KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!





The TrickBot gang operators are now abusing the Windows 10 App Installer to deploy their BazarLoader malware on the systems of targets who fall victim to a highly targeted spam campaign.
BazarLoader (aka BazarBackdoor, BazaLoader, BEERBOT, KEGTAP, and Team9Backdoor) is a stealthy backdoor Trojan commonly used to compromise the networks of high-value targets and sell access to compromised assets to other cybercriminals.
It has also been used to deliver additional payloads, such as Cobalt Strike beacons that help threat actors access their victims’ network and ultimately deploy dangerous malware, including but not limited to Ryuk ransomware.
In the recent campaign spotted by SophosLabs Principal Researcher Andrew Brandt, the attackers’ spam emails induce a sense of urgency by using threatening language and impersonating a company manager who asks for more info on a customer complaint about the email recipient.
Also Read: Top 8 Main PDPA Obligations To Boost And Secure Your Business
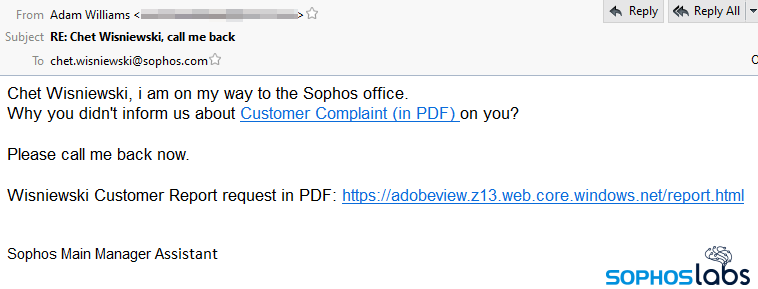
This complaint is supposedly available for review as a PDF from a site hosted on Microsoft’s own cloud storage (on *.web.core.windows.net domains).
To add to the ruse, those on the receiving end of this spam campaign are double baited into installing the BazarLoader backdoor using an adobeview subdomain that further adds credibility to the scheme.
“The attackers used two different web addresses for hosting this fake ‘PDF download’ page throughout the day,” Brandt said.
“Both pages were hosted in Microsoft’s cloud storage, which perhaps lends it a sense of (unearned) authenticity, and both the .appinstaller and .appbundle files were hosted in the root of each webpage’s storage.”
Also Read: 5 Tips In Using Assessment Tools To A Successful Businesses
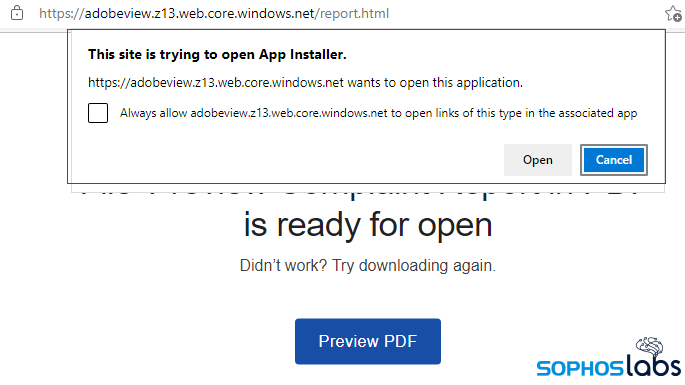
However, instead of pointing to a PDF document, the “Preview PDF” button on the phishing landing site opens a URL with an ms-appinstaller: prefix.
When clicking the button, the browser will first show a warning asking the victim if they want to allow the site to open App Installer. However, most people will likely ignore it when seeing an adobeview.*.*.web.core.windows.net domain in the address bar.
Clicking “Open” in the warning dialog will launch Microsoft’s App Installer — a built-in app since the release of Windows 10 version 1607 in August 2016 — to deploy the malware on the victim’s device in the form of a fake Adobe PDF Component, delivered as an AppX app bundle.
Once launched, App Installer will first start downloading the attackers’ malicious .appinstaller file and a linked .appxbundle file containing the final payload named Security.exe nested within a UpdateFix subfolder.
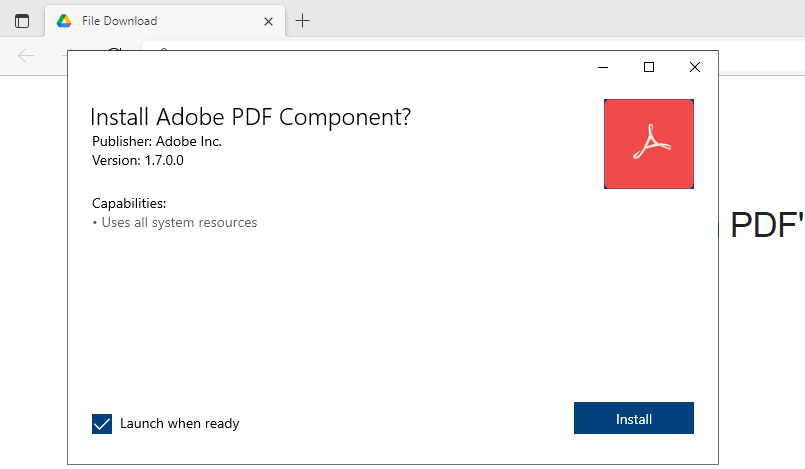
The payload downloads and executes an additional DLL file which is launched and spawns a child process which in turn spawns other child processes, eventually ending the string with the injection of the malicious code into a headless Chromium-based Edge browser process.
After getting deployed on the infected device, BazarLoader will begin harvesting system information (e.g., hard disk, processor, motherboard, RAM, active hosts on the local network with public-facing IP addresses).
This information is sent to the command-and-control server, camouflaged as cookies delivered through HTTPS GET or POST headers.
“Malware that comes in application installer bundles is not commonly seen in attacks. Unfortunately, now that the process has been demonstrated, it’s likely to attract wider interest,” Brandt said.
“Security companies and software vendors need to have the protection mechanisms in place to detect and block it and prevent the attackers from abusing digital certificates.”
You can find indicators of compromise (IoCs) related to this BazarLoader campaign, including malware sample hashes, command-and-control server, and source URLs, on SophosLabs’ Github page.
Microsoft took down the pages used by the attackers to host malicious files in these attacks on November 4, after being notified by Sophos.