KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Cerber ransomware is back, as a new ransomware family adopts the old name and targets Atlassian Confluence and GitLab servers using remote code execution vulnerabilities.
As ransomware began picking up pace in 2016, a new Cerber ransomware operation emerged that quickly became one of the most prolific gangs at the time. However, its activity slowly tapered off until it disappeared at the end of 2019.
Starting last month, a ransomware called Cerber once again reared its ugly head, as it began infecting victims worldwide with both a Windows and Linux encryptor
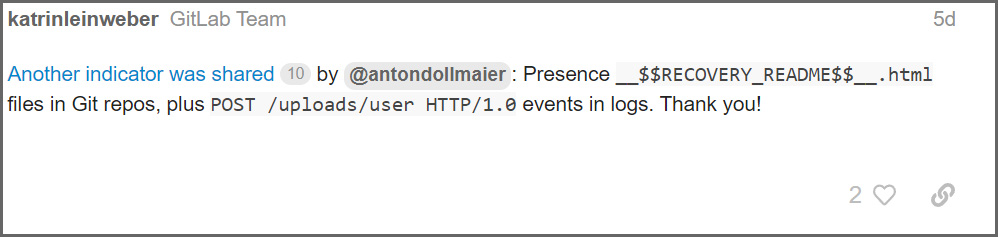
The new version of Cerber is creating ransom notes named __$$RECOVERY_README$$__.html and appending the .locked extension to encrypted files.
From the victims seen by BleepingComputer, the new Cerber ransomware gang is demanding ransoms ranging from $1,000 to $3,000.
Also Read: How PII Data Works In Businesses And Its Advantages
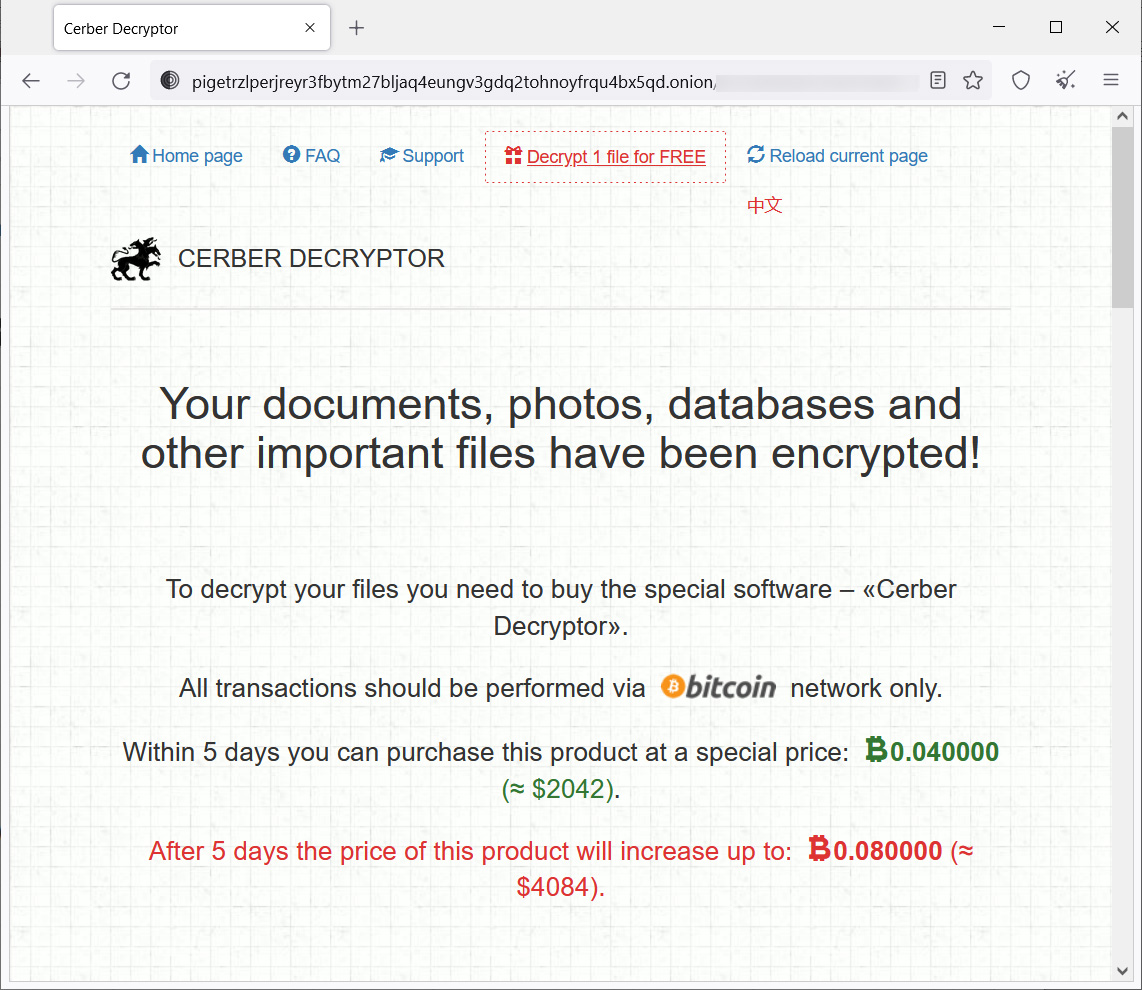
Emsisoft CTO and ransomware expert Fabian Wosar examined the new variant and said it does not match the code of the older family. In particular, the new version uses the Crypto+++ library, while the older variant used Windows CryptoAPI libraries.
These code differences and the fact that the original Cerber did not have a Linux variant lead us to believe that a new threat actor has adopted the name, ransom note, and Tor payment site, and is not the original operation.
This week, security researchers and vendors have seen the new Cerber ransomware operation hacking servers using remote code execution vulnerabilities in Atlassian Confluence and GitLab.
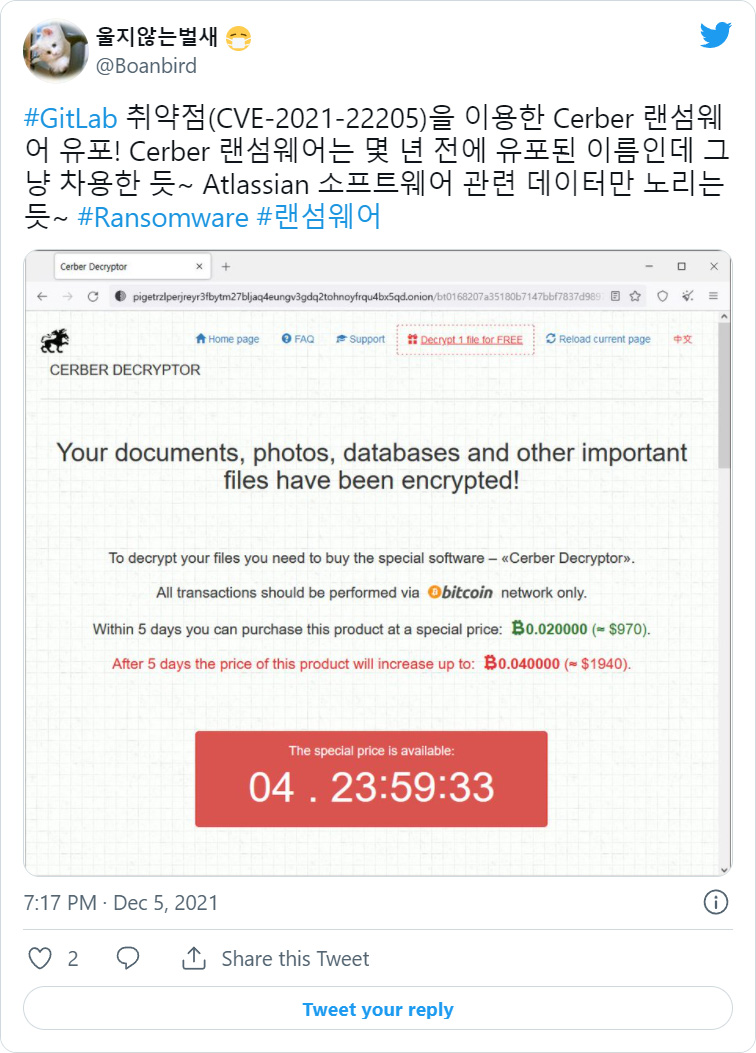
Security researcher BoanBird shared a sample of the new Cerber ransomware with BleepingComputer which shows this new strain specifically targets the Atlassian Confluence folders listed below.
C:\Program Files\Atlassian\Application Data
C:\Program Files\Atlassian\Application Data\Confluence
C:\Program Files\Atlassian\Application Data\Confluence\backupsBoanBird also shared a link to the GitLab forums where admins disclosed that Cerber exploits a recently disclosed vulnerability in GitLab’s ExifTool component.
Also Read: How To Check Data Breach And How Can We Prevent It
These vulnerabilities are tracked as CVE-2021-26084 (Confluence) and CVE-2021-22205 (GitLab) and can be exploited remotely without authentication. Additionally, both vulnerabilities have publicly disclosed proof-of-concept (PoC) exploits, allowing attackers to breach servers easily.
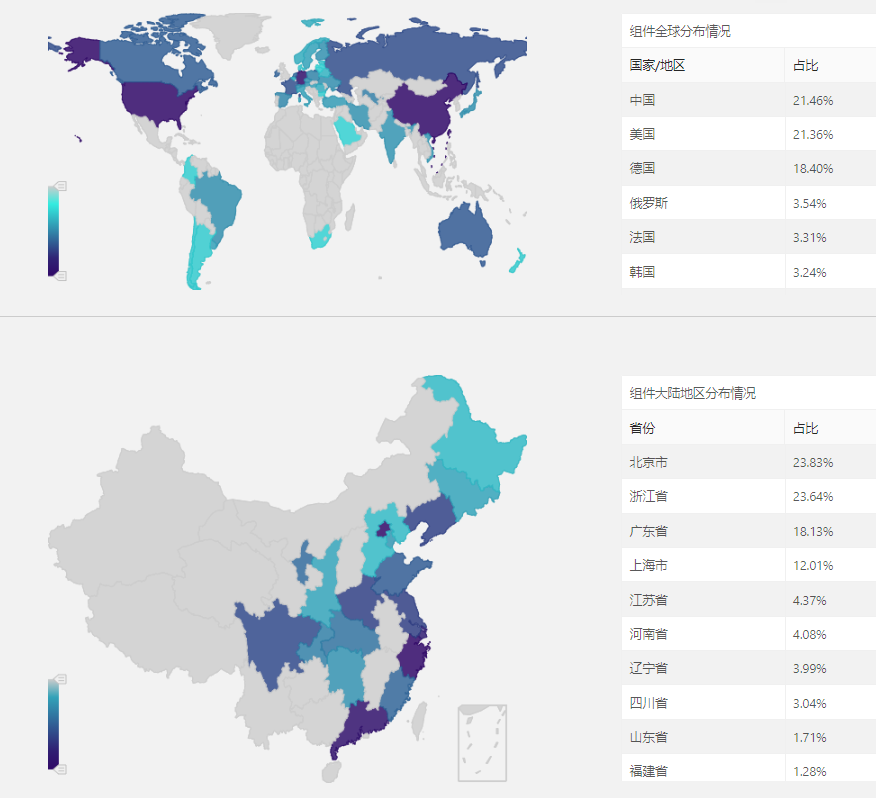
A report released this week by researchers at Tencent shows that attacks deploying the new Cerber ransomware are mostly targeting the United States, Germany, and China.
Although the previous version of Cerber excluded targets in the CIS (Commonwealth of Independent States), Tencent’s telemetry data from the recent attacks shows otherwise. Furthermore, BleepingComputer has also independently confirmed multiple victims in Russia, indicating that these threat actors are indiscriminate in who they target.
At this time, the best approach to protect against Cerber would be to apply the available security updates for Atlassian Confluence and GitLab.
However, as more servers are patched, we should expect the threat actors to target other vulnerabilities to breach servers.