KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Since 2019, ransomware gangs have leaked the stolen data for 2,103 companies on dark web data leaks sites.
When modern ransomware operations began in 2013, the attacker’s goal was to encrypt as many companies as possible and then demand a ransom payment for a decryptor.
Since the beginning of 2020, ransomware operations began conducting a new tactic called double-extortion.
Double-extortion is when ransomware operations steal unencrypted files before encrypting a network. The attackers then threaten to publicly release the stolen files on dark web data leak sites if a ransom is not paid.
Between the threat of not recovering their encrypted files and the additional concerns of data breaches, government fines, and lawsuits, threat actors are banking on the idea that this would force victims to more readily pay a ransom.
A dark web security researcher known as DarkTracer has been keeping track of the data leak sites for thirty-four ransomware gangs and told BleepingComputer that they have now leaked the data for 2,103 organizations.
The 34 ransomware gangs followed by DarkTracer are Team Snatch, MAZE, Conti, NetWalker, DoppelPaymer, NEMTY, Nefilim, Sekhmet, Pysa, AKO, Sodinokibi (REvil), Ragnar_Locker, Suncrypt, DarkSide, CL0P, Avaddon, LockBit, Mount Locker, Egregor, Ranzy Locker, Pay2Key, Cuba, RansomEXX, Everest, Ragnarok, BABUK LOCKER, Astro Team, LV, File Leaks, Marketo, N3tw0rm, Lorenz, Noname, and XING LOCKER.
Also Read: Practitioner Certificate In Personal Data Protection: Everything You Need To Know
Of these thirty-four operations, the top five active operations are Conti (338 leaks), Sodinokibi/REvil (222 leaks), DoppelPaymer (200 leaks), Avaddon (123 leaks), and Pysa (103 leaks).
Three groups that are no longer active and have more leaks than some of those in the top five are Maze (266 leaks) and Egregor (206 leaks).
The data for all the ransomware gang’s data leak sites are represented in the chart below created by DarkTracer from May 4th, 2021.
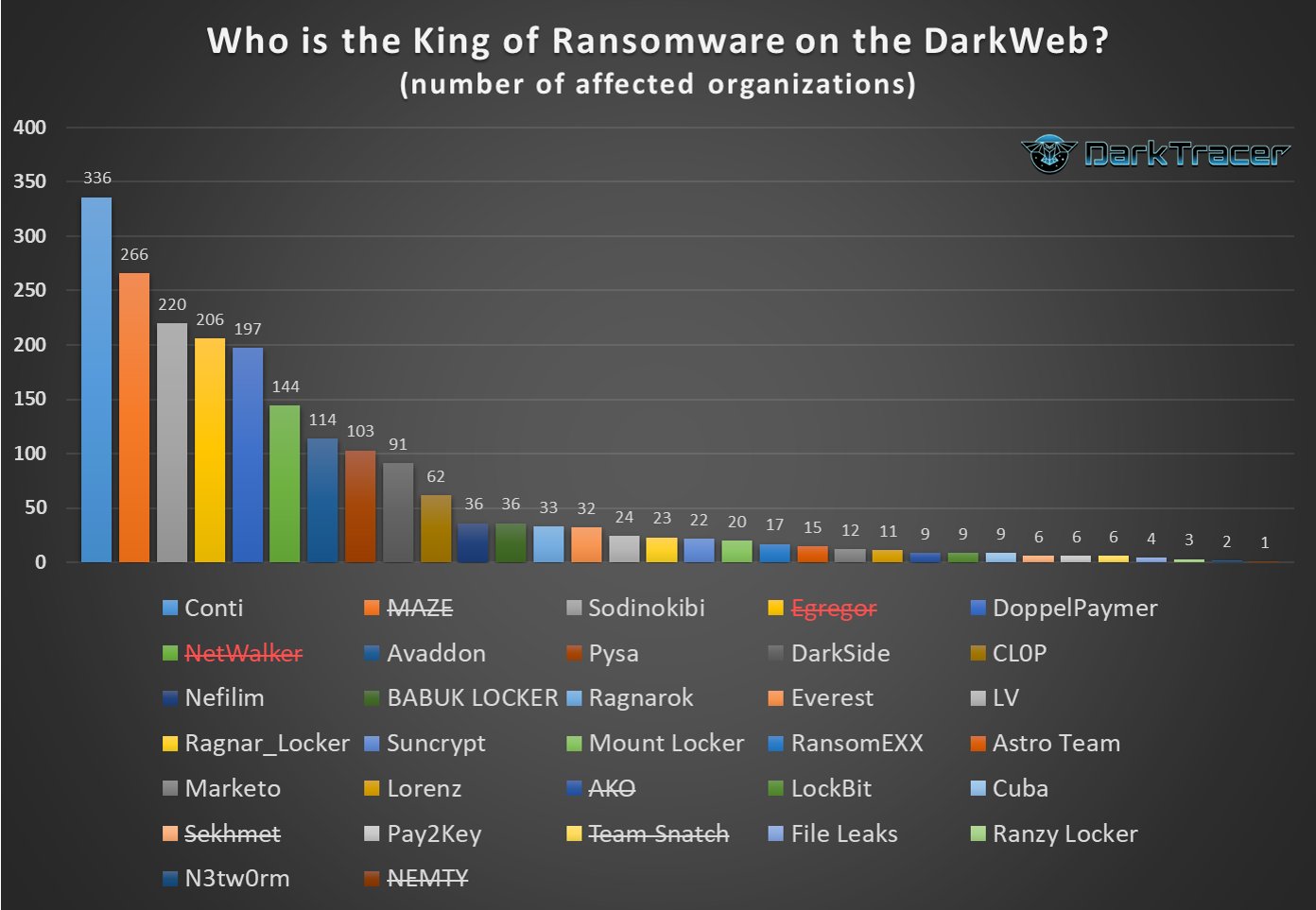
Some of the listed ransomware gangs are no longer in operation, such as NetWalker, Sekhmet, Egregor, Maze, Team Snatch, or rebranded to a new name, such as NEMTY and AKO.
The data-extortion industry has become a significant money-maker for ransomware gangs who have told BleepingComputer that victims worry more about their data being leaked than the loss of encrypted files.
Other threat actors are seeing this trend and have begun launching new data leak marketplaces over the past couple of months that exist solely to sell stolen data.
While it may seem better to pay a ransom to prevent a data leak, there is no guarantee that the data won’t be released or sold to other threat actors.
Also Read: The DNC Singapore: Looking At 2 Sides Better
Therefore, if your data is stolen, you are better off treating it as a data breach and being transparent about it to those who are affected.