KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Microsoft’s threat analysts have uncovered a large-scale, multi-phase phishing campaign that uses stolen credentials to register devices onto the target’s network and use them to distribute phishing emails.
As the report highlights, the attacks manifested only through accounts that didn’t have multi-factor authentication (MFA) protection, which made them easier to hijack.
The threat actor deployed the attacks in two stages, the first one designed to steal the recipient’s email credentials, luring them with DocuSign-themed emails that urged reviewing and signing a document.
Also Read: 10 Best, Secured And Trusted Disposal Contractor In Singapore
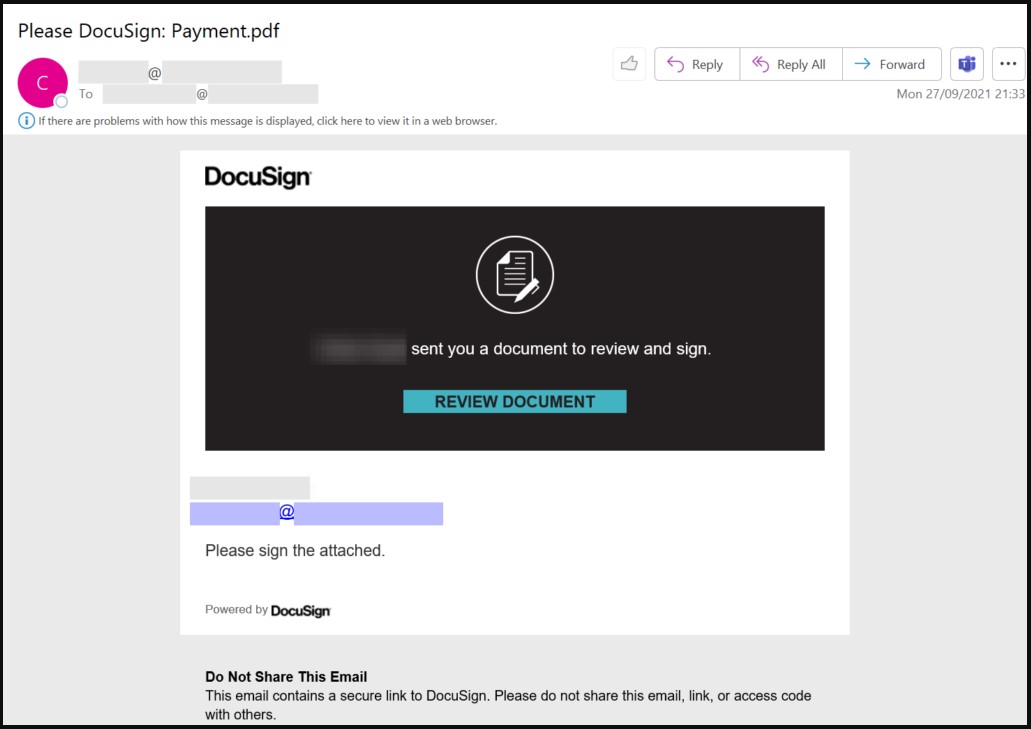
The embedded links take the victim to a phishing URL that imitates the Office 365 login page and pre-fills the victim’s username for increased credibility.
Microsoft’s telemetry data indicates that the first phase of the attacks focused mainly on firms located in Australia, Singapore, Indonesia, and Thailand.
The actors attempted to compromise remote working employees, poorly protected managed service points, and other infrastructure that may operate outside strict security policies.
Microsoft’s analysts were able to spot the threat by detecting anomalous creation of inbox rules, which actors added immediately after gaining control of an inbox to keep out IT notification messages that could trigger suspicions.
“Leveraging the Remote PowerShell connection, the attacker implemented an inbox rule via the New-InboxRule cmdlet that deleted certain messages based on keywords in the subject or body of the email message,” – the report details.
Also Read: 10 Tips For Drafting Key Terms In A Service Agreement
“The inbox rule allowed the attackers to avoid arousing the compromised users’ suspicions by deleting non-delivery reports and IT notification emails that might have been sent to the compromised user.”
The investigation that followed revealed that over a hundred mailboxes in multiple organizations had been compromised with malicious mailbox rules named “Spam Filter”.
With credentials in hand, the attackers installed Outlook on their own machine (Windows 10) and logged into the user’s email account. This action caused the attacker’s device to connect automatically to the company Azure Active Directory and register it.
This was likely due to accepting Outlook’s first launch experience by logging with the stolen credentials, Microsoft notes, adding that a MFA policy in Azure AD would not have allowed the rogue registration.
Once the attacker’s device was added to the organizations network, the threat actor proceeded to the second stage, sending emails to employees of the targeted firm and external targets such as contractors, suppliers, or partners.
.jpg)
Since these messages come from a trusted workspace, they aren’t flagged by security solutions and carry an intrinsic element of legitimacy that boosts the actors’ chances of success.
By registering rogue devices, the threat actor likely hoped to enforce policies that would facilitate lateral phishing.
Azure AD triggers an activity timestamp when a device attempts to authenticate, which was a second opportunity for defenders to discover the suspicious registrations.
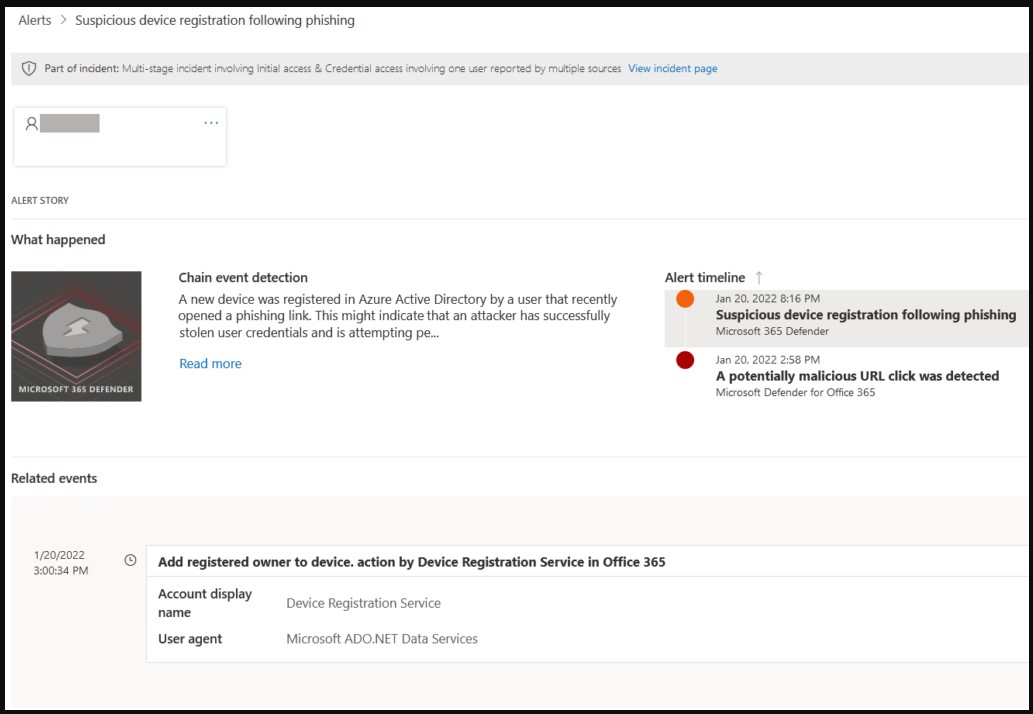
If the registration goes unnoticed, the actors are allowed to send messages from a recognized and trusted part of the domain using the stolen valid credentials on Outlook.
The second wave of phishing messages was much larger than the first, counting over 8,500 SharePoint-themed emails with a “Payment.pdf” attachment.
This phishing campaign was crafty and moderately successful, but it wouldn’t be nearly as effective if the targeted companies followed one of these practices:
Update [January 27, 13:43 EST]: Edited some paragraphs to clarify aspects of the campaign and how it moved from one stage to another.