KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!



We founded Asia’s first bug bounty platform and have helped Organisations, MNCs, and SMEs worldwide stay safe from cyber-attacks and data breaches.
Major organisations like A*Star Research, Marché, E27, MightyJaxx, and AlphaWave trust us with their cyber security service.
Not one of the companies we’re working with has suffered a data breach after engaging with our cyber-security testing.

Our pen-testers are hall-of-fame security professionals who have ethically hacked the most secure operating systems in the world, like Microsoft, Google, Facebook, etc.
As there’s nothing our pen-testers haven’t seen, we complete our VAPT within 7 days of project commencement!

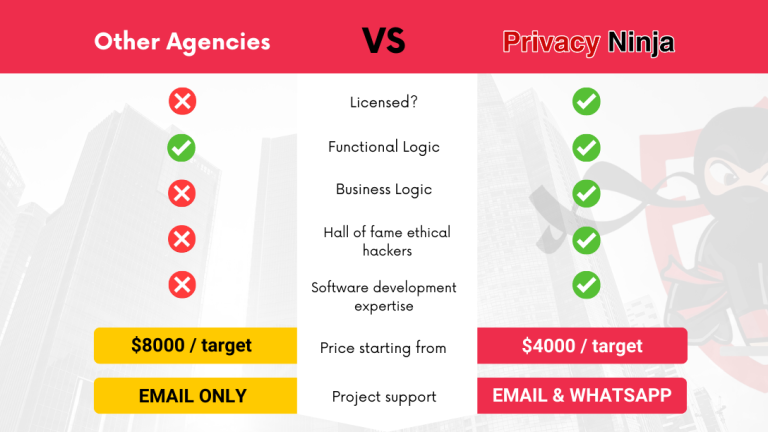
We pride ourselves on being the best pen-testing provider in Singapore but are also 100% committed to being the most affordable.
If you find other licensed and registered penetration testing service provider who are cheaper than us, we’ll beat the price by 20%.

Annual VAPT is mandatory for all networks, mobile, and web apps that store personal data in data bases. We believe businesses shouldn't have to pay extra to stay compliant and avoid penalties. If you find a lower price with another licensed VAPT service provider, for the same scope of work or more, we'll beat their price by 20%. Terms & Conditions apply.

We’re not just affordable — we’re trusted. None of our clients who used our VAPT services have ever been hacked, and we’re committed to keeping it that way. That’s why we offer a 1-Year Unlimited Revalidation Guarantee: unlimited revalidations for a full year after the initial test, at no extra cost. While others charge for revalidations , we don’t stop until your systems are completely secure. Because if we can’t help you stay protected, we don’t deserve your trust. Terms & Conditions apply.
Channel NewsAsia

Lian He Zao Bao

Channel 8

Interpol World

Channel 8

Overall findings summary
Itemised replicable steps/POC (Proof-of-concept)
Explanations
Common Vulnerability Scoring System (CVSS) risk rating
Vulnerability impact
Practical recommendations for remediation

Certified Ethical Hacker (CEH)

Offensive Security Certified Professional (OSCP)

Offensive Security Certified Professional (OSCP) Plus

CREST Certified Company

CREST Registered Penetration Tester (CRT)

CREST Certified Web Applications Tester (CCT App)

CREST Practitioner Security Analyst (CPSA)
CSRO License (Entity): Privacy Ninja Penetration Testing Service License No. CS/PTS/C-2022-0128R




Web Application
Penetration Testing
On-Prem & Cloud Network Penetration Testing

Mobile App
Penetration Testing

API
Penetration Testing

Smart Contract
Audit

Thick Client
Penetration Testing

Source Code
Review

What we found after penetration testing:
SQL Injection – An attacker can access and dump the whole database containing critical data using malicious SQL commands in user input fields.
Local File Inclusion (LFI) – An attacker can read sensitive files without any restriction by fooling the target system, gaining access to sensitive information, such as password files.
Stored Cross-Site Scripting (XSS) – An authenticated user can embed malicious JavaScript code in a page, which will be executed whenever a user accesses that page.
Malicious File Upload – An attacker can upload malicious executable files containing malicious content, like shell.php, to a computer system without any restriction, which might lead to remote code execution (RCE) attacks.
Broken Authorisation – An authenticated user can deactivate or delete job alerts of other users without any restriction.
Link Injection – Any authenticated user can embed malicious HTML tags such as the hyperlink <a> tag in a page, which may redirect users to a malicious website controlled by the attacker.
And many more.
SaaS
What we found after our penetration test:
Stored Cross-Site Scripting (XSS) – An authenticated user can embed malicious JavaScript code in a page, which will be executed whenever a user accesses that page.
Malicious File Upload – An attacker can upload malicious executable files containing malicious content to a computer system without any restriction, which might lead to other cyber-attacks such as insecure redirection, user account takeover, etc.
Host Header Injection – An attacker can redirect the users to a malicious web application controlled by the attacker and carry out various attacks such as session hijacking, malware download, etc.
HTML Injection – Any authenticated user can embed malicious HTML tags such as the hyperlink <a> tag in a page, which may redirect users to a malicious website controlled by the attacker.
And many more
Mobile Applications:

What we found after our penetration test:
Fake user account creation with invalid mobile numbers – An attacker can create unlimited bogus/fake user accounts using automated scripts, overloading the backend database.
Firebase database publicly exposed – An attacker can gain sensitive information about a user, such as an email ID, username and token.
Lack of binary protection – An attacker can use an automated tool to reverse engineer the code and modify it using malware to perform some hidden functionality.
Application signed with a debug certificate – An attacker can debug the application activities/communication and perform a Man-in-the-Middle attack.
SQL Injection – An attacker can supply SQL payloads in the user input field and dump the whole database containing all the user’s sensitive data.
And many more.
What we found after our penetration test:
Sensitive Information Disclosure – An attacker can gain remote access to user credentials or mobile application data without restriction and use them for authentication bypass or social engineering attacks.
Business Logical Flaw – A user can create a wallet with the wrong collection settings, which could lead to flaws in business logic while funding transactions.
Lack of binary protection – An attacker can use an automated tool to reverse engineer the code and modify it using malware to perform some hidden functionality.
Misconfiguration in Manifest/plist – An attacker can conduct a Man-in-the-Middle attack since application traffic is transmitted in clear text format.
Insecure Data Storage – An attacker can use the information stored in the app folder for further attacks, which may lead to user account takeover.
And many more.

What we found after our penetration test:
Default admin login on routers and VoIPs – An attacker can steal sensitive data by sniffing the traffic going through the routers/VoIPs and can implant its own exploit to compromise all other systems in the internal network.
Default admin login on biometric devices – An attacker can add, modify, and delete user accounts and related details from biometric devices without anyone’s knowledge.
Microsoft SMB EternalBlue Remote Code Execution – An attacker can take complete control over the server with SYSTEM security privileges and steal sensitive data or credentials of other logged-in users.
Malicious File Upload – An attacker can upload malicious executable files on the web server, which can get executed at the back end whenever a user accesses or views that particular file.
XMLRPC DOS Attack – An attacker can access the xmlrpc.php file without any authentication and conduct a DOS attack against the web server.
Synology DiskStation Manager(Multiple Possible Vulnerabilities) – An input validation error exists in the ‘externaldevices.cgi’ script that allows any administrative user to execute arbitrary commands with root privileges on the remote host.
Unsupported Windows OS – An attacker can conduct numerous exploits against outdated IIS servers, such as RCE, DoS, Buffer Overflow, Command Injection, etc.
And many more.
What we found after our penetration test:
Default admin login on POS printers – An attacker can add, modify, and delete the printer’s configuration without authorisation.
Default admin login on switches – An attacker can steal sensitive data by sniffing the traffic going through the switches or implant its own exploit to compromise all other systems present in the internal network.
Default admin login on biometric devices – An attacker can add, modify, and delete user accounts and related details from biometric devices without anyone’s knowledge.
Default admin login on UPS Network Management Card – An attacker can control NMC devices and attack other systems by changing the NMC configuration without restriction.
Microsoft SMB DOUBLEPULSAR Remote Code Execution – An attacker can take complete control over the server with SYSTEM security privileges and steal sensitive data or credentials of other logged-in users.
Microsoft RDP RCE (BlueKeep – CVE- 2019-0708) – An attacker can take complete control over the server through the RDP service and run arbitrary commands with administrator privileges.
Zerologon (CVE- 2020-1472) – An attacker can set an empty password for a domain user account and retrieve password hashes of all existing domain users.
Default community strings for SNMP service – An attacker can retrieve and modify sensitive information related to the device, such as device firmware versions, routing tables, network interfaces, and configuration details.
Unencrypted Telnet server – An attacker can eavesdrop on a Telnet session and obtain user credentials via a MiTM attack.
Outdated Apache Server – An attacker can conduct numerous exploits against outdated Apache servers, such as RCE, DoS, Buffer Overflow, Command Injection, etc.
Outdated VMware ESXI patches – An attacker with local administrative privileges on a virtual machine may exploit this issue to execute code as the virtual machine’s VMX process runs on the host.
Unsupported IIS version – An attacker can conduct numerous exploits against outdated IIS servers, such as RCE, DoS, Buffer Overflow, Command Injection, etc.
And many more.





Identify the most suitable type of security testing and assessment for your project so you do the right thing and don’t overpay for what you don’t need.
Receive detailed sample-related reports tailored to your project so you know what to expect and can ensure it’s something you understand and can act on.
Quotation with the only price-beat guarantee in the market, so you get the most affordable assessment on top of the best.

Established in 2018, Privacy Ninja is a Singapore-based IT security company specialising in data protection and cybersecurity solutions for businesses. We offer services like vulnerability assessments, penetration testing, and outsourced Data Protection Officer support, helping organisations comply with regulations and safeguard their data.
Singapore
7 Temasek Boulevard,
#12-07, Suntec Tower One,
Singapore 038987
Latest resources sent to your inbox weekly
© 2025 Privacy Ninja. All rights reserved
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!

Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!
