KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







A creative Office 365 phishing campaign has been inverting images used as backgrounds for landing pages to avoid getting flagged as malicious by crawlers designed to spot phishing sites.
These inverted backgrounds are commonly used as part of phishing kits that attempt to clone legitimate login pages as closely as possible to harvest a target’s credentials by tricking them into entering them into a fake login form.
This tactic has been used by several Office 365 credential phishing sites according to WMC Global analysts who spotted while being deployed as part of the same phishing kit created and sold by a single threat actor to multiple users.
“Because image recognition software is improving and becoming more accurate, this new technique aims to deceive scanning engines by inverting the colors of the image, causing the image hash to differ from the original,” WMC Global explains. “This technique can hinder the software’s ability to flag this image altogether.”

Also Read: Limiting Location Data Exposure: 8 Best Practices
The tricky part that makes this detection evasion method viable is that potential victims would immediately notice the unusual inverted image and would instantly become suspicious and, most probably, leave the site immediately.
However, to avoid this, the phishing kit designed to use this novel tactic automatically reverts the backgrounds using Cascading Style Sheets (CSS) to make them look just like the original backgrounds of the Office 365 login pages they are trying to mimic.
The targets that get redirected to one of these phishing landing pages will see the original background instead of the inverted image backgrounds that the web crawlers will be served with.
Using this tactic allows the phishing kit to display different versions of the same phishing landing page to victims and scanning engines, effectively hindering the latters’ attempts to detect the website it’s deployed on as a malicious site.
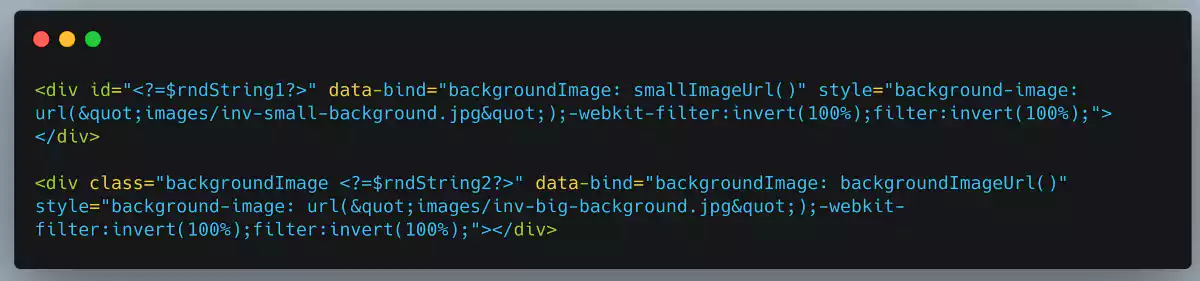
It’s also important to mention that this image inversion tactic was observed within an actively used Office 365 credential phishing kit according to WMC Global’s analysts.
“Our team reviewed other campaigns deployed by this threat actor, discovering that the individual was using the same inversion technique on the newer Office 365 background,” they further explain.
Also Read: 10 Practical Benefits of Managed IT Services
Earlier this year, another Office 365 phishing campaign made use of CSS tricks to bypass Secure Email Gateways (SEGs) by reversing text in a phishing emails’ HTML code to fill the email gateways’ Bayesian statistical models.
Other phishing campaigns targeting Office 365 users have also used innovative techniques such as testing the stolen login in real-time, abusing Google Ads to bypass secure email gateways, as well as Google Cloud Services, Microsoft Azure, Microsoft Dynamics, and IBM Cloud to host the phishing landing pages.