KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







A new phishing campaign using fake shipping delivery lures installs the STRRAT remote access trojan on unsuspecting victim’s devices.
Fortinet discovered the new campaign after spotting phishing emails impersonating Maersk Shipping, a giant in the global shipping industry, and using seemingly legitimate email addresses.
If the recipient opens the attached document, the macro code that runs fetches the STRRAT malware onto their machine, a powerful remote access trojan that can steal information and even fake ransomware attacks.
Also Read: 4 Reasons to Outsource Penetration Testing Services
As seen in the header information of the phishing emails, the messages are routed through recently registered domains that increase the risk of being flagged by email security solutions.
The email claims to be information about a shipment, changes in delivery dates, or notices regarding a fictitious purchase and includes an Excel attachment or links to one that pretends to be the related invoice.
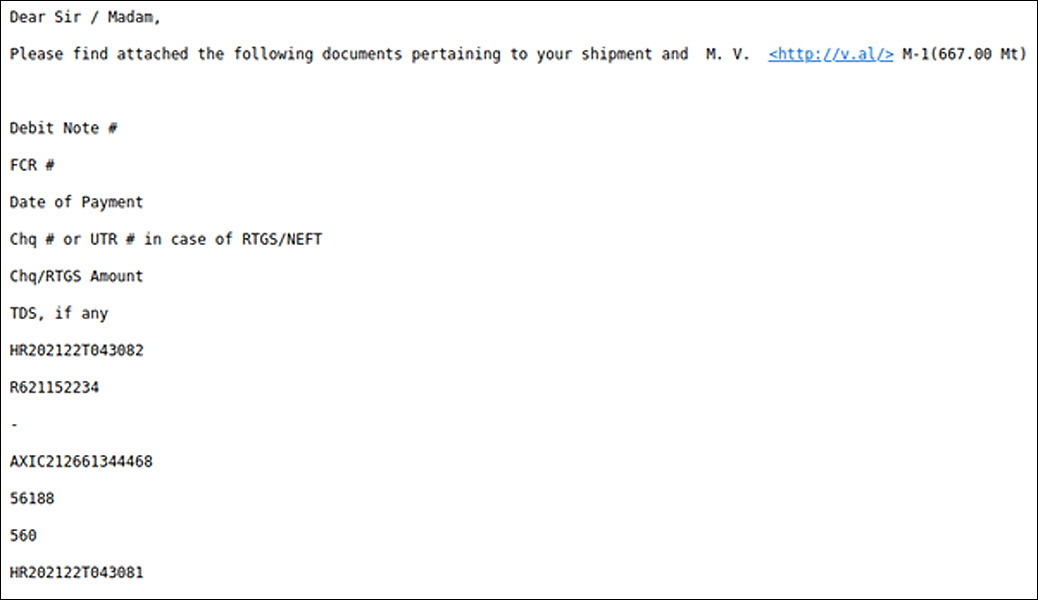
In some cases, Fortinet’s analysts sampled emails that carried ZIP files that contained the STRRAT malware, so no intermediate dropper in the form of a document was used.
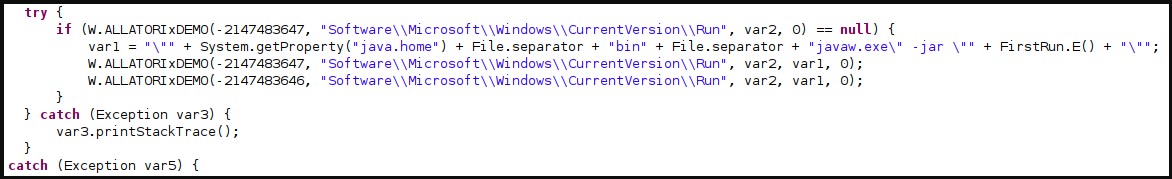
The actors have obfuscated the contained packages by using the Allatori tool to evade detection from security products.
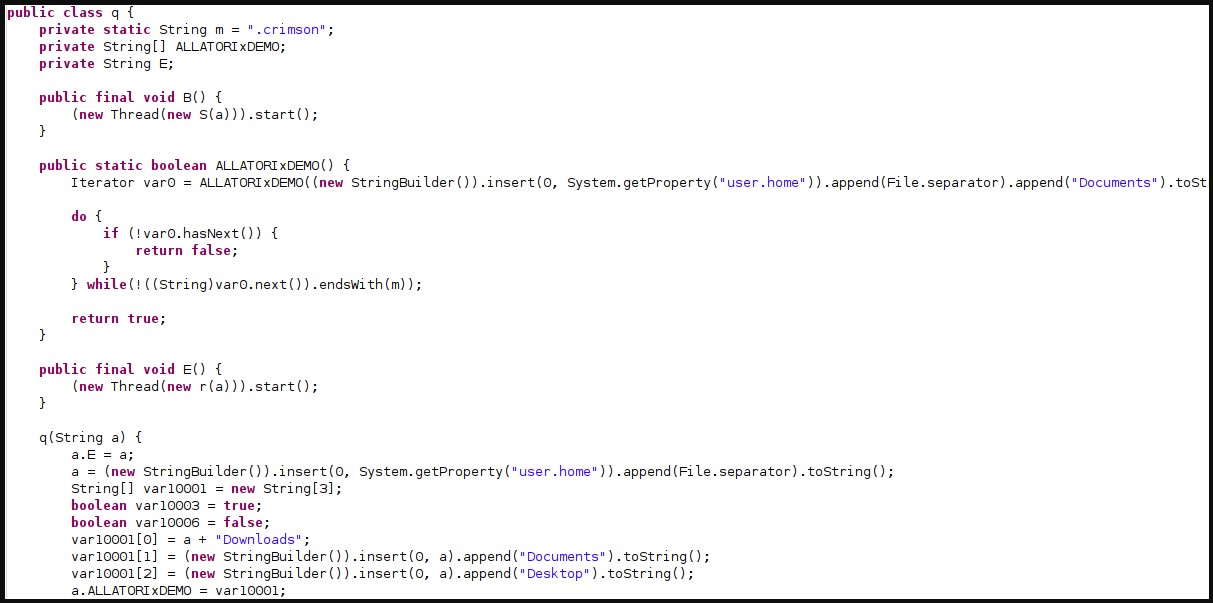
The STRRAT infection begins by decrypting the configuration file, copying the malware into a new directory, and adding new Windows registry entries for persistence.
STRRAT malware first gathers basic information on the host system like the architecture and any anti-virus tools running on it and checks local storage and network capability.
Also Read: Vulnerability Assessment vs Penetration Testing: And Why You Need Both
In terms of its functionality, STRRAT can perform the following:
This last part is interesting because no files are encrypted in the fake ransomware attack. As such, it’s most likely used to divert the victim’s attention away from the real problem, which is the exfiltration of data.
However, considering that this module essentially blows the cover of STRRAT, its presence and deployment is somewhat contradictory.
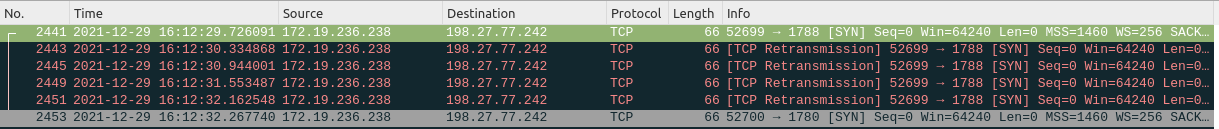
Finally, the malware’s communication method isn’t very well optimized for stealthiness either.
“Examining that traffic in Wireshark shows STRRAT being exceptionally noisy. This is likely due to the C2 channel being offline at the time of the investigation,” explains Fortinet’s report
“In its effort to obtain further instructions, the sample attempts to communicate over port 1780 and 1788 at one-second intervals, if not more in some instances.”
Trojans like STRRAT often go ignored for being less sophisticated and more randomly deployed. However, this phishing campaign demonstrates that lesser threats in circulation can still deliver damaging blows to companies.
The phishing emails used in this campaign blend very homogeneously with day-to-day corporate communications in companies that deal with shipments and transportation, so it only takes a tired or careless employee for the damage to be done.