KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







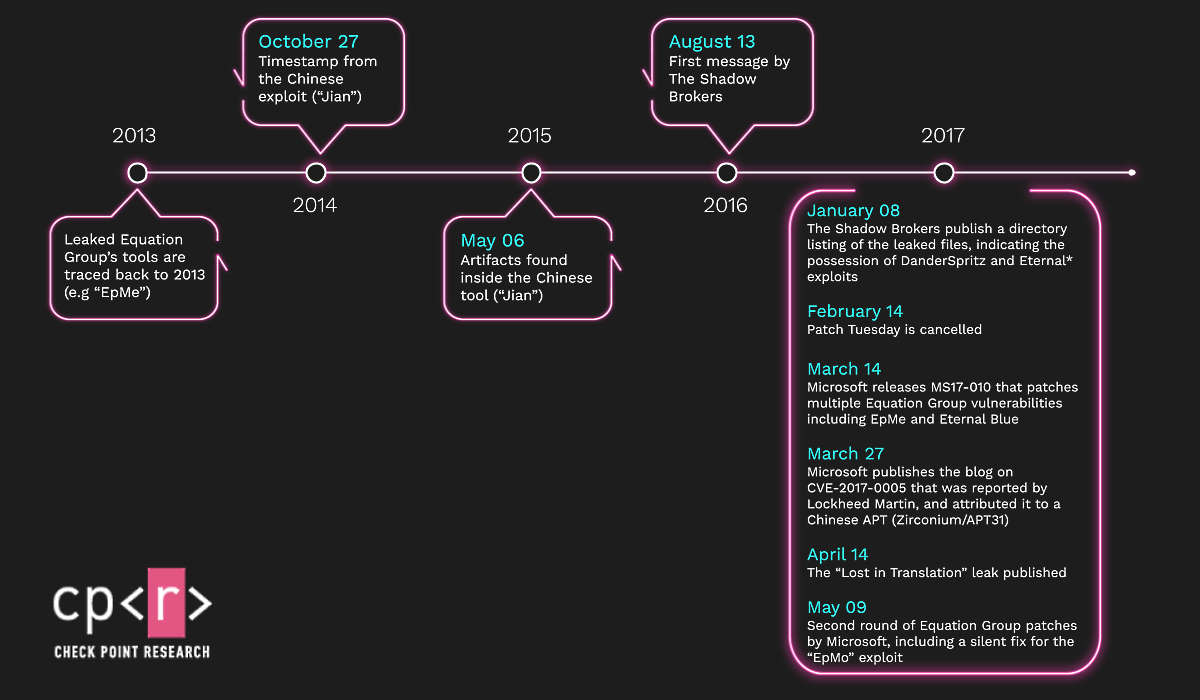
Chinese state hackers cloned and started using an NSA zero-day exploit almost three years before the Shadow Brokers hacker group publicly leaked it in April 2017.
EpMe is the original exploit created by Equation Group around 2013 for a Windows zero-day bug tracked as CVE-2017-2005.
The vulnerability was used for escalating Windows user privileges after gaining access to targeted devices since it’s a local privilege escalation (LPE) bug affecting devices running Windows XP up to Windows 8.
Microsoft patched this security bug in March 2017 and attributed active exploitation to the Chinese-backed APT31 hacking group.
However, APT 31 (also tracked as Zirconium) built their exploit, dubbed Jian, by replicating the functionality of the EpMe exploit stolen from the Equation Group (NSA’s Tailored Access Operations (TAO) unit) as Check Point researchers revealed in a report published today.
“To our surprise, we found out that this APT31 exploit is in fact a reconstructed version of an Equation Group exploit called ‘EpMe’,” Check Point said. “This means that an Equation Group exploit was eventually used by a Chinese-affiliated group, probably against American targets.”
Also Read: Key PDPA Amendments 2019/2020 You Should Know
This was made possible after the Chinese state hackers captured 32-bit and 64-bit samples of the Equation Group’s EpMe exploit.
Once replicated, the zero-day exploit was used by APT31 alongside other hacking tools in their arsenal, including the group’s multi-staged packer.
Microsoft patched the vulnerability Jian was designed to abuse only after Lockheed Martin’s IRT found an exploit sample in the wild and shared it with Microsoft.
While this isn’t the first case of a Chinese-backed APT group using Equation Group zero-days in their attacks, this is the first time Chinese cyberspies were able to get their hands on exploit samples and clone them for their own purposes.
“The first was when APT3 used their own version of EternalSynergy (called UPSynergy), after acquiring the Equation Group EternalRomance exploit,” Check Point added.
“However, in the UPSynergy case, the consensus among our group of security researchers as well as in Symantec was that the Chinese exploit was reconstructed from captured network traffic.”
As Check Point says, the APT31 operators could get their hands on the exploit samples themselves in all of their supported versions since Jian was assembled using the 32-bits and 64-bits versions of Equation Group’s exploit.
The APT31 hackers were thus able to get the Equation Group exploit samples in one of the following ways, according to Check Point:
“Fundamentally, our research is a demonstration of how one APT group is using the tools of another APT group for their own operations, making it harder for security researchers to perform accurate attribution of attacks, and showing how complex the reality behind these attacks truly is and how little we know,” Check Point Senior Security Researcher Itay Cohen said.
Also Read: The 5 Benefits Of Outsourcing Data Protection Officer Service
“Our hope is that our recent research technique of tracking exploited vulnerabilities could lead to new conclusions that have been under looked by the security industry up until now.”