KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Google has finally rolled out an option on Android allowing users to disable 2G connections, which come with a host of privacy and security problems exploited by cell-site simulators.
The addition of the option was spotted by EFF (Electronic Frontier Foundation), which calls the development a victory for privacy protection.
A cell-site simulator, also known as “stingray” or IMSI Catcher, is a device that masquerades as a cell tower, forcing cell phones in their range to connect to it.
Also Read: 4 easy guides to data breach assessment
This connection enables the operators of these Stingrays to perform man-in-the-middle attacks and intercept sensitive personal information such as:
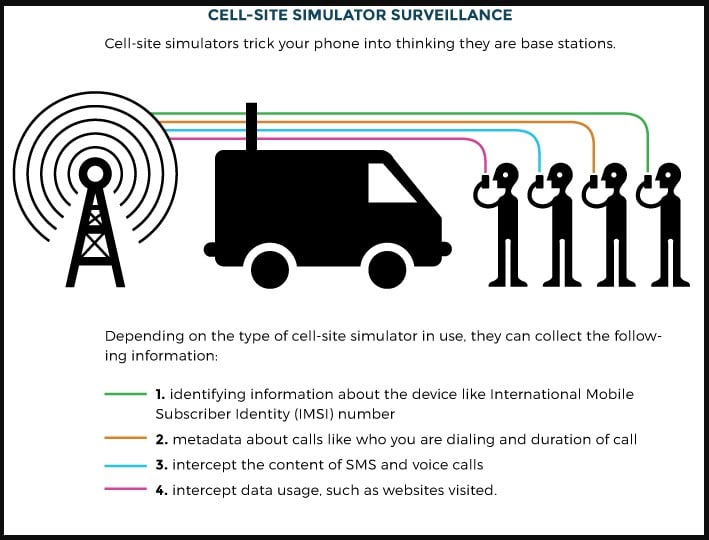
Unfortunately, this method of data interception has been repeatedly and indiscriminately deployed by law enforcement authorities during peaceful protests in otherwise democratic countries where strict data protection laws apply.
Moreover, documented cases of private deployment of “stingrays” have also been abundant in recent years, so the abuse of communication network vulnerabilities is widespread.
Most of these vulnerabilities have been addressed in 4G, but the simulated base stations have a way to downgrade nearby device connections to 2G, essentially laying the ground for exploiting old flaws.
Having a way to prevent this on the user end is a significant development, and while stopping 2G connections isn’t dealing with the entire spectrum of security problems, it certainly is a good start.
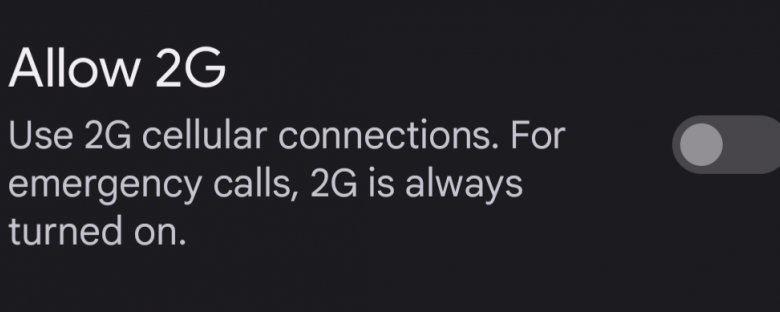
While Google has given Android users the option not to allow 2G cellular connections on their device, the setting is turned on by default.
If you want to turn it off, you can go to ‘Settings → Network & Internet → SIMs → Allow 2G’. Depending on your device maker and the Android skin used, the path to access that setting may be different.
Also Read: 7 Client Data Protection Tips to Keep Customers Safe
Note that this setting has only been made available on Android 12 for now. Bleeping Computer has tested Android 11 and Android 10, but the option is not yet available.
We have asked Google to clarify if there’s a hardware requirement too for this new option to work, and they told us that the modem needs to support the 1.6 Radio HAL, which is available only on newer devices.
Also, it’s important to clarify that 2G remains active as a backup for emergency calls no matter what position the toggle is set to, so there’s no way to disable it completely.
Finally, Apple hasn’t given iPhone users a choice to lock their devices to 4G/5G connectivity only, but now that Google has taken that step, it’s likely the competition follows.