KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Russian-backed hacking group Turla has used a previously undocumented malware toolset to deploy backdoors and steal sensitive documents in targeted cyber-espionage campaigns directed at high-profile targets such as the Ministry of Foreign Affairs of a European Union country.
The previously unknown malware framework, named Crutch by its authors, was used in campaigns spanning from 2015 to at least early 2020.
Turla’s Crutch malware was designed to help harvest and exfiltrate sensitive documents and various other files of interest to Dropbox accounts controlled by the Russian hacking group.
“The sophistication of the attacks and technical details of the discovery further strengthen the perception that the Turla group has considerable resources to operate such a large and diverse arsenal,” ESET researcher Matthieu Faou said in a report published today and shared in advance with BleepingComputer.
“Furthermore, Crutch is able to bypass some security layers by abusing legitimate infrastructure — here, Dropbox — in order to blend into normal network traffic while exfiltrating stolen documents and receiving commands from its operators.”
Also Read: How To Secure Your WiFi Camera: 4 Points To Consider
ESET researchers were able to link Crutch to the Russian Turla advanced persistent threat (APT) group based on similarities with the second-stage Gazer (aka WhiteBear) backdoor the threat actors used between 2016 and 2017.
The use of the same RC4 key for decrypting payloads, identical filenames while being dropped on the same compromised machine in September 2017, and almost identical PDB paths are just a few of the strong links between the two observed by ESET.
“Given these elements and that Turla malware families are not known to be shared among different groups, we believe that Crutch is a malware family that is part of the Turla arsenal,” Faou added.
Also, based on the timestamps of over 500 ZIP archives containing stolen documents and uploaded to Turla’s Dropbox accounts between October 2018 and July 2019, the working hours of Crutch’s operators line up with the Russian UTC+3 time zone.
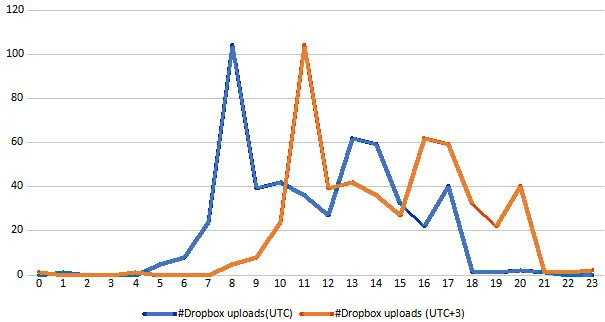
Turla delivered Crutch as a second stage backdoor on already compromised machines using first-stage implants like Skipper during 2017, months after the initial compromise in some cases, and the open-source PowerShell Empire post-exploitation framework
Early versions of Crutch (between 2015 to mid-2019) used backdoor channels to communicate with hardcoded Dropbox account via the official HTTP API and drive monitoring tools without network capabilities that searched for and archived interesting documents as encrypted archives.
An updated version (tracked as ‘version 4’ by ESET) added a removable-drive monitor with networking capabilities and removed the backdoor capabilities.
However, it allows for a more hands-off approach since it is capable of “automatically upload the files found on local and removable drives to Dropbox storage by using the Windows version of the Wget utility.”
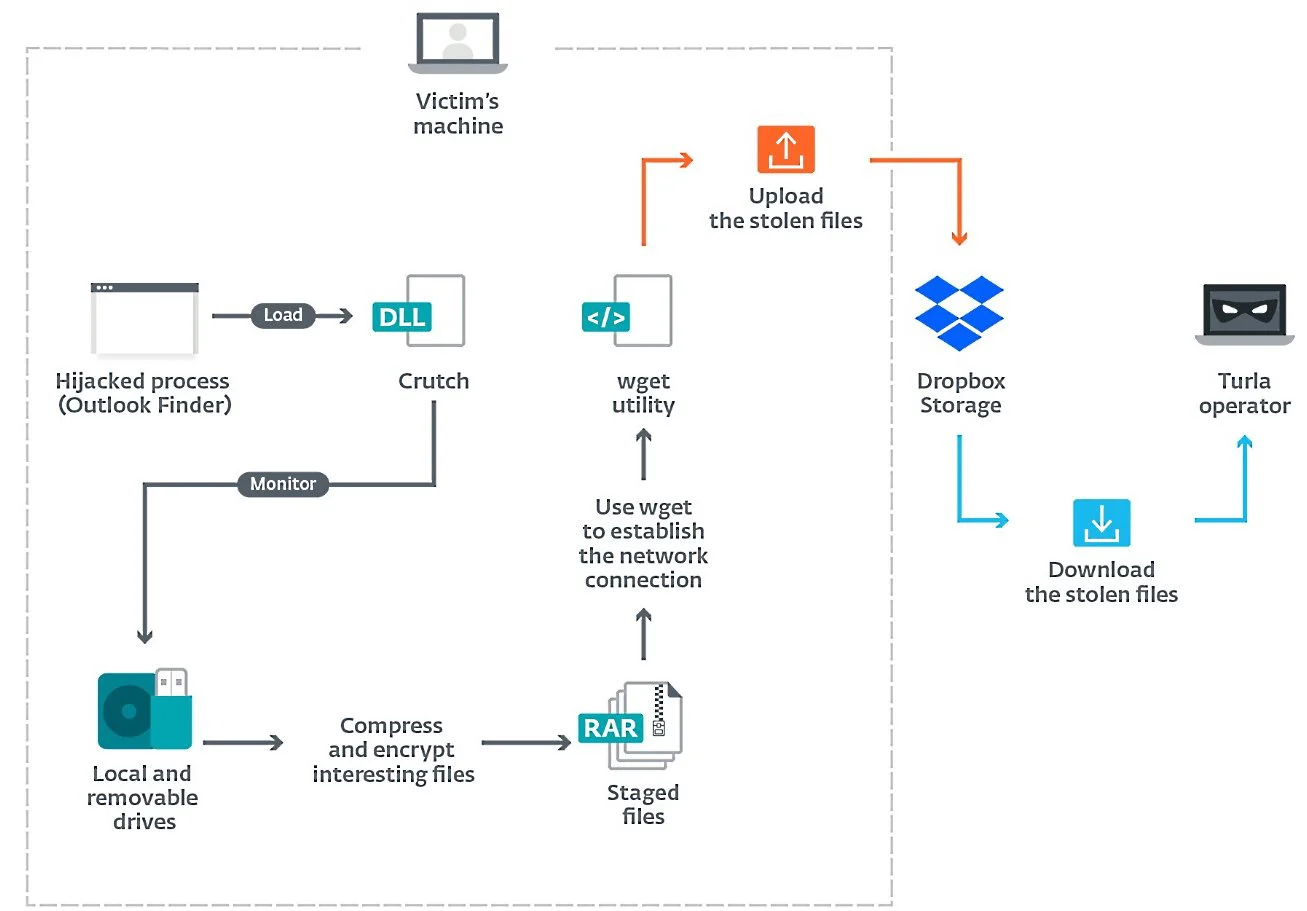
Both versions use DLL hijacking to gain persistence on compromised devices on Chrome, Firefox, or OneDrive, with Crutch v4 being dropped as “an old Microsoft Outlook component.”
“Crutch shows that the group is not short of new or currently undocumented backdoors,” Faou concluded.
“This discovery further strengthens the perception that the Turla group has considerable resources to operate such a large and diverse arsenal.”
In total, throughout their espionage campaigns, Turla has compromised thousands of systems belonging to governments, embassies, as well as education and research facilities from more than 100 countries.
The Russian Turla APT group (also tracked as Waterbug and VENOMOUS BEAR) has been behind information theft and espionage campaigns going as far back as 1996.
Also Read: How Formidable is Singapore Cybersecurity Masterplan 2020?
Turla is the main suspect behind attacks targeting the Pentagon and NASA, the U.S. Central Command, and the Finnish Foreign Ministry.
The hacking group also hacked into the systems of an undisclosed European government entity using a combo of recently updated remote administration trojans (RATs) and remote procedure call (RPC)-based backdoors according to an October report published by Accenture Cyber Threat Intelligence (ACTI).
These nation-state-backed hackers are also known for the unorthodox methods they use during their cyber-espionage campaigns such as creating backdoor trojans with their own APIs, controlling malware using comments on Britney Spears Instagram photos, and even hijacking the infrastructure and malware of Iranian APT OilRig and using them in their own campaigns.