KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Ragnarok ransomware gang appears to have called it quits and released the master key that can decrypt files locked with their malware.
The threat actor did not leave a note explaining the move and all of a sudden replaced all the victims on their leak site with a short instruction on how to decrypt files.
The leak site has been stripped of visual elements and all that is left on the site is the brief text linking to an archive containing the master key and the accompanying binaries for using it.
Looking at the leak site, it seems like the gang did not plan on shutting down today, and just wiped everything and shut down their operation.
Also Read: Protecting Data Online In The New Normal
Up until earlier today, the Ragnarok ransomware leak site showed 12 victims, added between July 7 and August 16, threat intelligence provider HackNotice told BleepingComputer.
By listing victims on their website, Ragnarok sought to force them into paying the ransom, under the threat of leaking unencrypted files stolen during the intrusion.
The listed companies are from France, Estonia, Sri Lanka, Turkey, Thailand, U.S., Malaysia, Hong Kong, Spain, and Italy and activate in various sectors ranging from manufacturing to legal services.
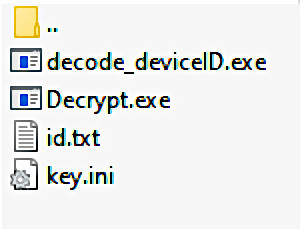
Ransomware expert Michael Gillespie told BleepingComputer that the Ragnarok decryptor released today contains the master decryption key.
“[The decryptor] was able to decrypt the blob from a random .thor file,” Gillespie told BleepingComputer initially.
The researcher later confirmed that he was able to decrypt a random file, which makes the utility a master decryptor that can be used to unlock files with various Ragnarok ransomware extensions.
A universal decryptor for Ragnarok ransomware is currently in the works and will soon be released by Emsisoft, a company famed for assisting ransomware victims with data decryption.
The Ragnarok ransomware group has been around since at least January 2020 and claimed dozens of victims after making headlines for exploiting the Citrix ADC vulnerability last year.
Also Read: The Top 4 W’s of Ethical Hacking
Ragnarok is not the only ransomware gang to release a decryption key this year
Researchers also provided decryptors [1, 2, 3] and sometimes the provenance of these tools remained uncertain, as it happened with the Kaseya attack.