KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







A new phishing campaign has been targeting verified Twitter accounts, as seen by BleepingComputer.
Verified accounts on Twitter refer to those possessing a blue badge with a checkmark. These accounts typically represent notable influencers, prominent celebrities, politicians, journalists, activists, as well as government and private organizations.
The phishing campaign follows Twitter’s recent removal of the checkmarks from a number of verified accounts, citing that these were ineligible for the legendary status, and were verified in error.
Also Read: When to Appoint a Data Protection Officer
Over the weekend, BleepingComputer came across a phishing campaign aimed at verified Twitter users.
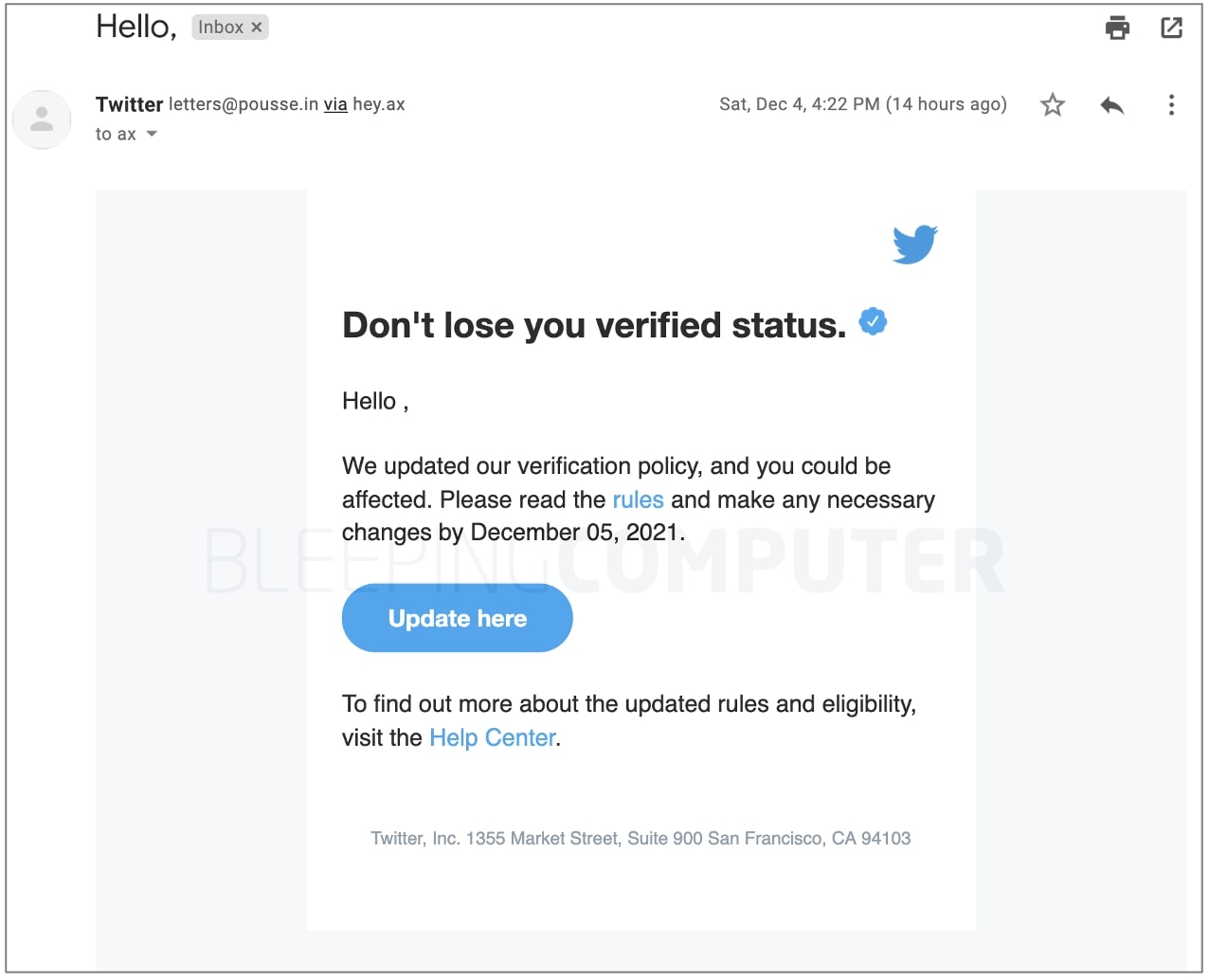
The phishing email shown below urges the Twitter user to “update” their details so as to not risk losing their verified status. Note, the email successfully made it past Gmail’s spam filters:
These emails are being sent at a time when Twitter is inexplicably removing the “blue tick” verified status from a number of notable accounts, such as that of the English television presenter, producer, and Heart Radio’s national breakfast show host, Jamie Theakston:
So @Twitter has removed my blue tick verification because they can’t be sure I’m me. Fair enough, some days I’m not entirely sure myself…— Jamie Theakston (@JamieTheakston) December 2, 2021
The Twitter account of Bloxy News with its 556,000+ followers is yet another example that was presented with a generic message as the reason behind revoked verification status.
Unsurprisingly, Twitter’s ongoing takedown of blue badges has ruffled many feathers on Twitterverse as accounts endorsed with the blue badge are often perceived as distinguished, notable, and expected to lead by example—at least that’s what Twitter tells you after verifying you:”As you know, a verified badge tells people that your account is notable and authentic. And being a part of this ‘blue badge’ Twitter community comes with responsibility. We hope you use it well. (Serious voice) All accounts, including verified accounts, need to follow the Twitter Rules.”
“To keep your verified status, please keep in mind that your Twitter account must always be complete. This means having either a verified email address or phone number, a profile image, and a display name. Any verified account in severe or repeated violation of our rules may lose their blue badge.”
A CEO left Twitter and now all of sudden ppl getting they verification badges snatched up??? Like WTF! pic.twitter.com/iW0Cr8sARq— JOURDON (@DynamoSuperX) December 1, 2021
Some took notice that the timing of Twitter’s en-masse blue badge takedown coincides with changes in the executive leadership—after former Twitter CEO Jack Dorsey resigned and handed on the torch to CTO Parag Agrawal.
Also Read: 4 Things to Know When Installing CCTVs Legally
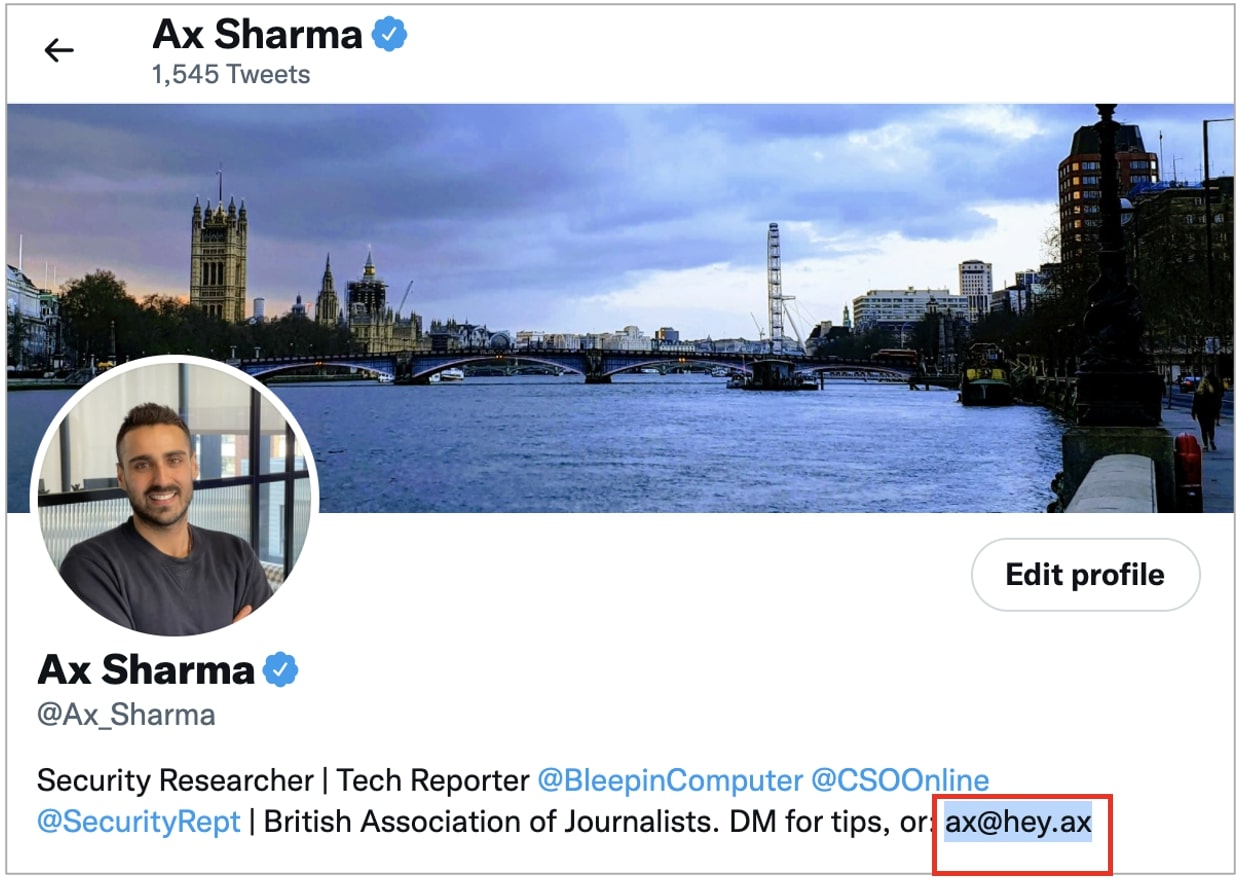
The phishing email discovered by BleepingComputer is sent to verified users, many of whom may choose to list an email address in their bio for business reasons.
At least in my case, the phishing message arrived at the email address listed in my public Twitter bio rather than the one associated with my Twitter account:
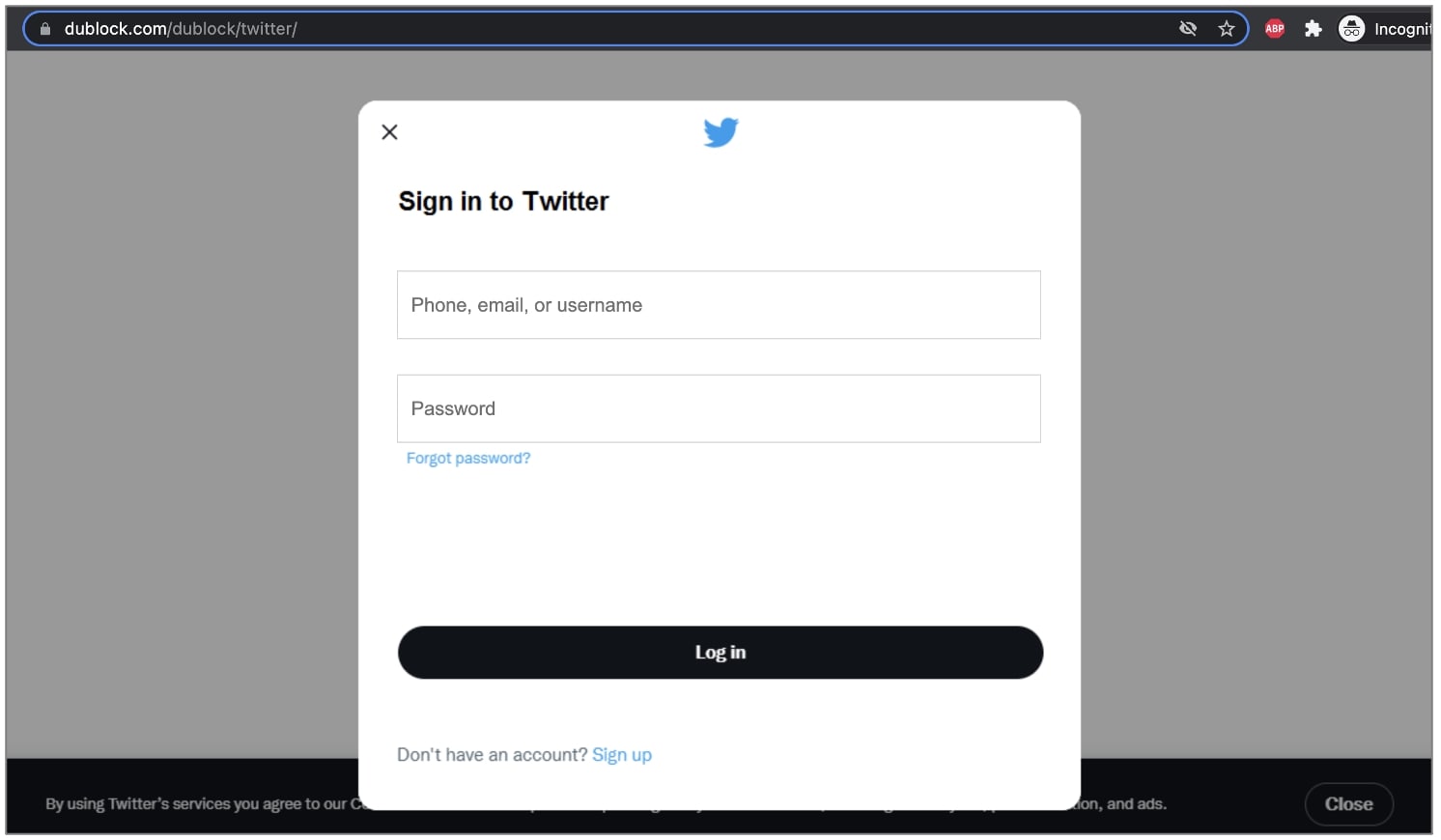
The phishing message first entices the user to tap the “Update here” button.
The button links to https://www.cleancredit[.]in/wp-content/uploads/2021/12/index.html which further redirects the user to a page living at: https://dublock[.]com/dublock/twitter/
It appears both of these websites have been compromised and being abused by the attackers to host phishing pages:
After entering Twitter credentials, that the form poorly validates, the user is prompted to also provide the two-factor authentication code sent to them:
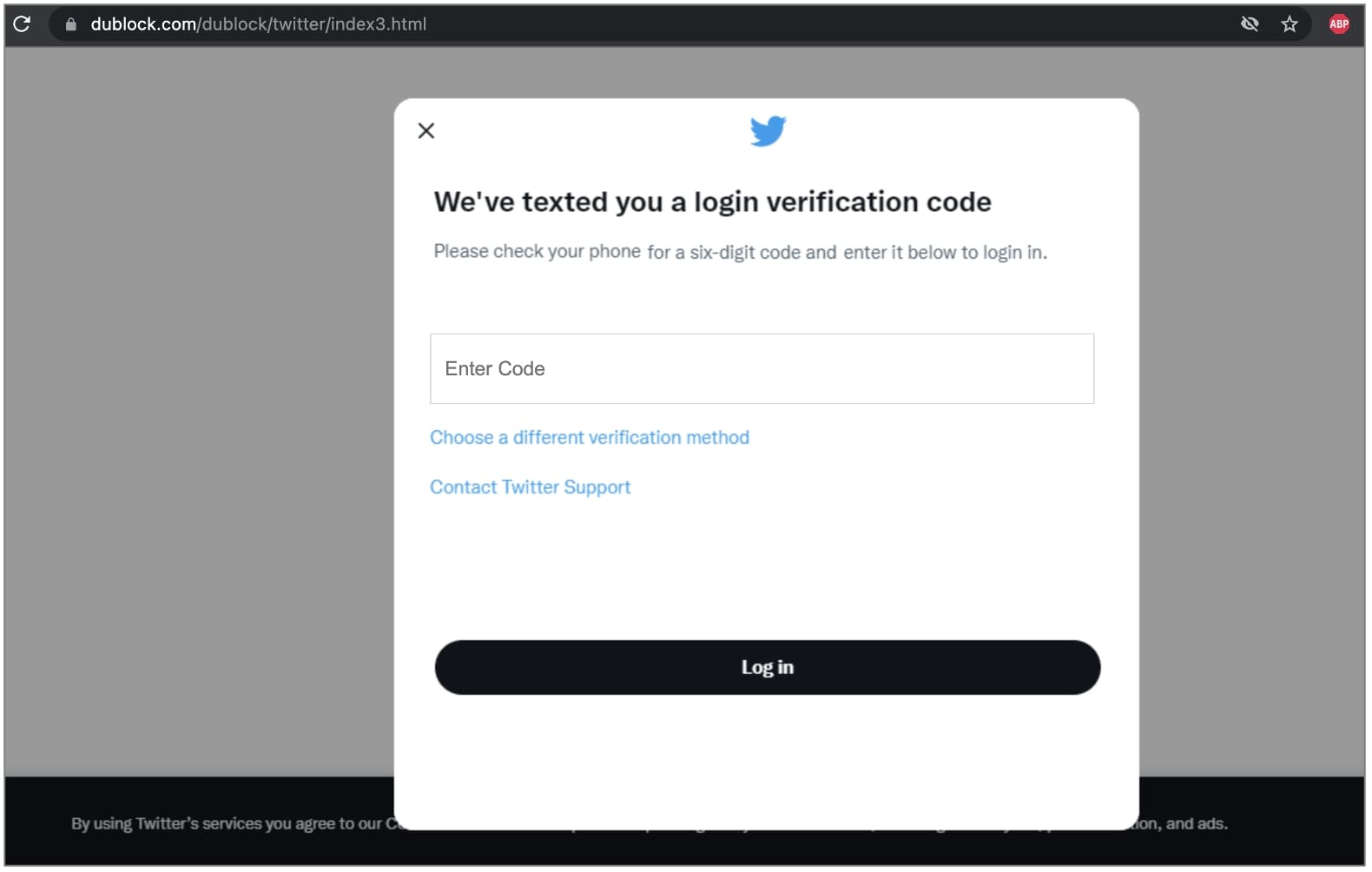
After gathering the user’s Twitter username, password, and two-factor authentication code, the phishing page redirects the user to the Twitter homepage.
Twitter users, verified or not, should be wary of such phishing emails and refrain from opening any links or attachments within.