KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!






This week started with a bang as a large hospital chain was hit by a ransomware attack that disrupted the healthcare industry.
We first learned of this Ryuk Ransomware attack on Universal Health Services (UHS) on Monday morning when doctors, nurses, and employees reported on Reddit that their hospitals were affected.
We also learned about a ransomware attack on insurance giant Arthur J. Gallagher (AJG), but it is not known which ransomware conducted the attack.
The Blackbaud attack, which affected so many organizations, stated that their attack exposed banking information and passwords.
Finally, a ransomware gang is kicking victims while they are down by DDoSing their websites if they do not pay.
The one bit of good news this week is the release of a free decryptor for the ThunderX ransomware.
Contributors and those who provided new ransomware information and stories this week include: @Ionut_Ilascu, @Seifreed, @BleepinComputer, @FourOctets, @DanielGallagher, @fwosar, @LawrenceAbrams, @struppigel, @serghei, @jorntvdw, @malwrhunterteam, @PolarToffee, @malwareforme, @demonslay335, @VK_Intel, @nao_sec, @CORE561, @PogoWasRight, @M_Shahpasandi, @fbgwls245, @MarceloRivero, @0x4143, and @GrujaRS.
Tyler Technologies is warning clients to change the passwords for the technology provider’s remote access accounts after suspicious logins have been reported.
A decryptor for the ThunderX ransomware has been released by cybersecurity firm Tesorion that lets victims recover their files for free.
GrujaRS found a new ransomware that appends the .babaxed extension and drops a ransom note named RECOVERY INSTRUCTIONS.
Universal Health Services (UHS), a Fortune 500 hospital and healthcare services provider, has reportedly shut down systems at healthcare facilities around the US after a cyber-attack that hit its network during early Sunday morning.
The REvil Ransomware (Sodinokibi) operation has deposited $1 million in bitcoins on a Russian-speaking hacker forum to prove to potential affiliates that they mean business.
CMA CGM S.A., a French maritime transport and logistics giant, today disclosed a malware attack affecting some servers on the edge of its network.
Michael Gillespie found a new Dharma Ransomware variant that appends the .WSHLP extension.
M. Shahpasandi found a new MedusaLocker ransomware variant that appends the .lr extension.
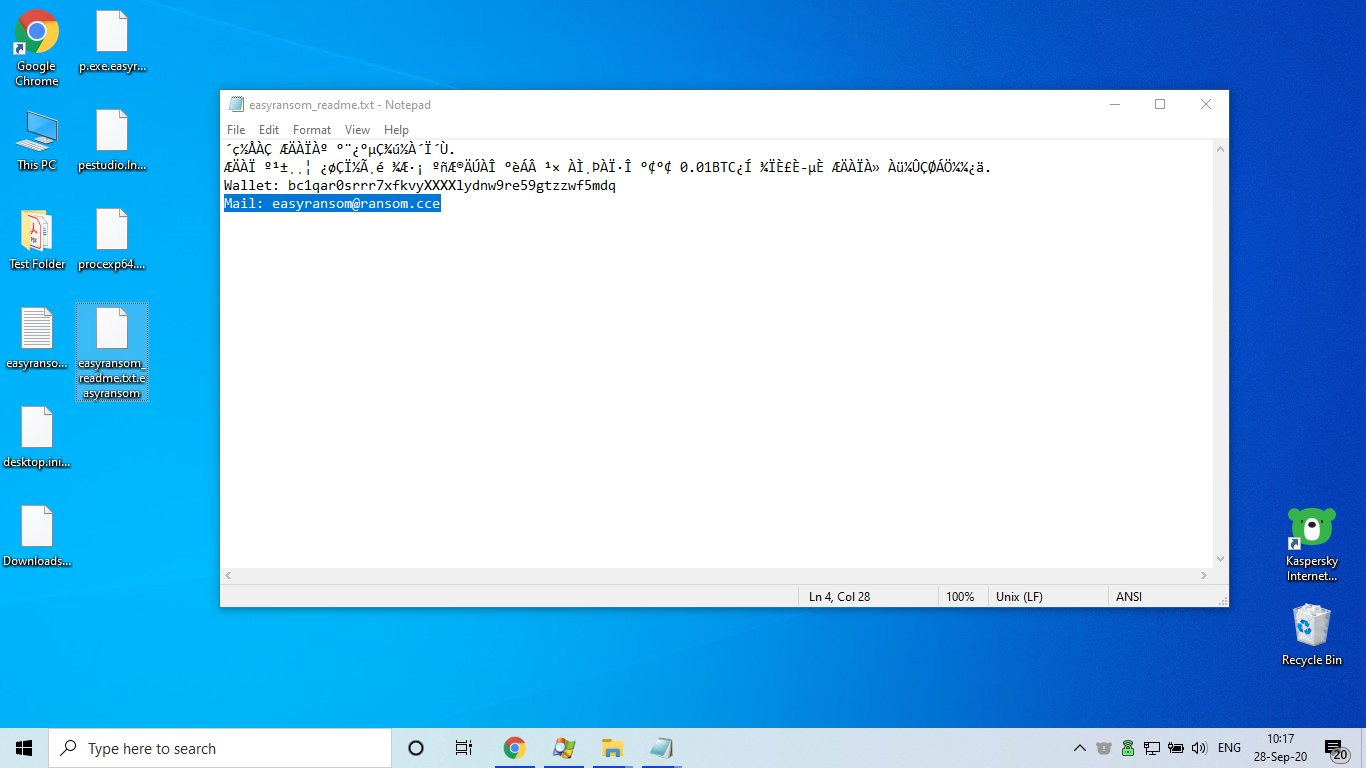
GrujaRS found a new ransomware that appends the .easyransom extension and drops a ransom note named easyransom_readme.txt.
Also Read: 12 Benefits of Data Protection for Business Success
The threat actors behind the Exorcist 2.0 ransomware are using malicious advertising to redirect victims to fake software crack sites that distribute their malware.
US-based Arthur J. Gallagher (AJG) global insurance brokerage and risk management firm confirmed a ransomware attack that hit its systems on Saturday.
Michael Gillespie found a new STOP Ransomware variant that appends the .lyli extension to encrypted files.
dnwls0719 found a new Phobos Ransomware variant that appends the .isos extension to encrypted files.
Blackbaud, a leading cloud software provider, confirmed that the threat actors behind the May 2020 ransomware attack had access to unencrypted banking and login information, as well as social security numbers.
QNAP has issued an advisory about a recent wave of ransomware attacks targeting its NAS storage devices and encrypting files.
So SunCrypt pledges to leave medical entities alone, and DataBreaches.net hopes they stick to their pledge on that. But who will be they be focusing on, then? According to the spokesperson, “Suncrypt is after the cybersecurity companies,” and they say we will all be seeing proof of that very soon.
Jakub Kroustek found a new variant of the Dharma Ransomware that appends the .fresh extension to encrypted files.
0x4143 found a new ransomware that appends the ‘.mame vse‘ extension to encrypted files.
Also Read: Completed DPIA Example: 7 Simple Helpful Steps To Create
The Netwalker ransomware operators have published the stolen data for K-Electric, Pakistan’s largest private power company, after a ransom was not paid.
A ransomware operation has started to utilize a new tactic to extort their victims: DDoS a victim’s website until they return to the negotiation table.
The U.S. Treasury Department’s Office of Foreign Assets Control (OFAC) today said that organizations that assist ransomware victims to make ransom payments are facing sanctions risks as their actions could violate OFAC regulations.
Marcelo Rivero found a new variant of the Dharma Ransomware that appends the .homer extension to encrypted files.