KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







The data breaches caused by the Clop ransomware gang exploiting a zero-day vulnerability have led to a sharp increase in the average ransom payment calculated for the first three months of the year.
Clop’s attacks did not encrypt a single byte but stole data from large companies that relied on Accellion’s legacy File Transfer Appliance (FTA) and tried to extort them with high ransom demands.
The incidents started in December 2020 and continued in January 2021. In February, Clop had already started to publish data from victims that refused to pay them.
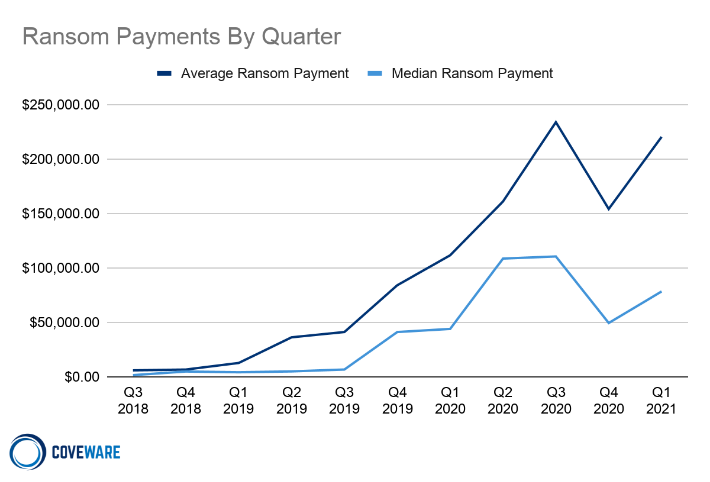
These attacks set to $220,298 the average ransom payment in the first quarter of 2021, which translates to a 43% increase compared to the last quarter of 2020, notes ransomware remediation firm Coveware.
The median ransom payment is also up, by almost 60%, reaching $78,398 from $49,450.
Also Read: The DNC Registry Singapore: 5 Things You Must Know
Coveware says that the figures are the result of Clop ransomware being particularly active in Q1 and demanding large ransoms from big companies they had breached.
Although Accellion’s FTA software solution was used by a small number of companies (around 100), the names on the list stand out:
Given the high profile of the targets, the Clop ransomware gang likely yielded high returns from the extortion campaigns, with many victims ending up paying big money to stop a data leak.
“Dozens of CloP victims were extorted for tens of millions of dollars even though the majority of the victims opted not to pay and were subsequently doxxed on the CloP leak site” – Coveware
Clop’s Accellion campaign seems to have reached an end in early April, as the gang started returned to data encryption operations made possible by typical network access vectors.
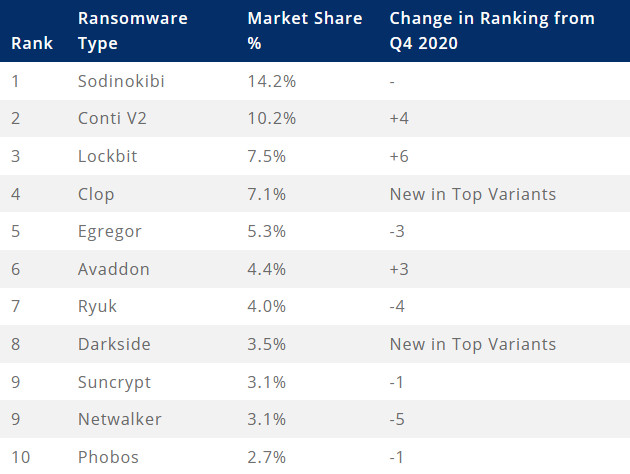
Despite being responsible for the increased average and median ransom payments, the Clop ransomware gang was not the most active since the beginning of the year.
As per Coveware’s data, the market share for ransomware attacks is dominated by REvil, Conti, and Lockbit operations, followed by Clop.
Coveware says that some of these ransomware operations have become so big and complex that they made technical-level mistakes that affected the credibility they’ve been building to make victims pay.
Conti outsourced chat operations, which made negotiations and victim recovery more difficult. Furthermore, the gang targeted the same victim multiple times, sometimes immediately after an initial attack.
Some REvil ransomware attacks ended with losing all the data because of “technical flaws that resulted in victims unable to match encryption keys.”
Data loss issues also occurred during some Lockbit attacks. Furthermore, this actor tried to extort their victims multiple times, says Coveware CEO Bill Siegel.
Despite these issues, which victims should see as a warning not to pay the ransom, the threat actors in the ransomware business are looking to extend operations to Linux and Unix machines.
Siegel says that multiple actors, like Defray777, Mespinoza, Babuk, Nephilim, and Darkside, are already focusing on this direction. Another actor that announced this move is REvil.
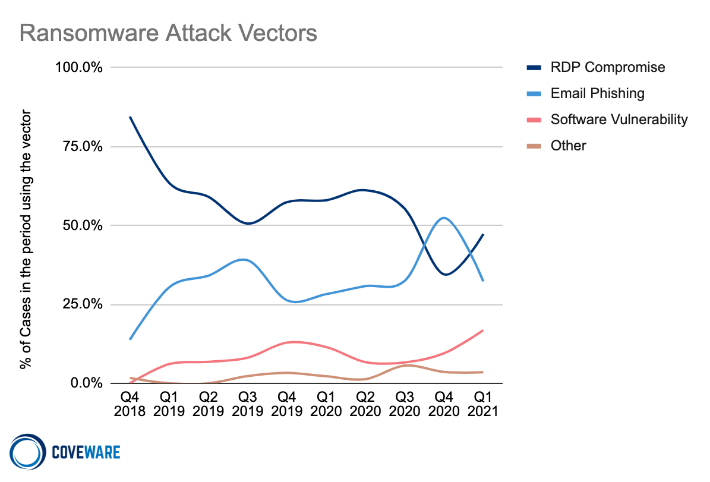
As for the most common initial access vector, Siegel says that remote desktop protocol (RDP) is still at the top, followed by email phishing, and software vulnerabilities.
Companies falling victim to ransomware attacks are recommended not to pay the extortionists so they are less encouraged to continue the practice. Additionally, paying the hackers gives a false sense of security that data won’t be leaked or traded on underground forums.
Also Read: How To Comply With PDPA: A Checklist For Businesses
Coveware says that before deciding on paying the threat actor victims of data exfiltration should consider that there is no guarantee that the attacker destroyed the data, or would not sell or keep it for future extortion.
Moreover, stolen data passed multiple hands without being secured and there is no way to tell that there are no copies left even if the threat actor keeps their end of the deal and destroys it.