KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!





A global-scale phishing campaign targeted worldwide organizations across an extensive array of industries with never-before-seen malware strains delivered via specially-tailored lures.
The attacks hit at least 50 orgs from a wide variety of industries in two waves, on December 2nd and between December 11th and 18th, according to a Mandiant report published today.
UNC2529, as Mandiant threat researchers track the “uncategorized” threat group behind this campaign, has deployed three new malware strains onto the targets’ computers using custom phishing lures.
The malware used by UNC2529 in these attacks is heavily obfuscated to hinder analysis, and it attempts to evade detection by deploying payload in-memory whenever possible.
“The threat actor made extensive use of obfuscation and fileless malware to complicate detection to deliver a well coded and extensible backdoor,” Mandiant said.
Throughout the two waves of attacks, the threat group used phishing emails with links to a JavaScript-based downloader (dubbed DOUBLEDRAG) or an Excel document with an embedded macro that downloaded an in-memory PowerShell-based dropper (known as DOUBLEDROP) from attackers’ command-and-control (C2) servers.
The DOUBLEDROP dropper bundles 32 and 64-bit instances of a backdoor (named DOUBLEBACK) implemented as a PE dynamic library.
Also Read: Practitioner Certificate In Personal Data Protection: Everything You Need To Know
The backdoor gets injected into the PowerShell process spawned by the dropper. Still, it is designed to later attempt to inject itself into a newly spawned Windows Installer (msiexec.exe) process if Bitdefender’s antivirus engine is not running on the compromised computer.
In the next stage, the DOUBLEBACK backdoor loads its plugin and reaches out to the C2 server in a loop to fetch commands to execute on the infected device.
“One interesting fact about the whole ecosystem is that only the downloader exists in the file system,” Mandiant added.
“The rest of the components are serialized in the registry database, which makes their detection somewhat harder, especially by file-based antivirus engines.”
UNC2529 used considerable infrastructure to pull off their attacks, with roughly 50 domains being used to deliver the phishing emails.
The group also invested time into tailoring their attacks to the targeted victims, in evident attempts to make sure that their emails were seen as legitimate messages from business partners or clients.
They used this tactic to increase the chance that their booby-trapped messages were opened and the targets got infected.
“Masquerading as the account executive, seven phishing emails were observed targeting the medical industry, high-tech electronics, automotive and military equipment manufacturers, and a cleared defense contractor with subject lines very specific to the products of the California-based electronics manufacturing company,” according to Mandiant.
UNC2529’s phishing campaign was not focused on a single industry vertical or a single region during the two waves of attacks.
While the threat group’s primary target area was the US, the attacks also targeted organizations from EMEA (Europe, the Middle East, and Africa), Asia, and Australia.
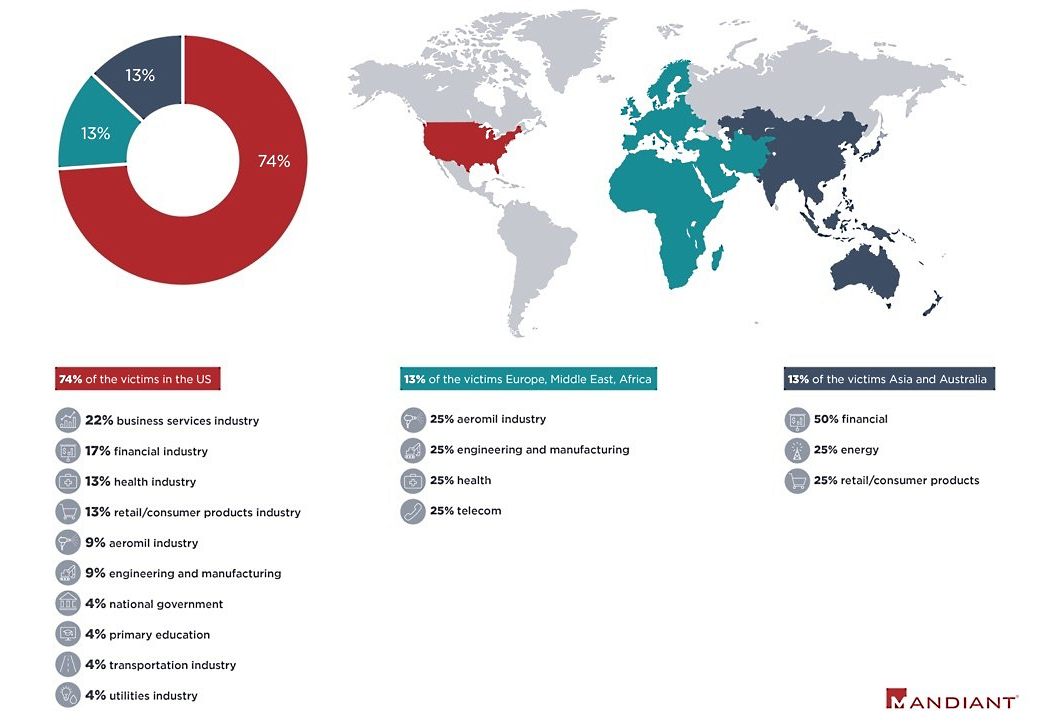
“Although Mandiant has no evidence about the objectives of this threat actor, their broad targeting across industries and geographies is consistent with a targeting calculus most commonly seen among financially motivated groups,” Mandiant concluded.
“DOUBLEBACK appears to be an ongoing work in progress and Mandiant anticipates further actions by UNC2529 to compromise victims across all industries worldwide.”
Also Read: The DNC Singapore: Looking At 2 Sides Better
Indicators of compromise, including malware hashes and domains used to deliver the phishing emails, are available at the end of Mandiant’s report.