KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







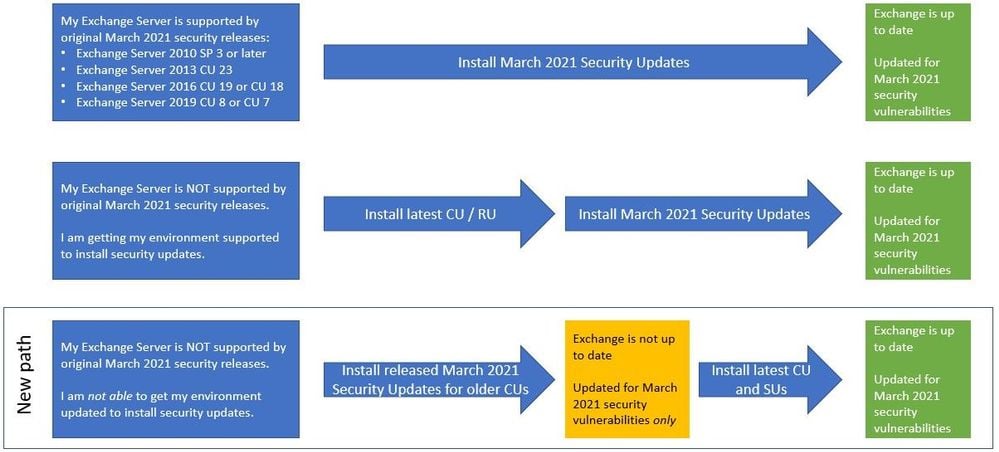
Microsoft has released security updates for Microsoft Exchange servers running unsupported Cumulative Update versions vulnerable to ProxyLogon attacks.
These additional security updates are meant to be installed only on machines running Exchange Server versions not supported by the original Match 2021 security patches released a week ago, only if the admin can’t find an update path to a supported version.
Applying these security updates will only address the Exchange Server vulnerabilities fixed earlier this month (tracked as CVE-2021-26855, CVE-2021-26857, CVE-2021-26858, CVE-2021-27065).
They do not bundle additional product updates or security fixes since they are meant to be quick patches to protect the servers until deploying the latest Exchange updates.
“This is intended only as a temporary measure to help you protect vulnerable machines right now,” the Exchange team said. “You still need to update to the latest supported CU and then apply the applicable SUs.”
Also Read: What You Should Know About The Data Protection Obligation Singapore
These security updates are only available through the Microsoft Download Center, and you can download standalone update packages for servers running:
You must install the downloaded security updates from an elevated command prompt because the updates can install without fixing the vulnerabilities by double-clicking the MSP installers as a normal user.
The full procedure needed to install the updates correctly requires you to go through the following steps:
Once you successfully install these additional updates, you should also make sure to bring your Exchange environment to a supported state by installing the latest available updates as soon as possible.
To be protected after deploying the security updates, you will also have to reboot the server after the installation process ends, even if you will not be prompted.
It’s also important to mention that if you install any other intermediary cumulative updates after these security updates, your Exchange server will once again be vulnerable to ongoing ProxyLogon attacks.
“Our original announcement Released: March 2021 Exchange Server Security Updates contains information and resources that can help you plan your updates, troubleshoot problems, and help you with mitigations, investigation, and remediation of the vulnerabilities,” Microsoft added.
Microsoft has also updated the Microsoft Safety Scanner (MSERT) tool to help customers detect web shells deployed in recent Exchange Server attacks by Chinese-backed state hackers.
Also Read: The Difference Between GDPR And PDPA Under 10 Key Issues
CISA also warned of “widespread domestic and international exploitation of Microsoft Exchange Server vulnerabilities,” urging admins to use Microsoft’s IOC detection tool to detect signs of compromise in their organizations.