KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







A critical Apache Log4j vulnerability took the world by storm this week, and now it is being used by threat actors as part of their ransomware attacks.
Last Friday, a researcher publicly released an exploit for the Log4j vulnerability, dubbed ‘Log4Shell.’ after it was already seen targeting vulnerable Minecraft servers.
While a patch was quickly released to fix the vulnerability, researchers and threat actors quickly began scanning for and exploiting vulnerable devices. With how fast it was adopted, it was only a matter of time until threat actors used it to deploy ransomware.
It didn’t take long, as threat actors revived an old ransomware named TellYouThePass on Monday and began distributing it via Log4j exploits.
Also Read: Data Minimization; Why Bigger is Not Always Better
Soon after, another ransomware (or wiper) called Khonsari was discovered that we later learned it was targeting vulnerable Minecraft servers.
Finally, a report today shows how the Conti ransomware gang is using the Log4j vulnerability to quickly gain access to internal VMWare vCenter servers to encrypt virtual machines.
While the Log4j vulnerability has taken up most of the cybersecurity community’s time this week, there have been other significant developments as well.
Romanian police arrested a ransomware affiliate for hacking and stealing sensitive info from the networks of multiple high-profile companies worldwide.
Emotet also began distributing Cobalt Strike beacons as a primary payload, allowing ransomware gangs quicker access to compromised networks to conduct attacks.
We also learned that the Hive Ransomware operation is becoming a major player after breaching hundreds of companies in just four months.
Finally, a massive ransomware attack against HR services provider Kronos has caused significant impact for many companies who use them for timekeeping and payroll. We also saw a Conti attack on McMenamins breweries, showing that nothing is sacred.
Contributors and those who provided new ransomware information and stories this week include: @LawrenceAbrams, @DanielGallagher, @PolarToffee, @jorntvdw, @malwrhunterteam, @demonslay335, @VK_Intel, @malwareforme, @serghei, @Seifreed, @FourOctets, @struppigel, @Ionut_Ilascu, @fwosar, @BleepinComputer, @billtoulas, @SANGFOR, @CuratedIntel, @80vul, @1ZRR4H, @AdvIntel, @MsftSecIntel, @GroupIB_GIB, @Bitdefender_Ent, @Cryptolaemus1, @JRoosen, @BroadcomS, @fbgwls245, @Amigo_A_,@JakubKroustek, and @pcrisk.
Jakub Kroustek found a new STOP ransomware variant that appends the .yjqs extension to encrypted files.
Also Read: Vulnerability Management For Cybersecurity Dummies
Romanian law enforcement authorities arrested a ransomware affiliate suspected of hacking and stealing sensitive info from the networks of multiple high-profile companies worldwide, including a large Romanian IT company with clients from the retail, energy, and utilities sectors.
Workforce management solutions provider Kronos has suffered a ransomware attack that will likely disrupt many of their cloud-based solutions for weeks.
The first public case of the Log4j Log4Shell vulnerability used to download and install ransomware has been discovered by researchers.
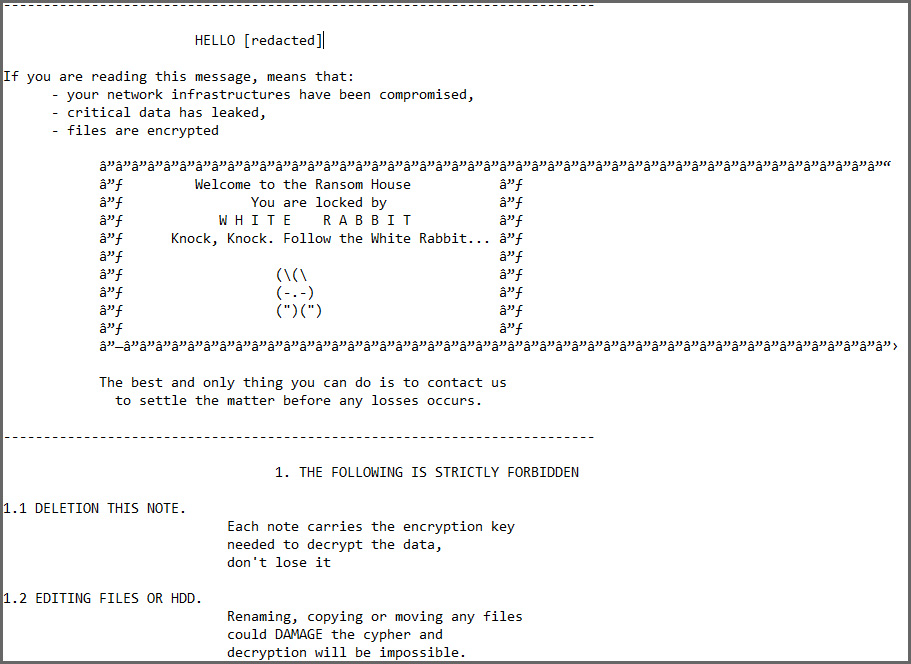
Michael Gillespie is looking for a sample of the new White Rabbit ransomware that appends the .scrypt extension.
Right in time for the holidays, the notorious Emotet malware is once again directly installing Cobalt Strike beacons for rapid cyberattacks.
PCrisk found a new STOP ransomware variant that appends the .Shgv extension to encrypted files.
The Hive ransomware gang is more active and aggressive than its leak site shows, with affiliates attacking an average of three companies every day since the operation became known in late June.
Portland brewery and hotel chain McMenamins suffered a Conti ransomware attack over the weekend that disrupted the company’s operations.
Microsoft urges admins of self-hosted Minecraft servers to upgrade to the latest release to defend against Khonsari ransomware attacks exploiting the critical Log4Shell security vulnerability.
Symantec, a division of Broadcom Software, tracks this ransomware as Ransom.Noberus and our researchers first spotted it on a victim organization on November 18, 2021, with three variants of Noberus deployed by the attackers over the course of that attack. This would appear to show that this ransomware was active earlier than was previously reported, with MalwareHunterTeam having told BleepingComputer they first saw this ransomware on November 21.
PCrisk found a new STOP ransomware variant that appends the .hudf extension to encrypted files.
Conti ransomware operation is using the critical Log4Shell exploit to gain rapid access to internal VMware vCenter Server instances and encrypt virtual machines.
Hellmann Worldwide is warning customers of an increase in fraudulent calls and emails regarding payment transfer and bank account changes after a recent ransomware attack.
Threat actors have revived an old and relatively inactive ransomware family known as TellYouThePass, deploying it in attacks against Windows and Linux devices targeting a critical remote code execution bug in the Apache Log4j library.
dnwls0719 found a new Dharma ransomware variant that appends the .C1024 extension to encrypted files.