KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!






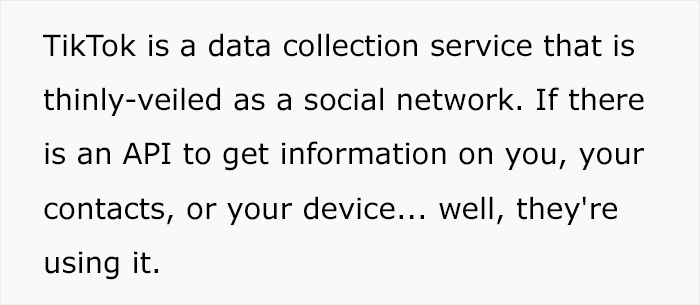
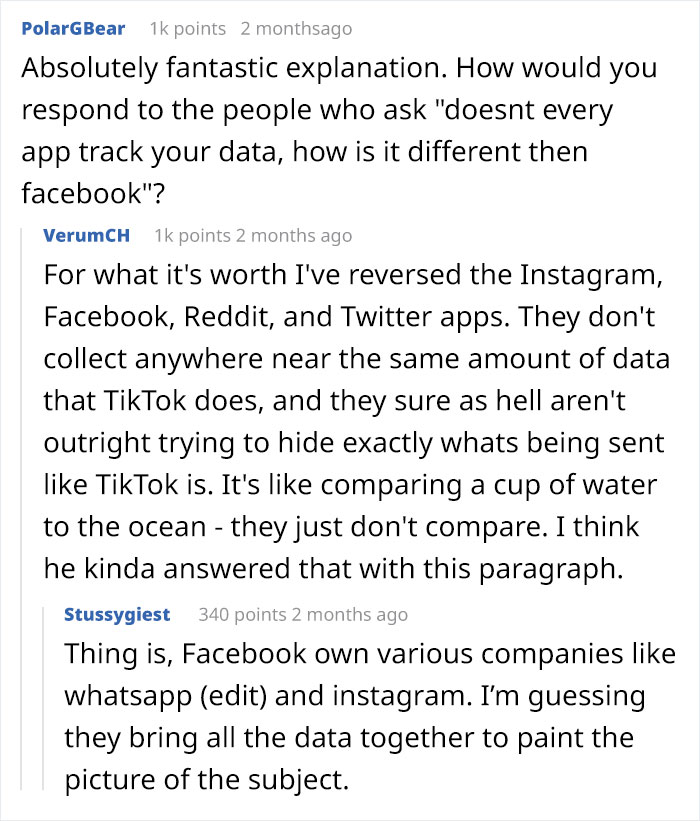
Facebook got itself into a sensitive data scandal when it did shady business with Cambridge Analytica, Instagram confirmed a security issue exposing user accounts and phone numbers, but these apps are basically online security havens compared to TikTok, according to one senior software engineer with about 15 years of professional experience.
2 months ago, Reddit user bangorlol made a comment in a discussion about TikTok. Bangorlol claimed to have successfully reverse-engineered it and shared what he learned about the Chinese video-sharing social networking service. Basically, he strongly recommended that people never use the app again, warning about its intrusive user tracking and other issues. Considering that TikTok was the 4th most popular free iPhone app download in 2019, this is quite alarming.

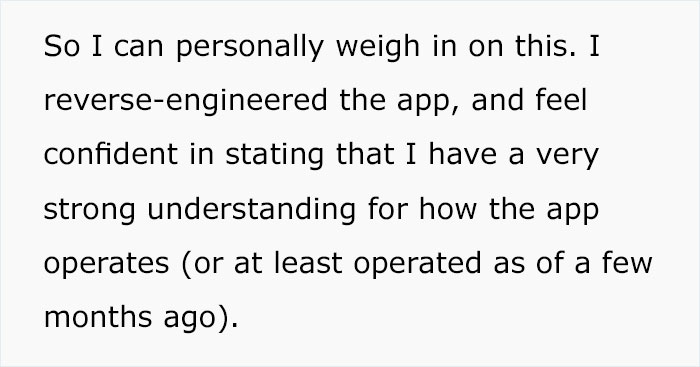
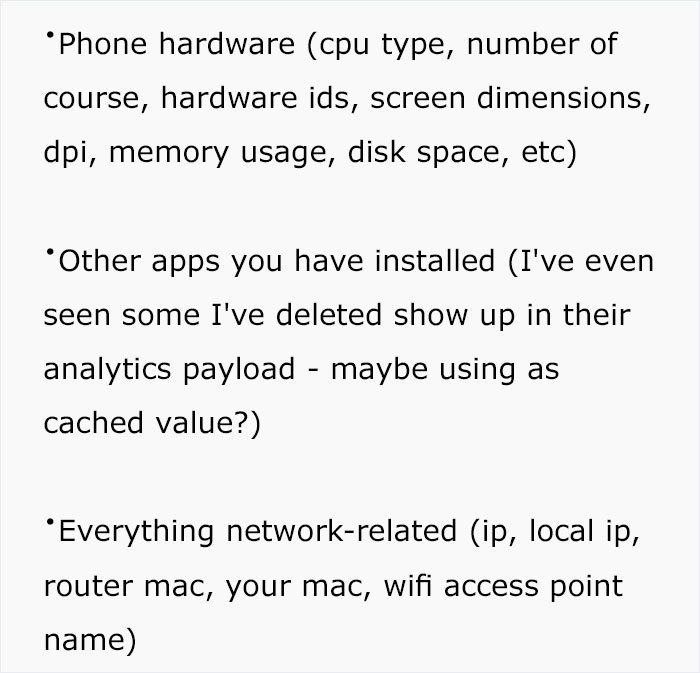
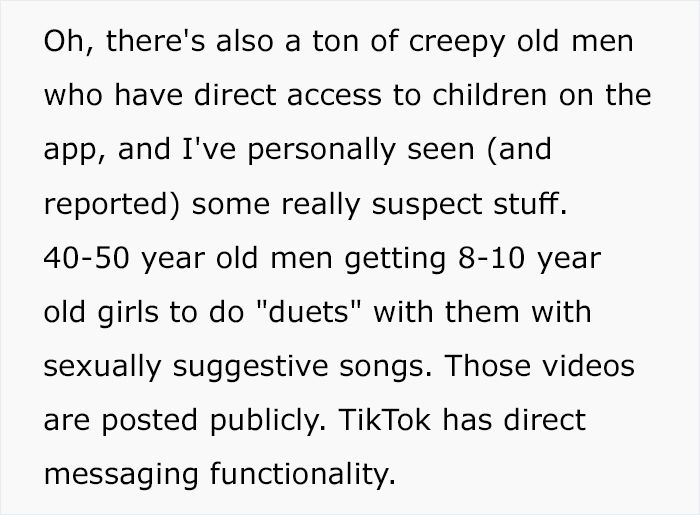
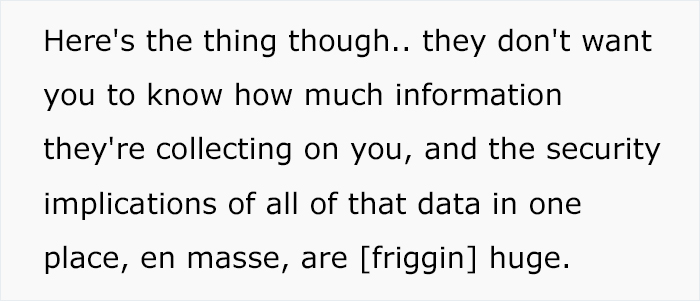
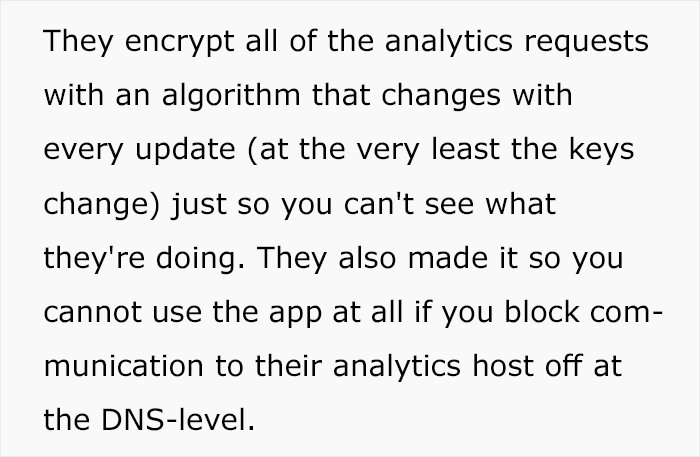
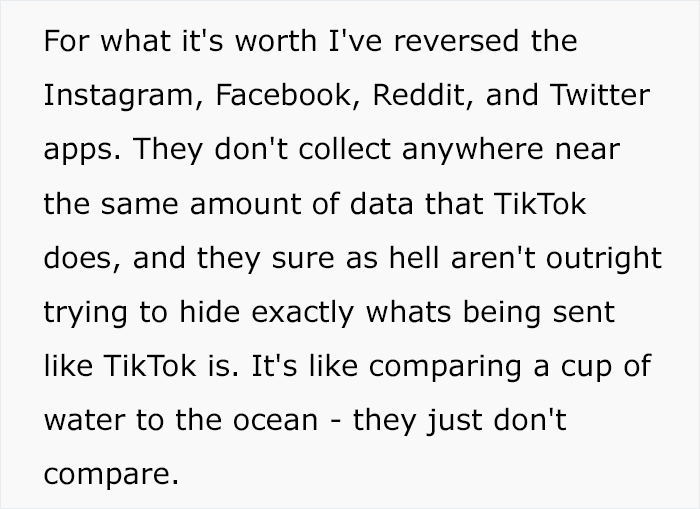
Bangorlol is no script kiddie. “The last several years of my career has been based around reversing mobile applications, analyzing how they work, and building additional third-party functionality around them,” he told Bored Panda. “A rough example would be me noticing that Twitter doesn’t show you a sequential timeline (no idea if they do or not) on the website but does on the app. I’d go into the Android or iOS version, find the requests that get the correct data, and build a third-party tool (app, website, browser extension) to give users this functionality.”
“Lately, it mostly involves reversing my company’s partner APIs so we don’t have to wait for them to create something custom for us. I hunt bug bounties when I’ve got the time, or help my friends out with theirs (or their CTF challenges). I like security in general and typically find at least a few major flaws whenever I change employers. I’m kind of a ‘jack of all trades’ kind of guy in the sense that I’m comfortable in most areas of software engineering and mostly pretty okay with many security topics.”
Reportedly, it took 200 days for the Chinese development team to create the original version of TikTok, but when Bangorlol got his cursor on its code, it had no chance. Although, it did try to put up a fight. “TikTok put a lot of effort into preventing people like me from figuring out how their app works. There’s a ton of obfuscation involved at all levels of the application, from your standard Android variable renaming grossness to them (bytedance) forking and customizing ollvm for their native stuff. They hide functions, prevent debuggers from attaching, and employ quite a few sneaky tricks to make things difficult. Honestly, it’s more complicated and annoying than most games I’ve targeted,” Bangorlol explained.
Such secrecy is understandable. TikTok’s earnings have risen proportionately with its increase in popularity and its owner ByteDance made a net profit of $3 billion last year, according to a report from Bloomberg.
Bangorlol thinks that we as a society have normalized giving away our personal information and have no expectations of privacy and security anymore, so giving TikTok our data together with our money is nothing surprising. “The general consensus among most ‘normal’ people is that they can’t/won’t be targeted, so it’s fine. Or that they have nothing to hide, so ‘why should I even care?’ I think the apathy is sourced from people just not understanding the security implications (at all levels) of handing over our data to a foreign government that doesn’t discriminate against who they target, and also doesn’t really have the best track record when it comes to human rights,” he said.
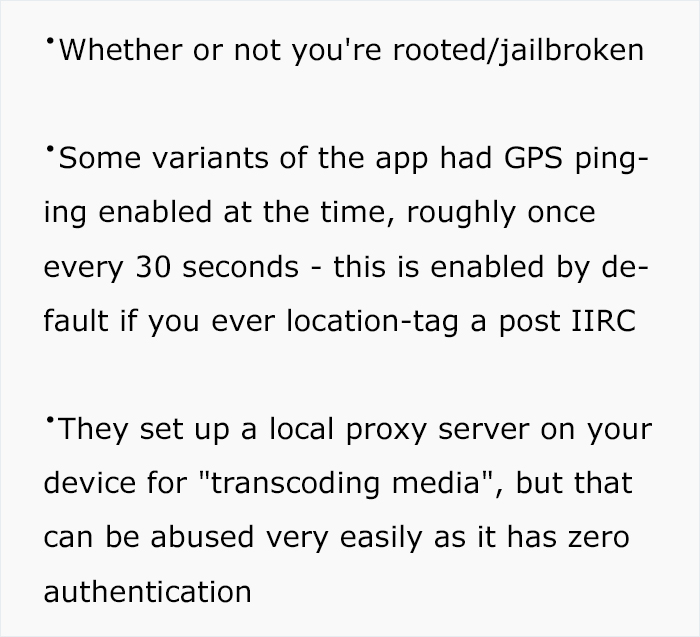
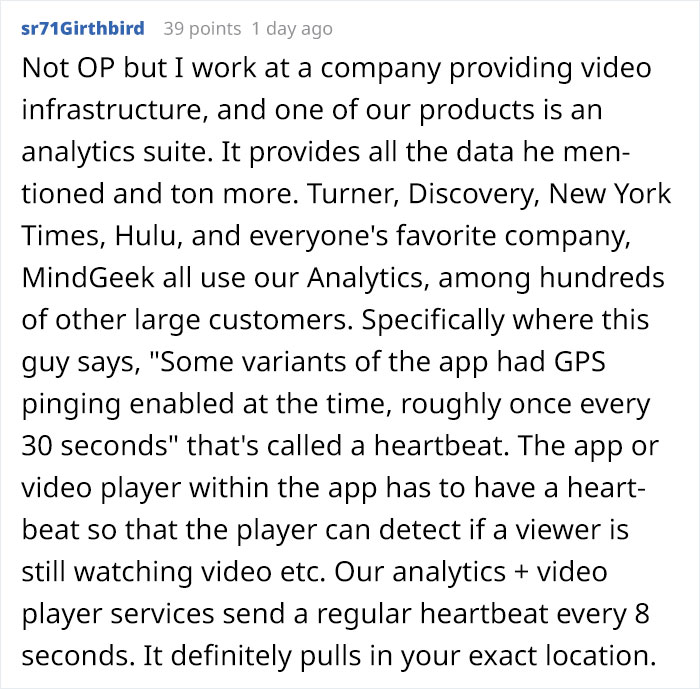
Keep in mind that Bangorlol released his initial commentary a while ago and hasn’t touched the app in months, and when he posted his findings, they were also a few months behind. “The app could’ve changed fingerprinting techniques or added/removed some of the nasty things they do. I strongly encourage security researchers who are much smarter than me and have more free time to take a look at the app and scrutinize every little detail they can. There’s a lot of stuff going on in the native libraries for at least the Android version that I wasn’t able to figure out and didn’t have the time to investigate further,” he added.
“TikTok might not meet the exact criteria to be called “Malware”, but it’s definitely nefarious and (in my humble opinion) outright evil,” Bangorlol said. “There’s a reason governments are banning it. Don’t use the app. Don’t let your children use it. Tell your friends to stop using it. It offers you nothing but a quick source of entertainment that you can get elsewhere without handing your data over to the Chinese government. You are directly putting yourself and those on your network (work and home) at risk.”
Also read: Privacy policy template important tips for your business
Also read: 4 easy guides to data breach assessment