KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







A data breach broker is selling a database that allegedly contains 25 million Mathway user records on a dark web marketplace.
Mathway is a calculator that allows users to type in math questions and receive an answer for free through their website or via Android and iOS apps.
The Mathway app is top-rated, with over 10 million installs on Android and ranked as #4 under education in the Apple Store.
Earlier this month, cyber intelligence firm Cyble told BleepingComputer that they were tracking a potential data breach of Mathway after a purported database was being sold in private sales.
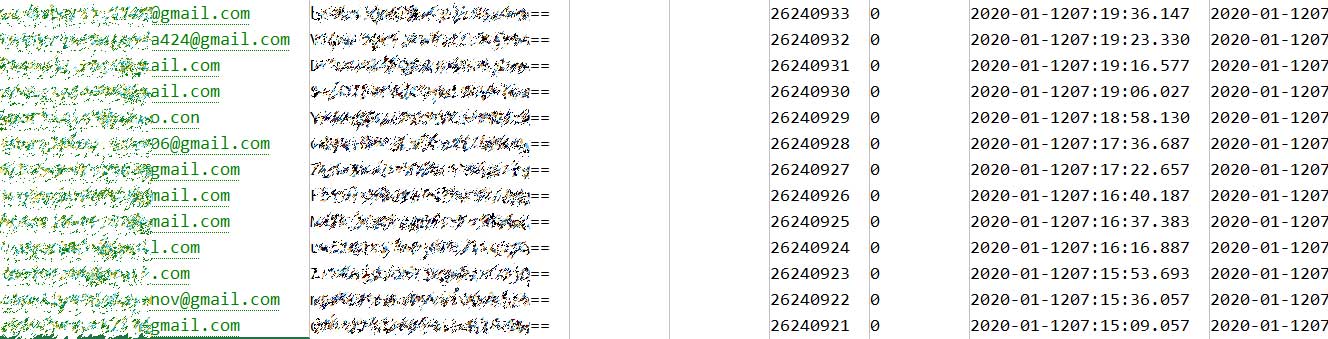
This week, a data breach seller known as Shiny Hunters began to publicly sell an alleged Mathway database on a dark web marketplace for $4,000.Mathway database advertisement
In a sample of the database shared with BleepingComputer, the most concerning of the exposed data are the email addresses and hashed passwords. Otherwise, the data is mostly what appears to be system data.
Mathway told BleepingComputer that they are currently investigating the reports of a data breach.
“We are aware of reports of a potential data compromise. We are working with cybersecurity experts to investigate further, and will take the appropriate steps to ensure the security of customer information.” Mathway said in a statement to BleepingComputer.
In a second email, Mathway told BleepingComputer that they should have more information soon.
If you use Mathway and want to check if your account is part of this breach, you can use Cyble’s AmIBreached data breach lookup service.
To be safe, all Mathway users should also change their password on the site.
If you use this same password at any other site, you should change it to a new unique password at that site as well.
It is suggested that you use a password manager to help keep track of unique and complex passwords at every site that you visit.

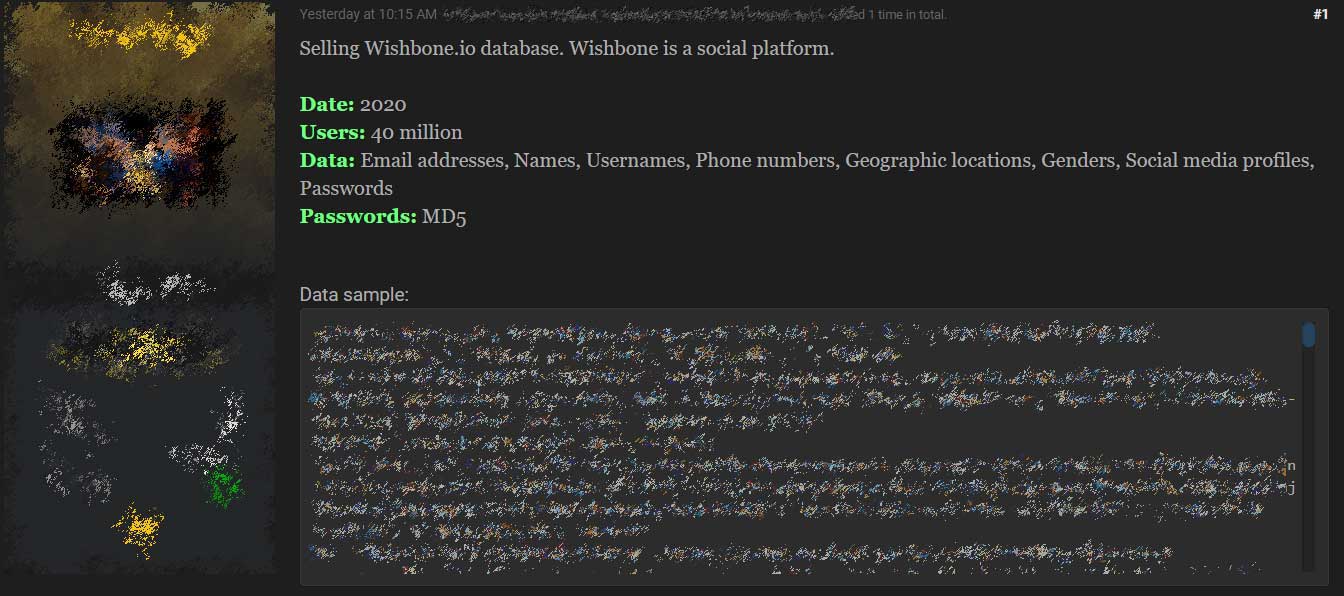
A hacker has leaked 40 million Wishbone user records that contain a treasure trove of information that could be used to perform phishing campaigns, account takeovers, and credential stuffing attacks.
BleepingComputer has been able to independently confirm that the data is legitimate as it contains user records for people we know have used the app and who have confirmed the accuracy of the data.
Wishbone is a popular app for iOS and Android that allows users to create comparisons between two images that people can then vote on.
For weeks, BleepingComputer has been aware of a data breach broker selling an alleged database containing 40 million user records for the Wishbone app through private deals.
According to cyber intelligence firm Cyble, who shared this information with BleepingComputer, the database was circulating privately since March.
Yesterday, a different data breach seller publicly advertised the sale of the Wishbone database on a popular hacker forum where they were selling it for $8,000.
This seller told BleepingComputer in previous conversations that he collects, trades, and buys databases from data breaches and then sells them to others.
We were also told that this database was dumped at the end of January 2020.
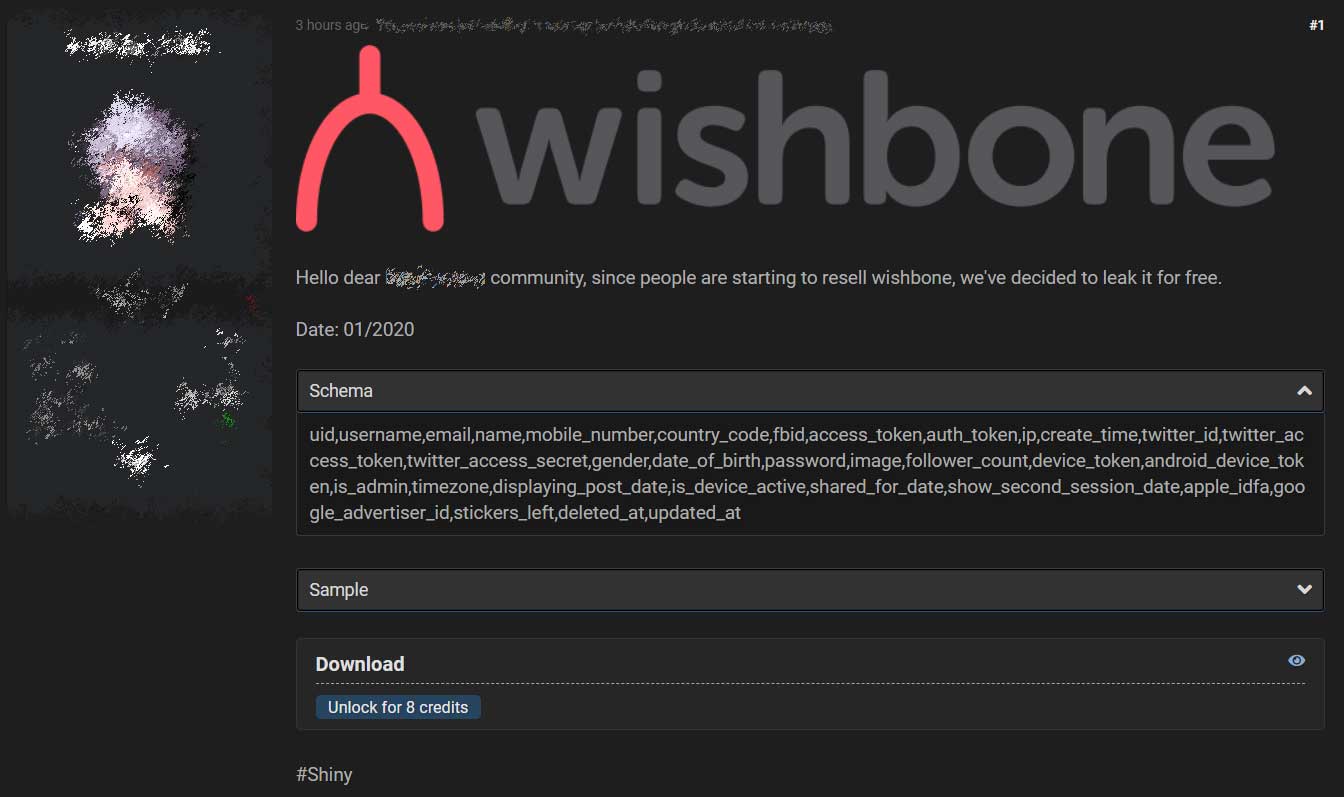
Today, another data breach seller and competitor known as Shiny Hunters, decided to leak the entire database for free on the same hacker forum.
Shiny Hunters have been responsible for the sale of numerous data breaches, including one for Microsoft’s private GitHub repository. Since then, some of these have been confirmed as data breaches by the affected companies.
We can expect to see tensions escalate between the two threat actors as both brokers are known to sell legitimate data.AD
This could lead to other private databases being leaked for free as each tries to spoil the other’s sales.
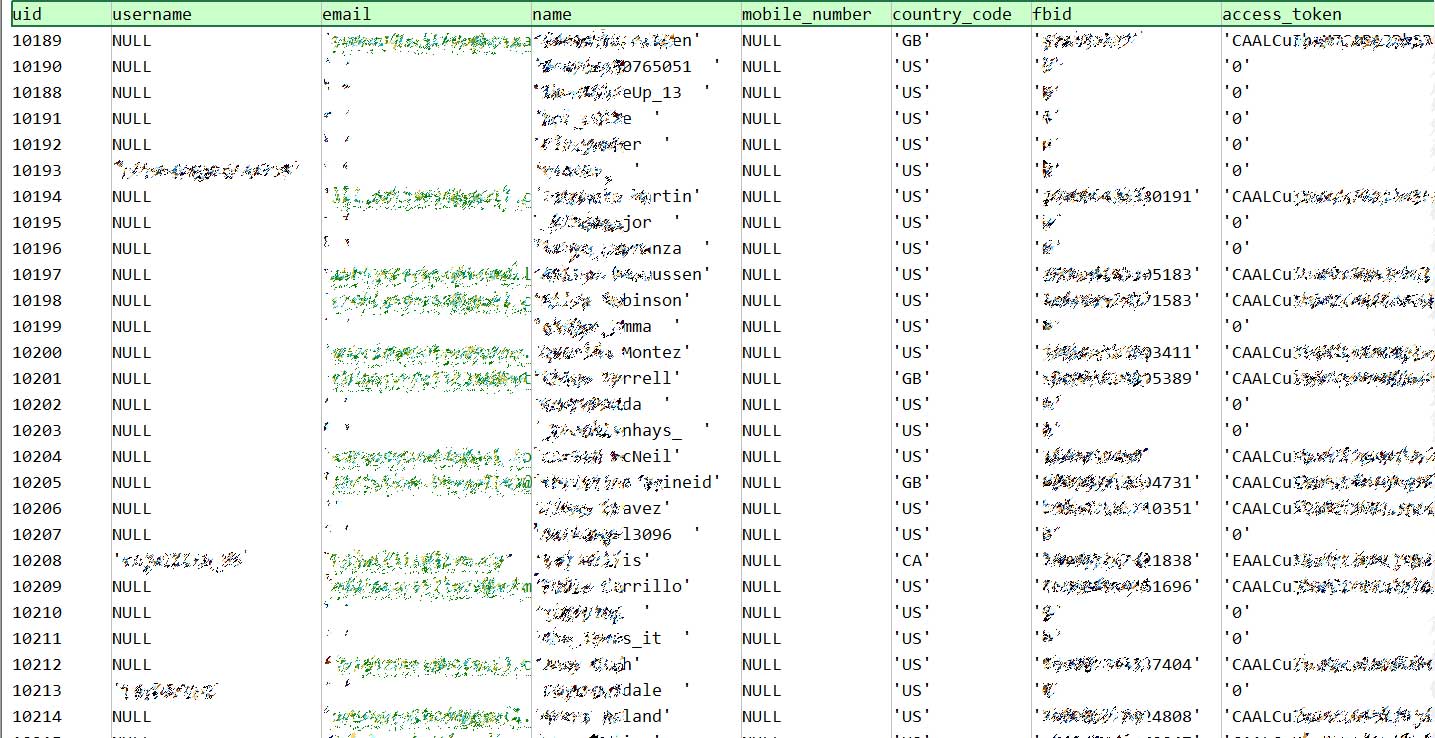
Samples of the Wishbone database have been shared with BleepingComputer that unfortunately contains a great deal of data that can be useful to threat actors.
This exposed data includes usernames, email addresses, hashed MD5 passwords, mobile numbers, Facebook and Twitter access tokens, gender, date of birth, MD5, profile images, and much more.
A full list of the exposed information can be seen in the leaked table structure below:
uid,username,email,name,mobile_number,country_code,fbid,access_token,auth_token,ip,create_time,twitter_id,twitter_access_token,twitter_access_secret,gender,date_of_birth,password,image,follower_count,device_token,android_device_token,is_admin,timezone,displaying_post_date,is_device_active,shared_for_date,show_second_session_date,apple_idfa,google_advertiser_id,stickers_left,deleted_at,updated_at
BleepingComputer has contacted Wishbone with a sample of the data but has not received a response.
Unfortunately, this is typical for companies that we contact to notify of alleged data breaches.
As some of the exposed data in this database file has been confirmed as accurate, it does appear to be a legitimate breach.
Due to this, out of an abundance of caution, I would suggest that all Wishbone users immediately change their passwords on the app.
If they have logged in via Facebook or Twitter, it is also suggested that you disconnect these apps from your Facebook account and Twitter accounts until it is confirmed if the data breach is real.
Finally, if you use your Wishbone password at other sites, you should change it there.
To check if your information was exposed in this database, you can check using Cyble’s AmIBreached data breach lookup service.