KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Kaspersky researchers discovered a previously undocumented Windows PowerShell malware dubbed PowerPepper and developed by the hacker-for-hire group DeathStalker.
DeathStalker (previously known as Deceptikons) is a threat actor whose activity goes back to at least 2012 [1, 2] known for using a wide range of malware strains and complex delivery chains, as well as regularly using tactics that help them evade detection.
The group’s targeting has involved organizations and businesses from all over the world from finance companies to law offices, with no specific motivation, which led to its classification as a group of cyber-mercenaries.
DeathStalker is one of four hacker-for-hire groups exposed in 2020, together with BellTrox (also tracked as Dark Basin), Bahamut, and CostaRicto.
The new PowerPepper implant was discovered by Kaspersky in May 2020 while researching other attacks using the group’s other PowerShell-based implant known as Powersing.
Since its discovery, PowerPepper has been under constant development with new versions being deployed and its delivery chains being adapted to new targets.
This new malware is an in-memory Windows PowerShell-based backdoor that allows its operators to execute shell commands delivered remotely via a command-and-control (C2) server.
Also Read: Computer Misuse Act Singapore: The Truth And Its Offenses
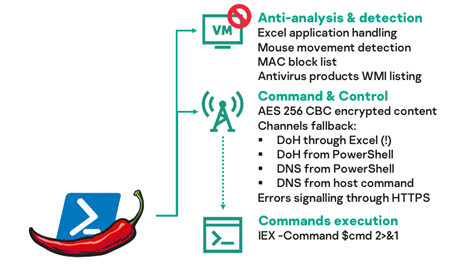
Its capabilities include several anti-detection tactics such as “mouse movements detection, client’s MAC addresses filtering, Excel application handling, and antivirus products inventory.”
The malware is delivered onto targets’ computers in the form of spear-phishing email malicious attachments or links that point to documents containing malicious Visual Basic for Application (VBA) macros that execute PowerPepper and gain persistence on infected systems.
“This infection chain varied slightly between July and November 2020: some dropped file names, integrated code or remote links changed, but the logic stayed the same,” Kaspersky Lab researcher Pierre Delcher explained.
Its macro-based and LNK-based delivery chains also have DeathStalker’s fingerprints on them with multiple obfuscation, execution, and masquerading tricks being employed to evade detection.
PowerPepper’s delivery chain evasion tricks include:
What stands out in its list of features is the way it communicates with its C2 server using Cloudflare responders via DNS over HTTPS (DoH) channels.
“PowerPepper first tries to leverage Microsoft’s Excel as a Web client to send DoH requests to a C2 server, but will fall back to PowerShell’s standard Web client, and ultimately to regular DNS communications, if messages cannot go through,” Delcher said.
The malware polls the C2 server for commands periodically using TXT-type DNS requests via DoH (or regular DNS when DoH fails) to the C2’s name servers.
The C2 server sends the encrypted commands to be executed embedded within a DNS response for targets validated via HTTPS after PowerPepper successfully starts on a compromised target.

“It only seems fair to write that DeathStalker tried hard to develop evasive, creative, and intricate tools with this PowerPepper implant and associated delivery chains,” Delcher concluded.
Also Read: Personal Data Websites: 3 Things That You Must Be Informed
“Nothing is specifically sophisticated in techniques and tricks that are leveraged, yet the whole toolset proven itself to be effective is pretty well put together, and shows determined efforts to compromise various targets around the world.”