KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Almost $7 million worth of Bitcoin in a wallet controlled by DarkSide ransomware operators has been moved in what looks like a money laundering rollercoaster.
The funds have been moving to multiple new wallets since yesterday, a smaller amount being transferred with each transaction to make the money more difficult to track.
The timing aligns with the takedown of REvil ransomware infrastructure after hijacking the gang’s Tor hidden service as a result of an international law enforcement operation.
Also Read: Intrusion Into Privacy All About Law And Legal Definition
The DarkSide ransomware gang has extorted dozens of victims of tens of millions of U.S. dollars, their most famous attack being on May 7, against the largest fuel pipeline in the United States, Colonial Pipeline.
Omri Segev Moyal, the CEO and co-founder of cybersecurity company Profero, tweeted today that 107 bitcoins from a DarkSide wallet were moved to a new wallet.
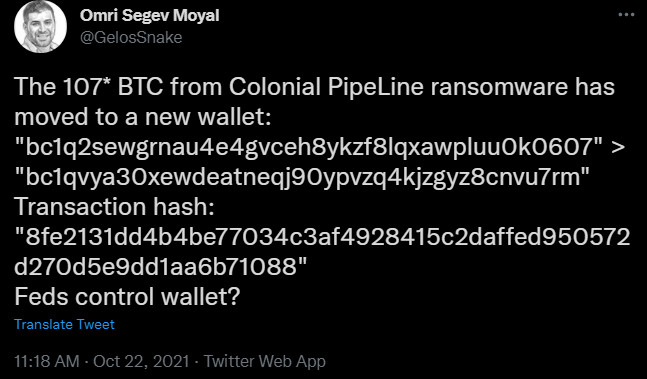
Looking at the transaction hash, the move started on October 21, 2021, at 7:05 AM (GMT) and the initial value was a little under $7 million.
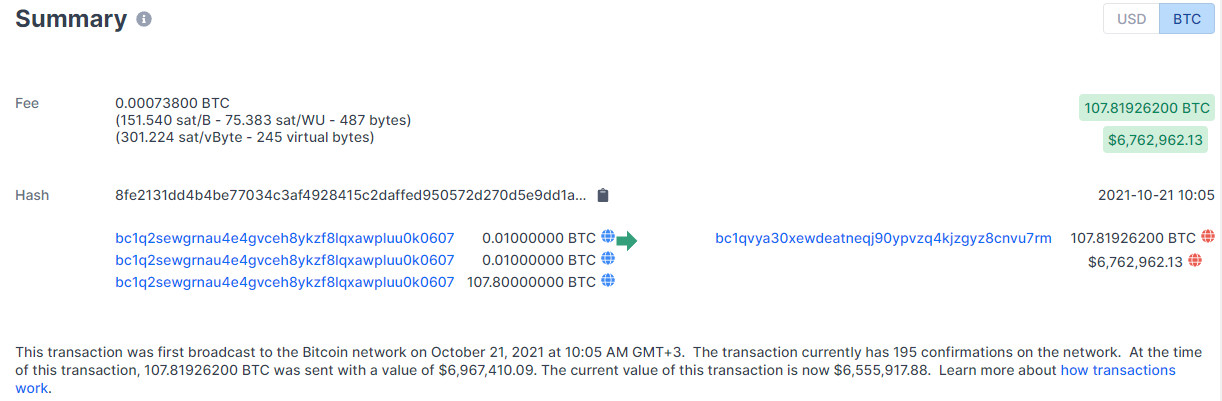
In a blog post today, blockchain analysis company Elliptic shows how DarkSide’s cryptocurrency flowed through different wallets, shrinking from 107.8 BTC to 38.1 BTC.

Moving the funds this way is a typical money laundering technique that hinders tracing and helps cybercriminals convert the cryptocurrency to fiat money.
Elliptic says that the process continues still and that small amounts of the money have already been transferred to known exchanges.
Moving the money at this time may be a result of what happened to the REvil ransomware operation, which shut down for a second time this year after finding that its services had been compromised by a third-party.
Also Read: New Data Protection Laws Australia: How Implementation Works
The hacking occurred after REvil attacked the Kaseya MSP platform that served more than 1,000 companies across the globe. While the FBI was on the verge of disrupting REvil, the cybercriminals shut down their operation.
When REvil restarted its business, they restored from the backups that had been infiltrated by the FBI before the gang closed shop.
DarkSide’s attack on Colonial Pipeline was the last one from DarkSide under this name. Until then, the ransomware gang had collected at least $90 million from its victims.
However, they chose their last target poorly, since its operations supplied petroleum products to markets and refineries on the U.S. East Coast accounting for 45% of all fuel consumed in the region.
Even if Colonial Pipeline paid the 75 BTC (around $5 million at the time) ransom, the consequences of the attack were too much for the DoJ not to treat it with top priority.
On June 7, the DoJ announced that it recovered 63.7 bitcoins of the ransom Colonial Pipeline paid to DarkSide to recover their systems as fast as possible.
DarkSide then exited the ransomware business only to emerge as BlackMatter. In July, the rebranded threat actor was looking to buy access to corporate networks.
Recorded Future announced at the time BlackMatter saying that it “incorporated in itself the best features of DarkSide, REvil, and LockBit.”
Under the new name, the ransomware actors continued to hit large companies such as medical technology giant Olympus, the New Cooperative farmers organization in the U.S., or Marketron provider of marketing services.
In a joint advisory released recently, CISA, the FBI, and the NSA provide mitigation information that can help organizations defend against BlackMatter ransomware attacks.