KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







With Microsoft temporarily rolling back a feature that automatically blocks macros in Microsoft Office files downloaded from the Internet, it is essential to learn how to configure this security setting manually. This article will explain why users should block macros in Internet downloads and how you can block them in Microsoft Office.
A common distribution method used by some of the most notorious malware, including Emotet, Dridex, Qbot, and RedLine stealer, is to send phishing emails containing malicious Word or Excel documents with macros that install the malware on the target’s devices.
To prevent this distribution method, Microsoft announced in February that Microsoft Office would automatically block VBA macros in documents downloaded from the Internet starting in June.
This announcement was met with resounding support from many Windows admins, cybersecurity professionals, and end-users who saw it as having a significant impact on the security of Windows.
However, soon after the feature went live in June, Microsoft suddenly and without any real explanation rolled back this change, leaving Windows and Microsoft Office users once again at risk from Office documents with malicious macros.
While the rollback is only temporary until customer concerns are addressed, the good news is that you can manually enable this feature on your devices using group policies.
Also Read: The DNC Registry Singapore: 5 Things You Must Know
Before we explain how to automatically block macros in Microsoft Office files downloaded from the Internet, it is essential to understand a Windows feature called the ‘Mark-of-the-Web’.
The Mark-of-the-Web is a special NTFS alternate data stream added to downloaded files that tells Windows and supporting applications, such as Microsoft Office, that the file was downloaded from the Internet and should be considered risky to open.
When a file has a Mark-of-the-Web, and you try to open it, Windows will display additional warnings to the user, asking if they are sure they wish to run the file.
Microsoft Office will also check for a Mark-of-the-Web, and if found, open the document in Protected View, warning that the document can contain viruses.
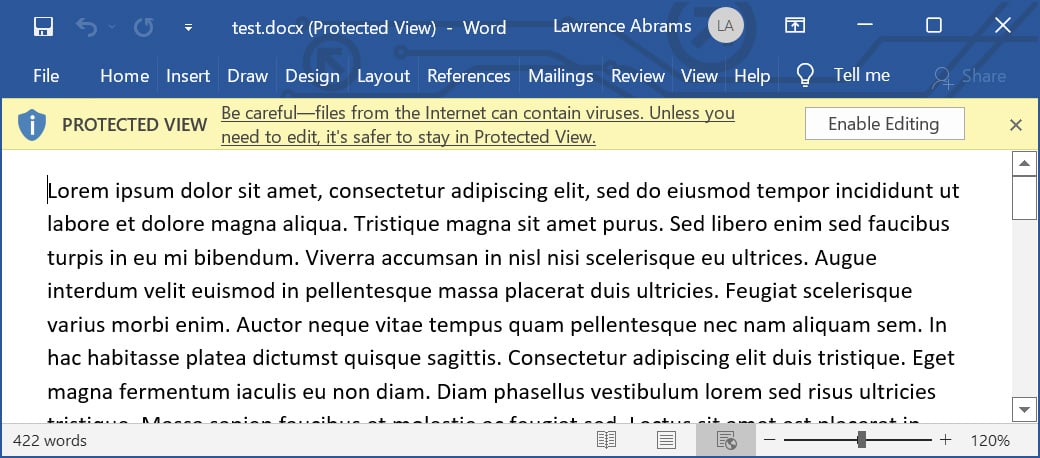
However, if you have ever managed Windows devices, you will know that these warnings are commonly ignored, leading to a device becoming infected and a network becoming compromised.
Since 2016, Microsoft has had a Microsoft Office group policy called ‘Block macros from running Office files from the Internet that will automatically prevent macros from running on documents containing a ‘Mark-of-the-Web.’
While not as pretty as the new feature that Microsoft rolled back, it performs the same functionality of blocking macros on all downloaded Office documents.
To enable this policy, you can download and install the Microsoft Office group policies and configure the ‘Block macros from running Office files from the Internet’ policy for each application you would like to secure.
These policies are located under User Configuration > Administrative Templates > [Office Application] > [Office Application] Options > Security > Trust Center, as shown below.
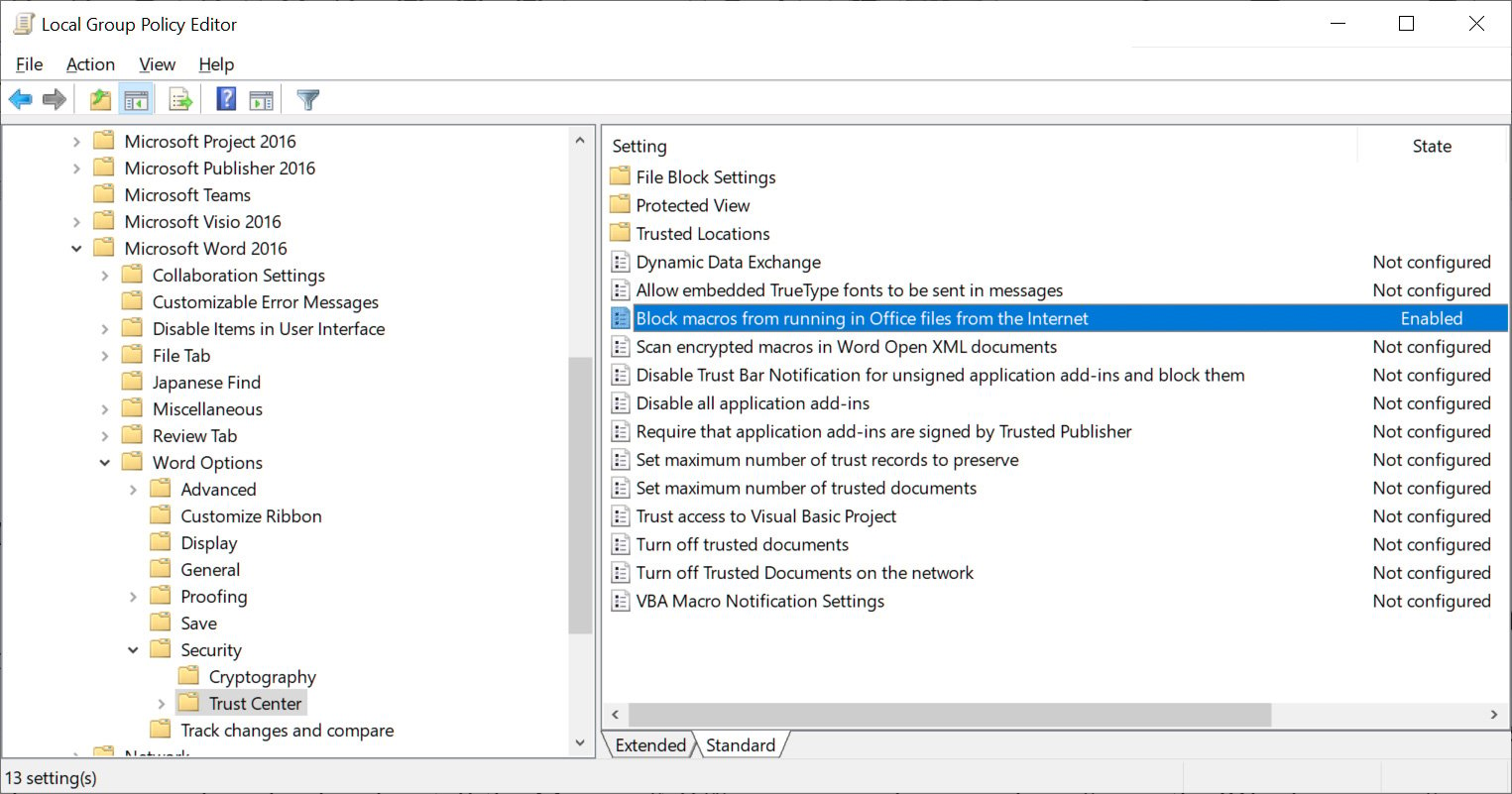
To automatically block macros in Microsoft Office files downloaded from the Internet, navigate to the ‘Block macros from running Office files from the Internet’ policy for the application you want to secure and set the policy to Enabled.
Also Read: How To Comply With PDPA: A Checklist For Businesses
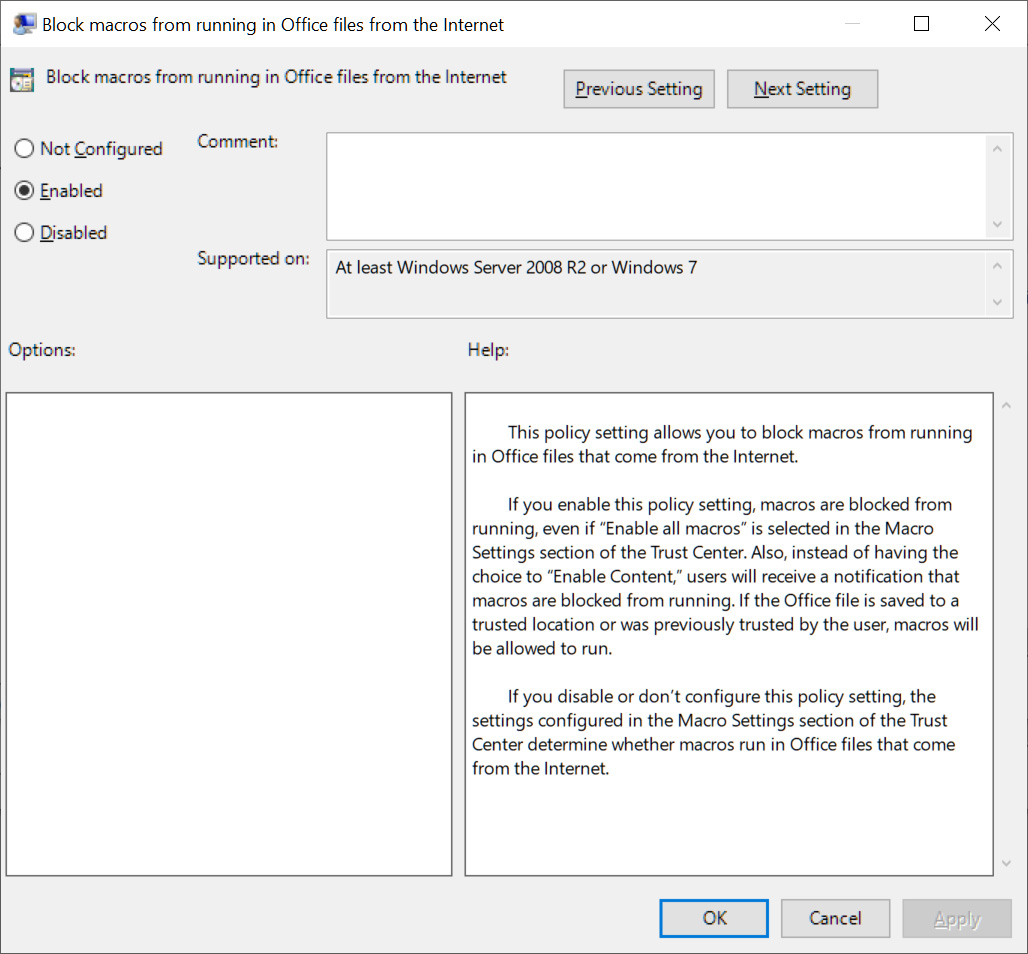
Once this policy is enabled, a new Registry value named ‘blockcontentexecutionfrominternet‘ will be set to ‘1‘ under the HKEY_CURRENT_USER\SOFTWARE\Policies\Microsoft\office\[office version]\[office application]\security key.
For example, when configuring this policy for Microsoft Word, Windows will create the following Registry value:
Windows Registry Editor Version 5.00
[HKEY_CURRENT_USER\SOFTWARE\Policies\Microsoft\office\16.0\word\security]
“blockcontentexecutionfrominternet”=dword:00000001
With this policy enabled, when you attempt to open a Word document with macros that were downloaded from the Internet and enable macros, and you disabled Protected View, you will see a warning stating, “BLOCKED CONTENT Macros in this document have been disabled by your enterprise administrator for security reasons.”
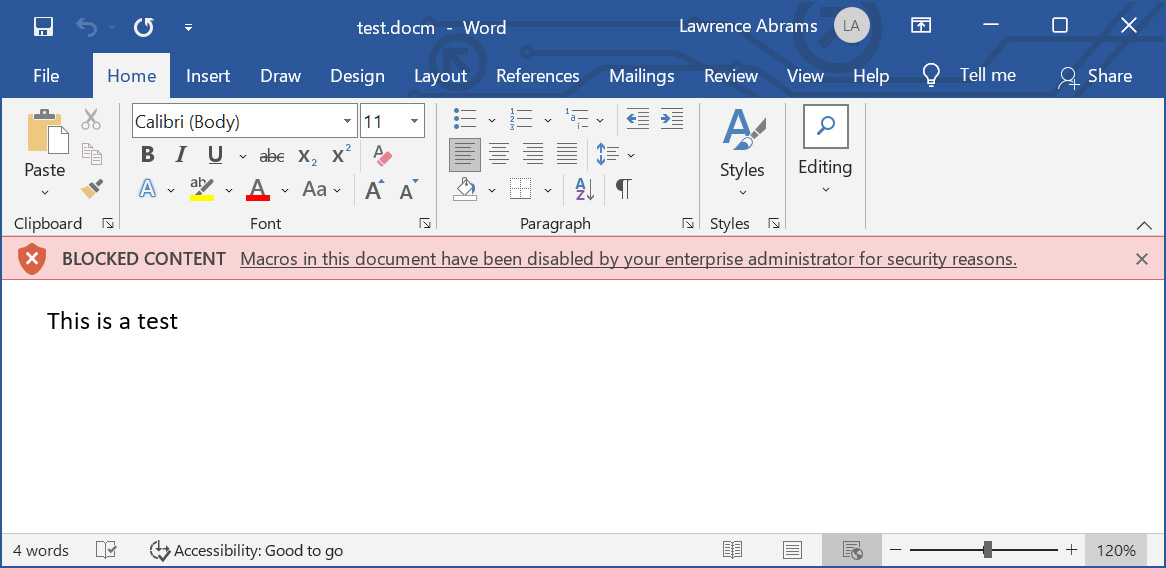
If you trust this document and know it is safe, you can remove the Mark-of-the-Web by going into the file’s properties, clicking the Unblock button in the security section, and then press the Apply button, as shown below.
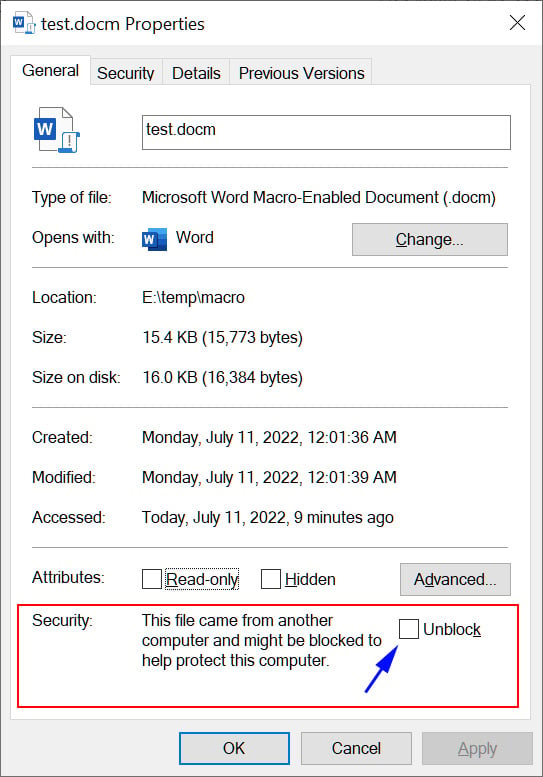
Once you Unblock the file, or remove its Mark-of-the-Web, macros can once again be executed when you open that particular document.
It needs to be reiterated that you should only remove the Mark-of-the-Web from documents you know are 100% trustworthy.
With this policy, you can now achieve the same level of protection as Microsoft’s rolled-back feature. Furthermore, if your organization has a problem blocking all Macros, it is possible to configure ‘Trusted Locations’ where users can save documents and not have macros blocked.
Microsoft also provides various documentation on configuring this policy and creating Trusted Locations, which are recommended to be read by all Windows admins.