Vulnerability Assessment & Penetration Testing for Mobile Apps
Protect Yourself From The Risk Of Cyber Attacks & Data Breaches, And Avoid 5-7 Figure Fines & Lawsuits With Our Vulnerability Assessment & Penetration Testing

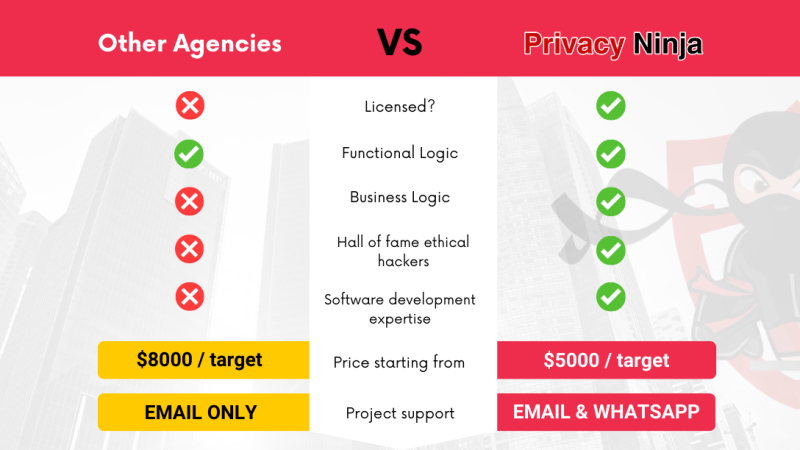
Why Work With Privacy Ninja?

Look at our track record
We founded Asia’s first bug bounty platform and have been keeping Organisations, MNCs and SMEs all over the world safe from cyber attacks and data breaches.
Large organisations like A*Star Research, Marché, E27, MightyJaxx, AlphaWave, Wallex, The Law Society of Singapore trust us with their cyber security.
Not one of the companies we’re working with have suffered a data breach after engaging us.

Our team is made up of the best penetration testers in the world
Our pentesters are hall of famers who have ethically hacked the most secure systems in the world like Microsoft, Google, Facebook etc.
As there’s nothing our pentesters haven’t seen, we complete our VAPT within 7 days of project commencement!

Despite being the best in Singapore, we’re the most affordable
We pride ourselves on being the best pen-testing provider in Singapore but are also 100% committed to being the most affordable.
If you find other licensed and registered penetration testing service provider who are cheaper than us, we’ll match the price.
Our Double Guarantee

Price Match Guarantee
Annual VAPT is mandatory for all networks, mobile, and web apps that store personal data in databases. We believe businesses shouldn't have to pay extra to stay compliant and avoid penalties. If you find a lower price with another licensed VAPT service provider, for the same scope of work or more, we'll match their price. Terms & Conditions apply.

Our Security Guarantee: Unlimited Revalidations Until You’re Fully Secure
We’re not just affordable — we’re trusted. None of our clients who used our VAPT services have ever been hacked, and we’re committed to keeping it that way. That’s why we offer a 1-Year Unlimited Revalidation Guarantee: unlimited revalidations for a full year after the initial test, at no extra cost. While others charge for revalidations , we don’t stop until your systems are completely secure. Because if we can’t help you stay protected, we don’t deserve your trust. Terms & Conditions apply.
As Featured In

Lian He Zao Bao
Bank Phishing

Channel 8
Dark Web

Interpol World
Cybersecurity

Channel 8
IoT Security
Affordability is one thing. A solid report is everything.
Complete Your Mobile Vulnerability Assessment & Penetration Testing with Privacy Ninja in 7 Days.

After the VAPT exercise, you will gain access to all findings in a detailed report that includes:
-
Overall findings summary
Vulnerabilities Identified & Confirmed
-
Explanations
-
Common Vulnerability Scoring System (CVSS) risk rating
-
Vulnerability impact
-
Affected Sources
Our Pentesting Certifications

Certified Ethical Hacker (CEH)

Offensive Security Certified Professional (OSCP)

Offensive Security Certified Professional (OSCP) Plus

CREST Certified Company

CREST Registered Penetration Tester (CRT)

CREST Certified Web Applications Tester (CCT App)

CREST Practitioner Security Analyst (CPSA)
CSRO License (Entity): Privacy Ninja Penetration Testing Service License No. CS/PTS/C-2022-0128R
Industries We Serve

How We've Helped Our Clients Identify Security Vulnerabilities

Digital Marketing Company
What we found:
HIGH:
- Fake user account creation with invalid mobile number – An attacker can create unlimited bogus/fake user accounts using automated scripts due to which the backend database will be overloaded with fake user accounts.
- Firebase database publicly exposed – An attacker can gain sensitive information about a user such as email id, username and token.
- Lack of binary protection – An attacker can use an automated tool to reverse engineer the code and modify it using malware to perform some hidden functionality.
- Application signed with a debug certificate – An attacker can debug the application activities/ communication and perform Man-in-the-Middle attack.
- SQL Injection – An attacker can supply SQL payloads in the user input field and dump the whole database containing all user’s sensitive data.
- And many more
Our Clients

Client Testimonials





In Your Mobile App VA, you’ll receive
🔴 Understand your requirements
🔴 Identify and advise what needs to be tested and what the testing should be focusing on
🔴 Generate and send over the quote in the same or next working day

