KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







SaltStack, a VMware-owned company, has revealed critical vulnerabilities impacting Salt versions 3002 and prior, with patches available as of today.
Salt is an open-source IT infrastructure management solution written in Python that is widely used by data centers around the world.
Users are therefore encouraged to patch their Salt instances immediately.
The three vulnerabilities disclosed today are as follows, with their severity mentioned in the respective parentheses:
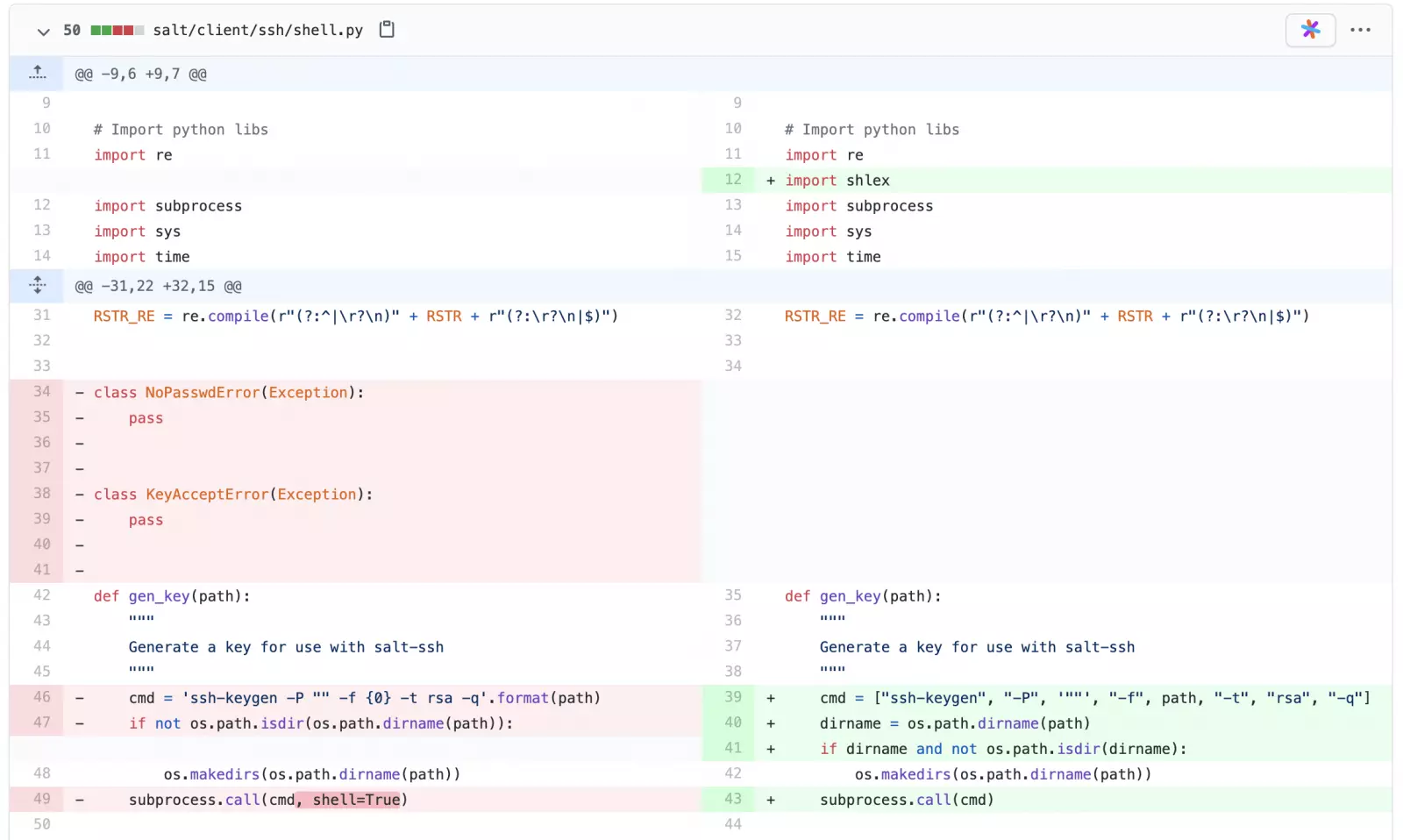 Line 49 has the “shell=True” option removed to prevent shell injection attacks
Line 49 has the “shell=True” option removed to prevent shell injection attacksAlso Read: How To Make A PDPC Complaint: With Its Importance And Impact
While the vulnerabilities were disclosed today, it is worth noting that fixes for all three vulnerabilities were committed and disclosed to GitHub much earlier.
For example, the fix for CVE-2020-16846 was pushed to GitHub as early as August 18th, and the Salt client test cases for the shell injection flaw also mention multiple Zero-Day Initiative (ZDI) IDs, such as ZDI-CAN-11143. The date of the original report on this identifier, however, is June 2020 as shown below.
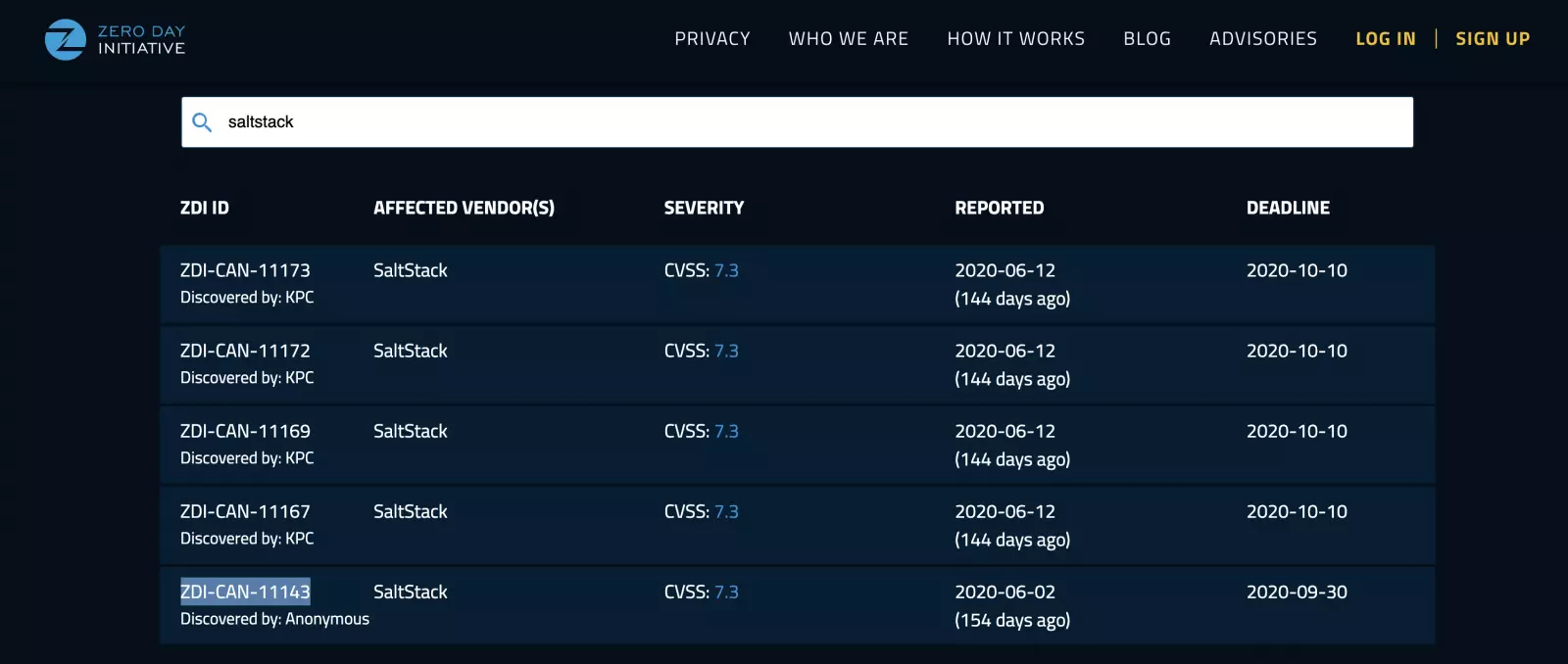
The November 3rd advisory does attribute the discovery of CVE-2020-16846 and CVE-2020-17490 to KPC of Trend Micro Zero Day Initiative who had reported multiple ZDI vulnerabilities in June 2020.
It is not clear why SaltStack published the CVEs and fixes publicly to GitHub before publicly disclosing them as this could have been abused by threat actors to create exploits.
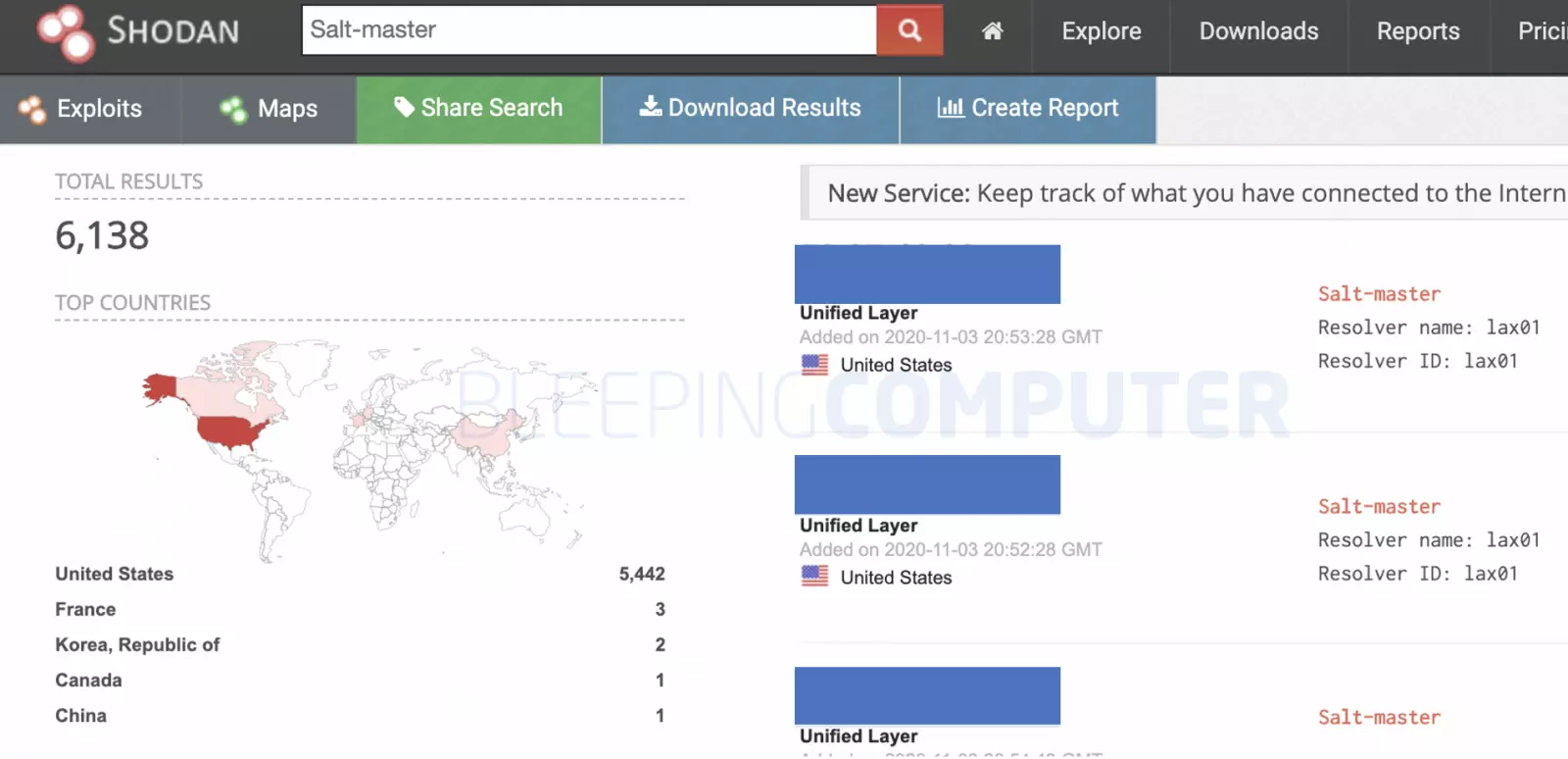
As observed by BleepingComputer today, Shodan lists over 6,000 Salt Master nodes exposed to the internet, not all of which may be running the latest, patched versions.
On October 30th, SaltStack had released a security advisory indicating these CVEs were to come, this Election Day.
The advance partial disclosure on these critical vulnerabilities is a cautious move on SaltStack’s part given the widespread attacks that had hit vulnerable Salt instances earlier this year.
“Two of these vulnerabilities are expected to be rated as high/critical and the other is expected to be low based on the Common Vulnerability Scoring System (CVSS). Once SaltStack became aware of the vulnerabilities, we quickly took actions to remediate them,” stated the October 30th advisory.
Partial disclosures are increasingly becoming the norm for open-source software.
Giving everyone a heads up allows time for the vulnerable instances to be patched before security flaws can potentially be exploited in the wild by adversaries.
Also Read: Deemed Consent PDPA: How Do Businesses Comply?
The fixed versions include 3002.1, 3001.3, and 3000.5 depending on what branch of Salt you are using. The company has also made patches available for older versions, such as 2019.x.
SaltStack has provided some tips on how to harden your Salt instances, in addition to patching for new vulnerabilities that may be discovered from time to time.
It remains questionable, despite the company giving an advance heads up, whether Election Day is ever the right time to disclose critical vulnerabilities—especially considering the fixed versions have also been released today, coinciding with the full disclosure.
Users can download the fixed releases from PyPI downloads as of now. More information is also available in the November 3, 2020 advisory.