KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







An alert from the U.S. Federal Bureau of Investigation about Mamba ransomware reveals a weak spot in the encryption process that could help targeted organizations recover from the attack without paying the ransom.
The FBI warns that Mamba ransomware attacks have been directed at entities in the public and private sector, including local governments, transportation agencies, legal services, technology services, industrial, commercial, manufacturing, and construction businesses.
Mamba ransomware (a.k.a. HDDCryptor) relies on an open-source software solution named DiskCryptor to encrypt victim computers in the background with a key defined by the attacker.
Also Read: The DNC Registry Singapore: 5 Things You Must Know
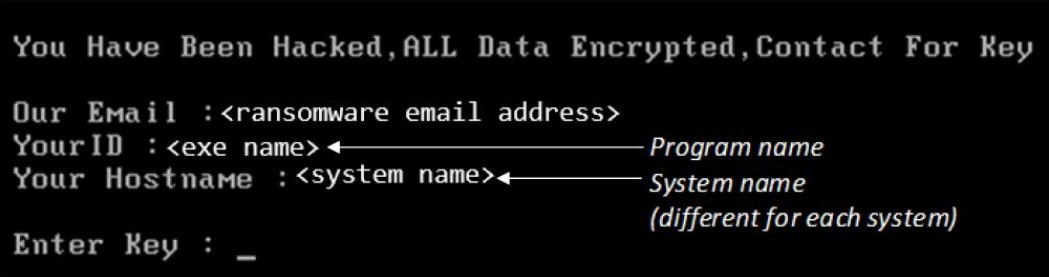
The FBI explains that installing DiskCryptor requires a system restart to add necessary drivers, which occurs with Mamba approximately two minutes after deploying the program.
The agency further notes that the encryption key and the shutdown time variable are stored in DiskCryptor’s configuration, a plaintext file named myConf.txt.
A second restart of the system happens once the encryption process completes, around two hours later, and the ransom note becomes available.
Because there is no protection around the encryption key, as it is saved in plaintext, the FBI says that this two-hour gap is an opportunity for organizations hit by Mamba ransomware to recover it.
“If any of the DiskCryptor files are detected, attempts should be made to determine if the myConf.txt is still accessible. If so, then the password can be recovered without paying the ransom. This opportunity is limited to the point in which the system reboots for the second time” – the FBI
The Mamba ransomware operation started to increase its activity with a new variant found in the second half of 2019. Despite not having an affiliate program, it was among the top threats.
In a report from Coveware, in the first quarter of last year Mamba was sitting in the top five ransomware threats led by REvil and Ryuk. This changed in the fourth quarter of 2020, although it continued to be a notable risk.
One peculiarity of Mamba ransomware is that it overwrite the disk’s master boot record (MBR), preventing access to encrypted files on the drive. This makes it more difficult to track the number of attacks since files cannot be analyzed through automated services like ID-Ransomware.
Also Read: How To Comply With PDPA: A Checklist For Businesses
The FBI provides the following details on artifacts that could help organizations detect a Mamba ransomware attack:
| Key Artifacts | |
| Files | Description |
| $dcsys$ | Located in the root of every encrypted drive [i.e. C:\$dcsys$] |
| C:\Users\Public\myLog.txt | Ransomware log file |
| C:\Users\Public\myConf.txt | Ransomware configuration file |
| C:\Users\Public\dcapi.dll | DiskCryptor software executable |
| C:\Users\Public\dcinst.exe | DiskCryptor software executable |
| C:\Users\Public\dccon.exe | DiskCryptor software executable |
| C:\Users\Public\dcrypt.sys | DiskCryptor software executable |
| C:\Windows\System32\Drivers\dcrypt.sys | Installed DiskCryptor driver |
| [Ransomware Filename].exe | Portable 32-bit .NET assembly compatible with 32-bit and 64-bit Windows systems which combines DiskCryptor with a simple ransom message upon boo |
| dcinst.exe | Cryptor installer support |
| dccon.exe | Console version od DiskCryptor |
| Services | |
| myCryptoraphyServiceRuns [Ransomware Filename].exe as a service and is removed once encryption is completed |