KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







LockBit is the latest ransomware gang whose Linux encryptor has been discovered to be focusing on the encryption of VMware ESXi virtual machines.
The enterprise is increasingly moving to virtual machines to save computer resources, consolidate servers, and for easier backups.
Due to this, ransomware gangs have evolved their tactics to create Linux encryptors that specifically target the popular VMware vSphere and ESXi virtualization platforms over the past year.
Also Read: Computer Misuse Act Singapore: The Truth And Its Offenses
While ESXi is not strictly Linux, it does share many of its characteristics, including the ability to run ELF64 Linux executables.
In October, LockBit began promoting the new features of their Ransomware-as-a-Service operation on the RAMP hacking forums, including a new Linux encryptor that targets VMware ESXi virtual machines.
In a new report, Trend Micro researchers analyzed the ransomware gang’s Linux encryptor and explained how it’s used to target VMWare ESXi and vCenter installations.
Linux encryptors are nothing new, with BleepingComputer reporting on similar encryptors in the past from HelloKitty, BlackMatter, REvil, AvosLocker, and the Hive ransomware operations.
Like other Linux encryptors, LockBits provides a command-line interface allowing affiliates to enable and disable various features to tailor their attacks.
These features include the ability to specify how large a file and how many bytes to encrypt, whether to stop running virtual machines, or wipe free space after, as shown by the image below.
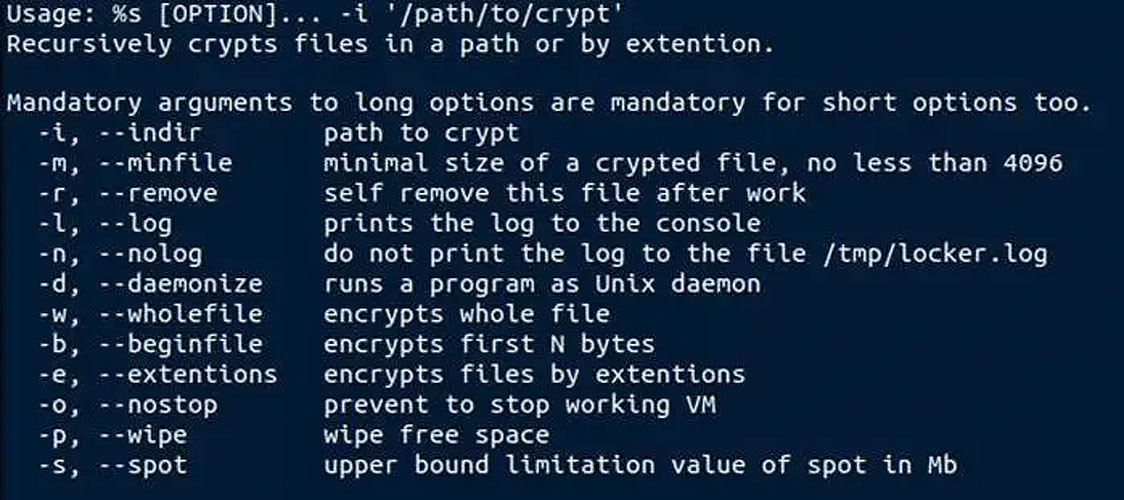
However, what makes the LockBit linux encryptor stand out is the wide use of both VMware ESXI and VMware vCenter command-line utilities to check what virtual machines are running and to shut them down cleanly so they are not corrupted while being encrypted.
Also Read: Personal Data Websites: 3 Things That You Must Be Informed
The full list of commands seen by Trend Micro in LockBit’s encryptor are listed below:
| Command | Description |
|---|---|
| vm-support –listvms | Obtain a list of all registered and running VMs |
| esxcli vm process list | Get a list of running VMs |
| esxcli vm process kill –type force –world-id | Power off the VM from the list |
| esxcli storage filesystem list | Check the status of data storage |
| /sbin/vmdumper %d suspend_v | Suspend VM |
| vim-cmd hostsvc/enable_ssh | Enable SSH |
| vim-cmd hostsvc/autostartmanager/enable_autostart false | Disable autostart |
| vim-cmd hostsvc/hostsummary grep cpuModel | Determine ESXi CPU model |
Trend Micro states that the encryptor uses AES to encrypt files and elliptic-curve cryptography (ECC) algorithms to encrypt the decryption keys.
With the widespread use of VMware ESXI in the enterprise, all network defenders and security professional should expect that every large ransomware operation has already developed a Linux variant.
By making this assumption, admins and security professionals can create appropriate defenses and plans to protect all devices in their networks, rather than just Windows devices.
This is especially true for the LockBit operation, which has become the most prominent ransomware operation since REvil shut down and prides itself on its encryptors’ speed and feature set.
It is also vital to remember that as much as we are watching ransomware gangs, they are also watching us back.
This means that they monitor researchers’ and journalists’ social feeds for the latest tactics, defenses, and vulnerabilities that they can then use against corporate targets.
Due to this, ransomware gangs are constantly evolving their encryptions and tactics to try and stay one step ahead of security and Windows admins.