KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Pulse Secure has fixed a zero-day vulnerability in the Pulse Connect Secure (PCS) SSL VPN appliance that is being actively exploited to compromise the internal networks of defense firms and govt agencies.
Last week, cybersecurity firm FireEye revealed that threat actors actively exploited the zero-day vulnerability, tracked as CVE-2021-22893, to deploy malware on Pulse Secure devices to steal credentials and provide backdoor access to compromised networks.
A day later, US Cybersecurity and Infrastructure Security Agency (CISA) issued an emergency directive ordering federal agencies to mitigate the vulnerability within two days by disabling the Windows File Share Browser and Pulse Secure Collaboration features.
Pulse Secure also released the Pulse Connect Secure Integrity Tool to check if hackers modified any files on their Pulse Secure appliances.
Also Read: PDPA Singapore Guidelines: 16 Key Concepts For Your Business
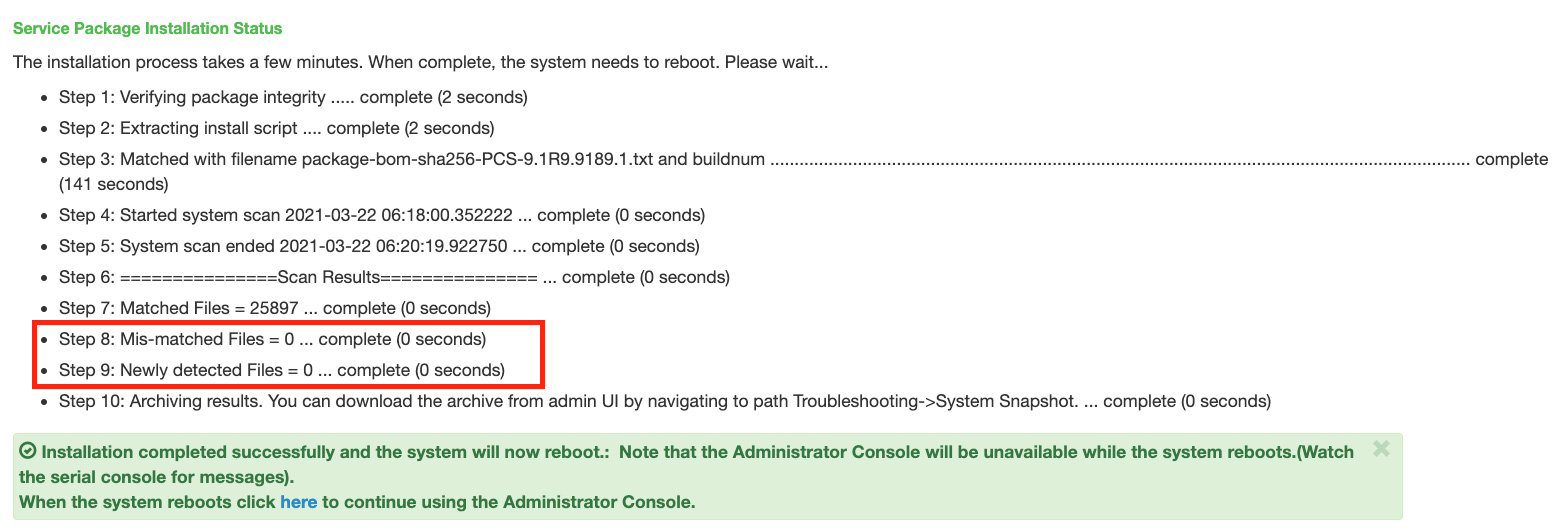
Today, Pulse Secure has released a security update for the CVE-2021-22893 vulnerability and recommends all users immediately install the patch.
“The Pulse team took swift action to provide mitigations directly to the limited number of impacted customers that remediates the risk to their system, and we are pleased to be able to deliver a security patch in such short order to address the vulnerability.” – Pulse Secure.
Organizations running Pulse Connect Secure 9.0RX & 9.1RX should immediately update to Pulse Connect Secure 9.1R11.4, which fixes the vulnerability.
Before installing the update, it is advised that organizations run the Pulse Secure Integrity Tool first to determine if their devices were breached and to respond accordingly.
Pulse Secure warns that organizations upgrading from Pulse Connect versions before 9.1R8.x may encounter issues in the browser VPN client due to an expired certificate.
Also Read: Data Protection Officer Singapore | 10 FAQs
Pulse Secure released an advisory last month that contains instructions on how to resolve this issue.