KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Volatile Cedar, an advanced hacker group believed to be connected to the Lebanese Hezbollah Cyber Unit, has been silently attacking companies around the world in espionage operations.
The threat actor likely accessed more than 250 Oracle and Atlassian servers belonging mainly to organizations providing mobile communications and internet-based services.
Also known as Lebanese Cedar, the actor has been active since at least 2012 but fell of the researchers’ radar in 2015. Their operations resurfaced in early 2020 with what security researchers call the BeardStache global campaign, which may have compromised hundreds of companies.
In a report today, cybersecurity company ClearSky says that Lebanese Cedar seems to focus on collecting intelligence and stealing company databases with sensitive information – such as client call records and private data in the case of telecommunications companies.
Also Read: What Legislation Exists in Singapore Regarding Data Protection and Security?
According to the researchers, the threat actor makes reconnaissance efforts to select their victims and relies on public tools to find them. They use URI Brute Force tools (GoBuster and DirBuster) to look for open directories that could allow a web shell injection.
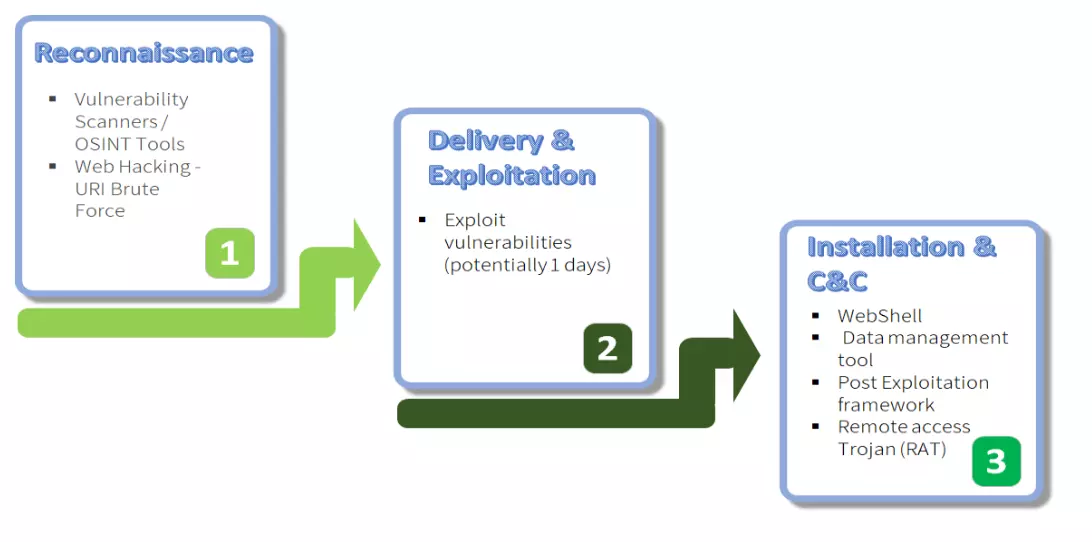
Lebanese Cedar looks for unpatched Atlassian Confluence, Atlassian Jira, and Oracle Fusion Middleware servers. The vulnerabilities exploited are CVE-2019-3396, CVE-2019-11581, and CVE-2012-3152.
The geography of the latest batch of victims varies from the Middle East to America and Europe, comprising the United States, the United Kingdom, Egypt, Saudi Arabia, Jordan, United Arab Emirates, and the Palestinian National Authority.
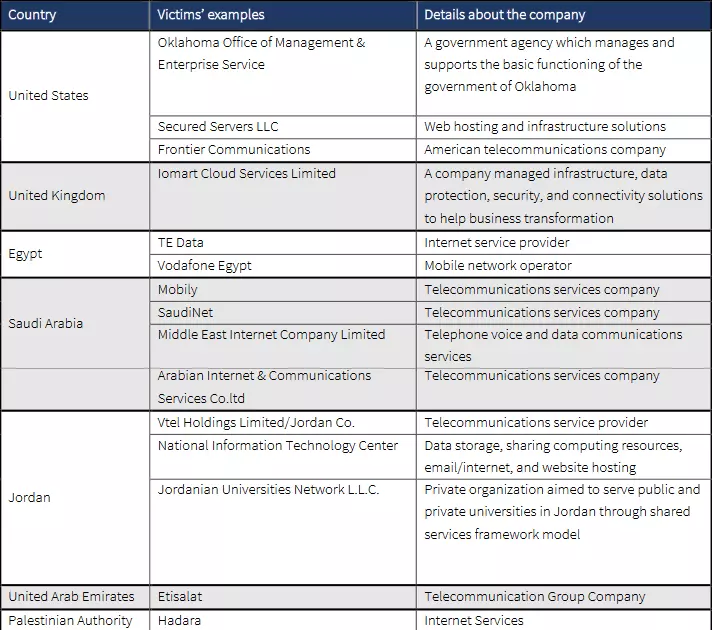
ClearSky says that the group may have been active over the past five years but its operations remained unnoticed due to adopting new tactics, techniques, and procedures.
According to the security firm, Lebanese Cedar was able to keep a low profile by:
The researchers started to investigate after finding suspicious network activities and hacking tools on the systems of multiple companies. A closer look revealed a new version of the Explosive RAT – a remote access tool linked to Volatile Cedar – and the the “Caterpillar” web shell.
Also Read: Letter of Consent MOM: Getting the Details Right
“’Caterpillar WebShell’ was found in most of the victims we investigated, in many of the systems we also found traces of “Explosive” RAT. We identified the specific open-source JSP file browser that was modified for the hackers’ purposes. We found that Lebanese Cedar deployed the payload of Explosive RAT into the victims’ network. Lebanese Cedar is the only known threat actor that uses this code” – ClearSky
During incident response engagements, the company found two JSP files on victims’ servers, added on various dates between January 2019 and August 2020. The files had been installed at the same time on multiple ports that redirect to an Oracle server.
ClearSky warns that the Oracle servers accessed by Lebanese Cedar are still open and are easy targets for other hackers looking to attack the networks of multiple telecom providers or gain access to the files available.
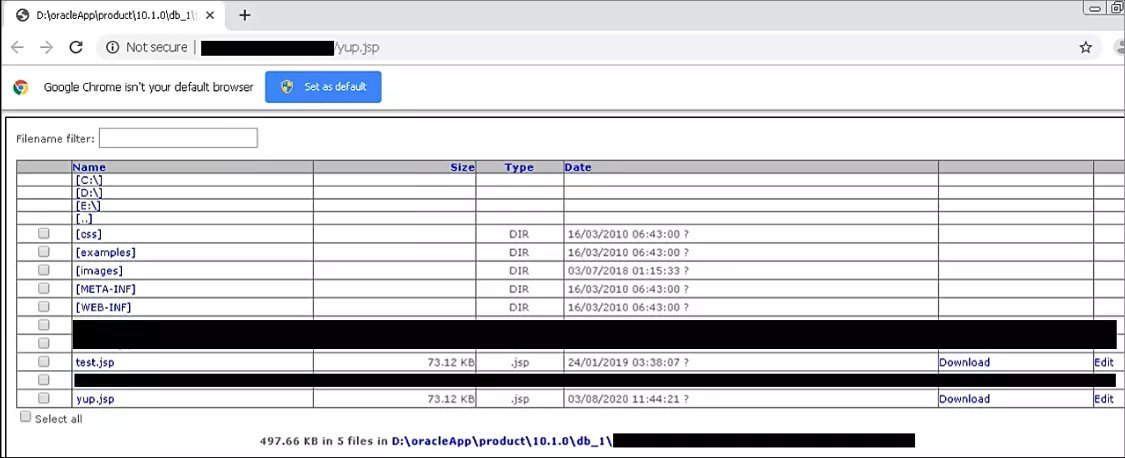
The researchers say that Lebanese Cedar combines open-source tools with custom ones, their current toolset including a full blown web shell, a custom RAT, and “carefully selected complementary tools, including URI brute force tools.”
ClearSky describes Lebanese Cedar as an actor that has the capability to develop their tools and orchestrate “sophisticated, well-designed attacks” without drawing attention to their operations. The clever selection of tools, tactics, and attack vectors allows them to pass unnoticed.
The company’s report provides complete technical details about the attacks investigated and indicators of compromise that include some of the original servers used by the hackers.