KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Threat actors can take advantage of a weakness that affects Microsoft Defender antivirus on Windows to learn locations excluded from scanning and plant malware there.
The issue has persisted for at least eight years, according to some users, and affects Windows 10 21H1 and Windows 10 21H2.
Like any antivirus solution, Microsoft Defender lets users add locations (local or on the network) on their systems that should be excluded from malware scans.
People commonly make exclusions to prevent antivirus from affecting the functionality of legitimate applications that are erroneously detected as malware.
Also Read: The Importance of Data Protection Management System (DPMS)
Since the list of scanning exceptions differs from one user to another, it is useful information for an attacker on the system, since this gives them the locations where they can store malicious files without fear of being detected.
Security researchers discovered that the list of locations excluded from Microsoft Defender scanning is unprotected and any local user can access it.
Regardless of their permissions, local users can query the registry and learn the paths that Microsoft Defender is not allowed to check for malware or dangerous files.
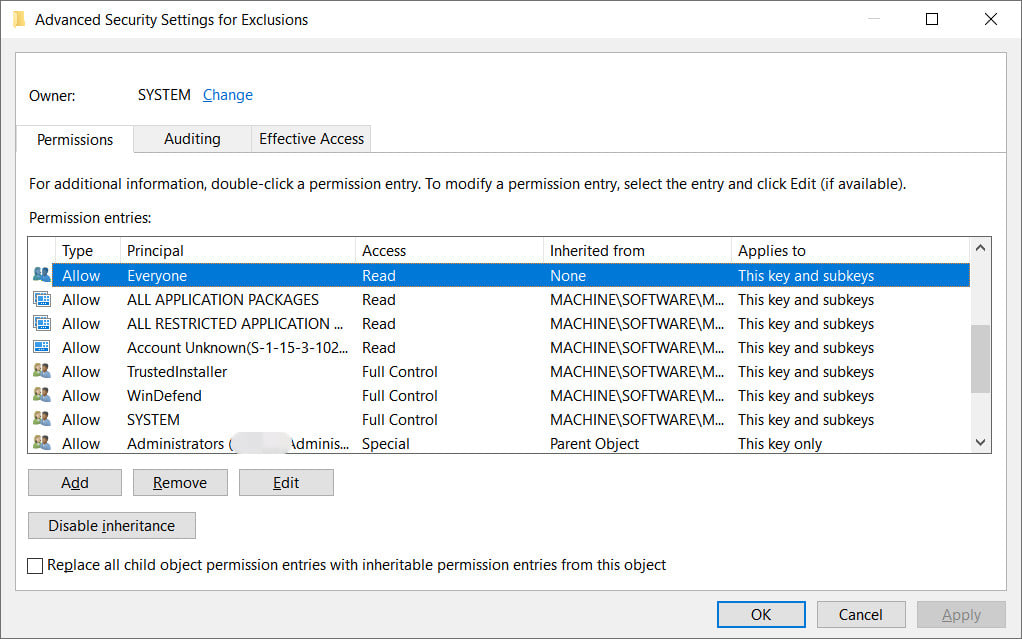
Antonio Cocomazzi, a SentinelOne threat researcher who is credited for reporting the RemotePotato0 vulnerability, points out that there is no protection for this information, which should be considered sensitive, and that running the “reg query” command reveals everything that Microsoft Defender is instructed not to scan, be it files, folders, extensions, or processes.
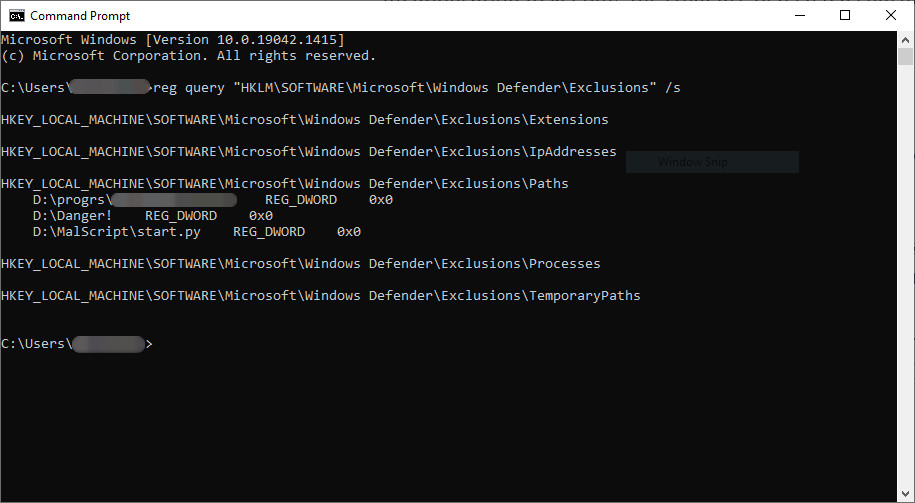
Another security expert, Nathan McNulty, confirmed that the issue is present on Windows 10 versions 21H1 and 21H2 but it does not affect Windows 11.
McNulty also confirmed that one can grab the list of exclusions from the registry tree with entries that store Group Policy settings. This information is more sensitive as it provides exclusions for multiple computers.
A security architect versed in protecting the Microsoft stack, McNulty warns that Microsoft Defender on a server has “automatic exclusions that get enabled when specific roles or features are installed” and these do not cover custom locations.
Although a threat actor needs local access to get the Microsoft Defender exclusions list, this is far from being a hurdle. Many attackers are already on compromised corporate networks looking for a way to move laterally as stealthily as possible.
By knowing the list of Microsoft Defender exclusions, a threat actor that already compromised a Windows machine can then store and execute malware from the excluded folders without fear of being spotted.
Also Read:
In tests done by BleepingComputer, a malware strain executed from an excluded folder ran unhindered on the Windows system and triggered no alert from Microsoft Defender.
We used a sample of Conti ransomware and when it executed from a normal location Microsoft Defender kicked in and blocked the malware.
After placing Conti malware in an excluded folder and running it from there, Microsoft Defender did not show any warning and did not take any action, allowing the ransomware to encrypt the machine.
This Microsoft Defender weakness is not new and has been highlighted publicly in the past by Paul Bolton:
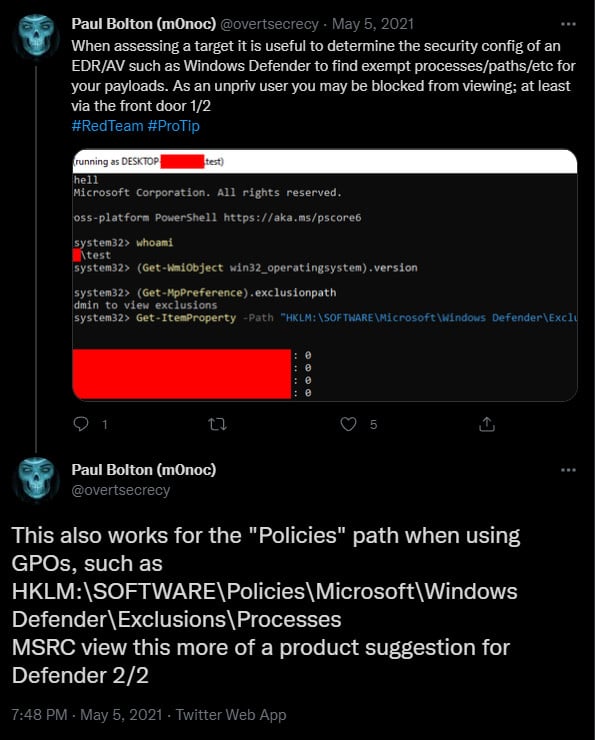
A senior security consultant says that they noticed the issue about eight years ago and recognized the advantage it provided to a malware developer.
“Always told myself that if I was some kind of malware dev I would just lookup the WD exclusions and make sure to drop my payload in an excluded folder and/or name it the same as an excluded filename or extension” – Aura
Given that it’s been this long and Microsoft has yet to address the problem, network administrators should consult the documentation for properly configuring Microsoft Defender exclusions on servers and local machines via group policies.