KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Newly launched social site GETTR suffered a data breach after a hacker claimed to use an unsecured API to scrape the private information of almost 90,000 members and then shared the data on a hacking forum.
GETTR is a new pro-Trump social media platform created by former Trump advisor Jason Miller as an alternative to Twitter.
As first seen by Alon Gal, co-founder and CTO of cybersecurity firm Hudson Rock, a group of hackers found an unsecured application programming interface (API) that allowed them to scrape the data for 87,973 GETTR members.
After compiling the information, the data was published to a well-known hacking forum commonly used to share databases stolen during data breaches.
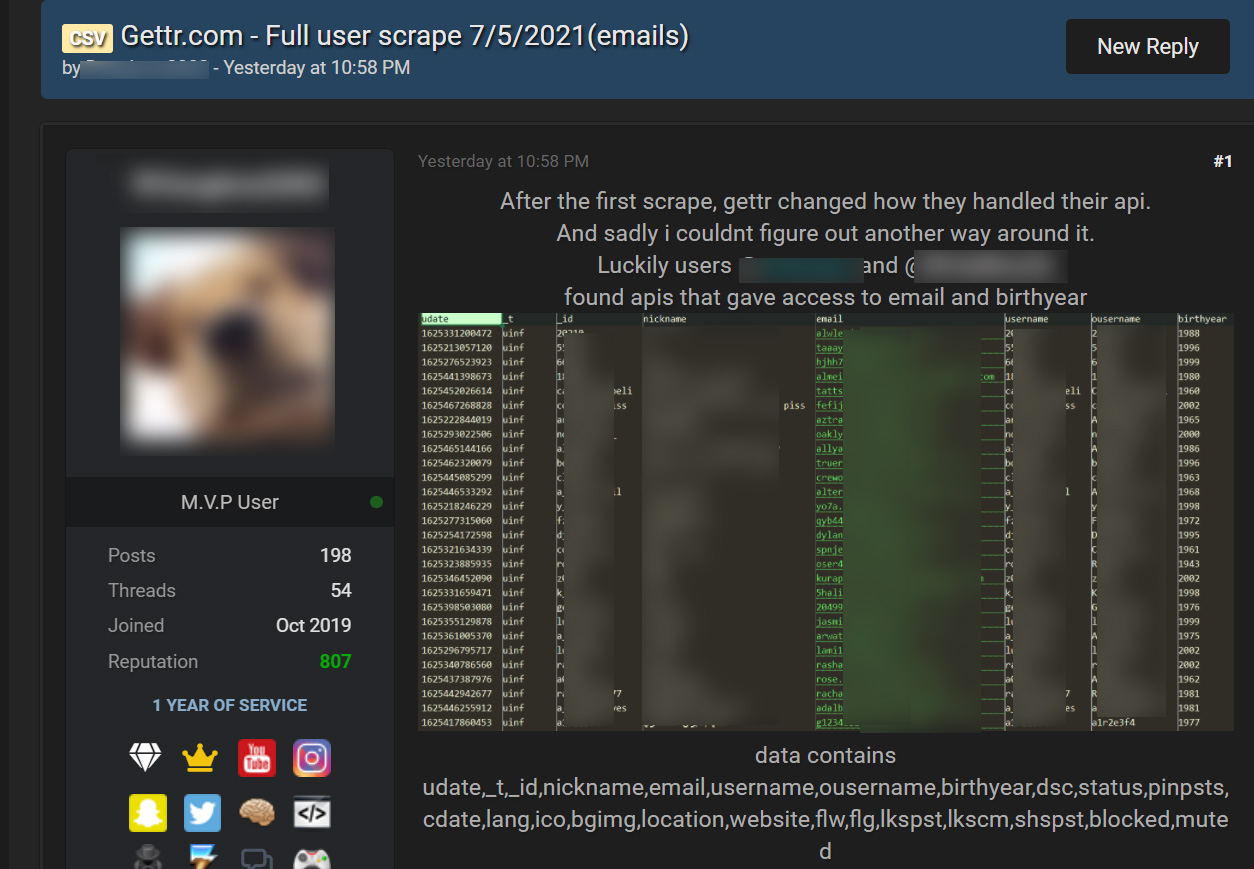
The hacker states that they first utilized an unsecured API to scrape public profile data of GETTR users, but it was later secured.
However, another member of the hacking forum found another unsecured API that allowed the scraping of public information and a member’s private email address and birth year.
From samples of the data seen by BleepingComputer, the scraped information includes a member’s email address, nickname, profile name, birth year, profile descriptions, avatar URL, background images, location, personal website, and other internal site data.
Also Read: PDPA Singapore Guidelines: 16 Key Concepts For Your Business
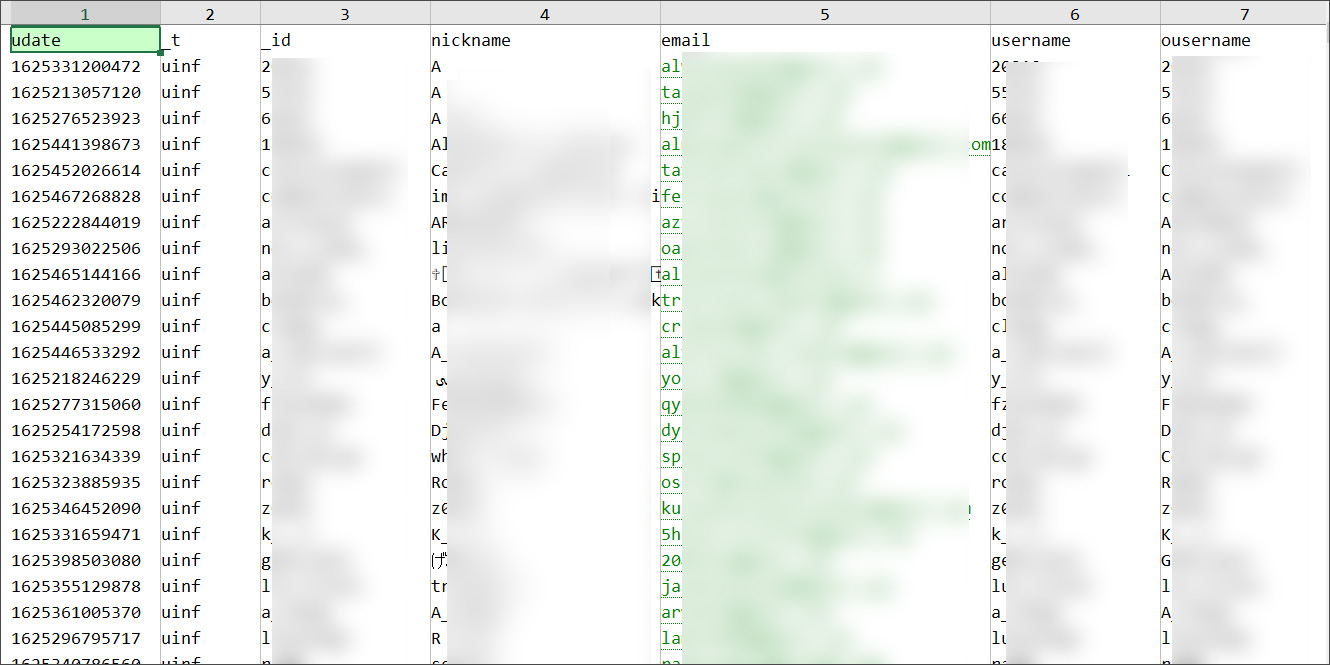
While much of the leaked information is readily available simply by visiting a GETTR user’s profile, a user’s email address, location, and birth year is not publicly available.
BleepingComputer confirmed that accounts exist from a random sampling of email addresses contained in the leaked data.
BleepingComputer has contacted GETTR regarding the leaked data but has not received a response.
While most of the leaked GETTR account information is publicly accessible, the email addresses, birth year, and locations are not meant to be accessible to other users.
Unfortunately, this type of information can be used by threat actors to perform targeted phishing attacks aimed at gathering further sensitive information, such as login passwords.
All GETTR users should be on the lookout for phishing emails pretending to be from GETTR, leading to a site asking you to log in.
Also Read: Data Protection Officer Singapore | 10 FAQs
If you receive these emails, you should immediately delete them and not enter your credentials.