KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Microsoft has released two out-of-band security updates designed to address remote code execution (RCE) bugs found to affect the Microsoft Windows Codecs Library and Visual Studio Code.
The two vulnerabilities are tracked as CVE-2020-17022 and CVE-2020-17023, both of them being rated as important severity and marked as not being exploited in the wild.
CVE-2020-17022 was reported to Microsoft by Dhanesh Kizhakkinan of FireEye Inc, while CVE-2020-17023 was reported by Justin Steven.
The ‘CVE-2020-17022 | Microsoft Windows Codecs Library Remote Code Execution Vulnerability’ affects all devices running Windows 10, version 1709 or later, and a vulnerable library version.
Also Read: Top 10 Exceptional And Creative Website Design Guidelines
The vulnerability is caused by the way that the Microsoft Windows Codecs Library handles objects in memory and successful exploitation requires a program to process a specially crafted image file.
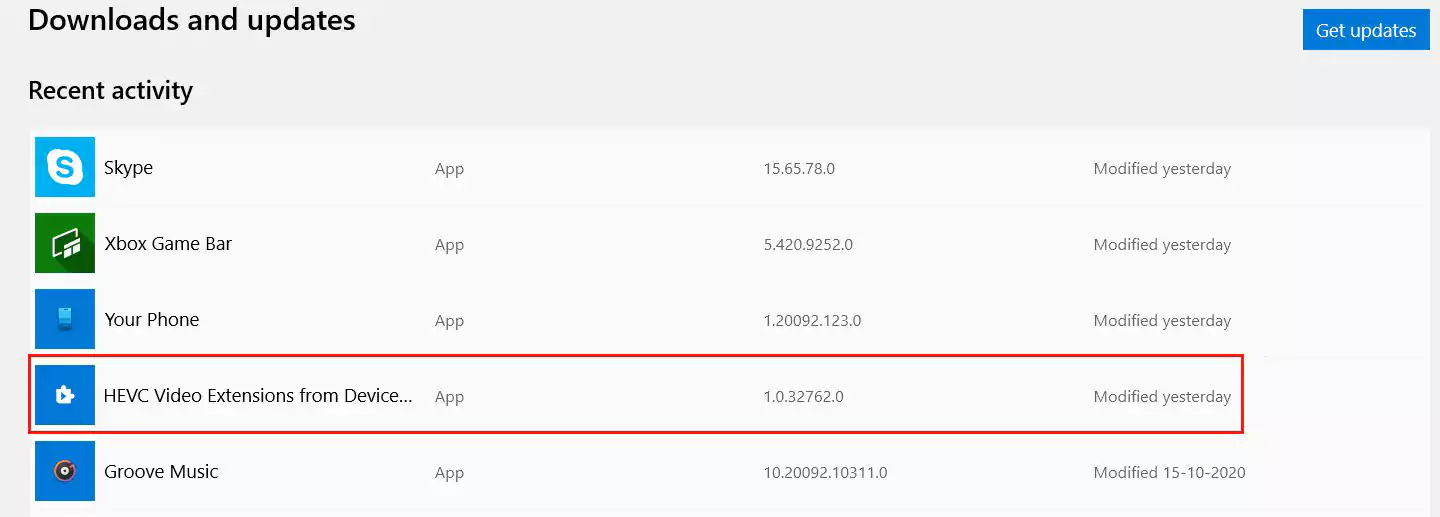
Microsoft says that Windows 10 devices are not vulnerable in their default configuration and that “only customers who have installed the optional HEVC or ‘HEVC from Device Manufacturer’ media codecs from Microsoft Store may be vulnerable.”
Going into Settings > Apps & Features, and selecting HEVC, Advanced Options allows you to check if the codecs have been updated — secure versions are 1.0.32762.0, 1.0.32763.0, and later.
Microsoft patched two similar RCE bugs in June, leading to user confusion because of the ways the security updates were being delivered — via the Microsoft Store instead of the normal Windows Update channel.
The ‘CVE-2020-17023 | Visual Studio JSON Remote Code Execution Vulnerability’ is triggered when users open a maliciously crafted ‘package.json’ file and it allows attackers to remotely execute code in the context of the currently logged-on user.
If the user has administrative rights, successful exploitation also enables attackers to create rogue admin accounts on compromised Windows devices.
Also Read: Data Protection Officer Duties And Responsibilities
CVE-2020-17023 is actually a security update bypass for CVE-2020-16881, another Visual Studio Code RCE bug Microsoft attempted to fix on September 8th as Steven told BleepingComputer.
More info on how the vulnerability works can be found in the Twitter thread embedded below.
Microsoft says that it has not identified any mitigating measures or workarounds for the two vulnerabilities.
Affected customers don’t have to take any action to secure their computers against CVE-2020-17022 since the security update will be automatically delivered to all impacted devices via the Microsoft Store unless automatic updating for Microsoft Store apps is disabled.
“Alternatively, customers who want to receive the update immediately can check for updates with the Microsoft Store App; more information on this process can be found here,” Microsoft explains.
BleepingComputer has reached out to Microsoft for more details but had not heard back at the time of this publication.
Update October 16, 17:00 EDT: Added more info on CVE-2020-17023.