KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Microsoft has released a PowerShell script that admins can use to check whether the recently disclosed ProxyLogon vulnerabilities have hacked a Microsoft Exchange server.
On March 2nd, Microsoft released out-of-band emergency security updates to fix four zero-day vulnerabilities actively used in attacks against Microsoft Exchange. These vulnerabilities are tracked as CVE-2021-26855, CVE-2021-26857, CVE-2021-26858, CVE-2021-27065.
When chained together, these vulnerabilities are known as ‘
ProxyLogon‘ and allow the threat actors to perform remote code execution on publicly exposed Microsoft Exchange servers utilizing Outlook on the web (OWA).
As part of these attacks, the threat actors installed web shells that allowed the attackers to control the server and access the internal network.
These attacks have been attributed to a China state-sponsored hacking group known as HAFNIUM.
Also Read: Website Ownership Laws: Your Rights And What These Protect
When disclosing these vulnerabilities, Microsoft provided a list of commands that Exchange administrators could use to check if a server was hacked.
These commands would need to be executed manually to check for indicators of compromise (IOC) in Exchange HttpProxy logs, Exchange log files, and Windows Application event logs.
Yesterday, Microsoft released a PowerShell script on the Microsoft Exchange support engineer’s GitHub repository named Test-ProxyLogon.ps1 to automate these tasks for the administrator.
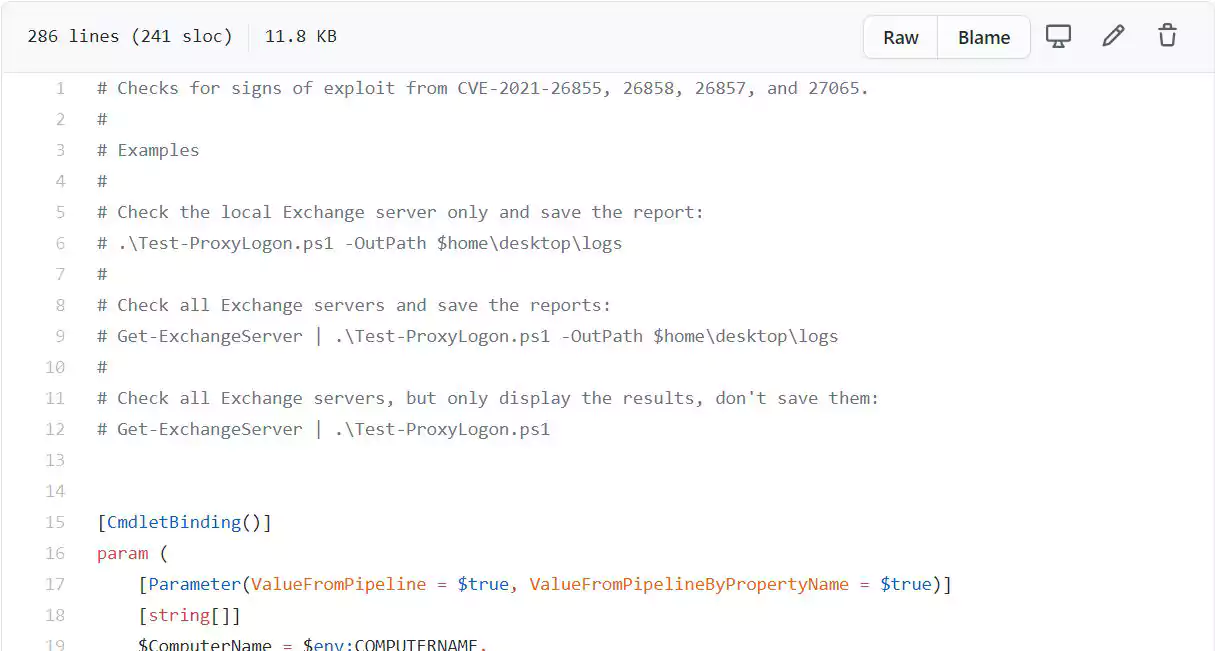
Microsoft provides the following instructions on using the script to check a single Microsoft Exchange server or all servers in your organization.
To check all Exchange servers in your organization and save the logs to the desktop, you would enter the following command from Exchange Management Shell:
Get-ExchangeServer | .\Test-ProxyLogon.ps1 -OutPath $home\desktop\logsIf you only want to check the local server and save logs, you would enter the following command:
.\Test-ProxyLogon.ps1 -OutPath $home\desktop\logsFinally, to only test the local server and display the results without saving them, you can run the following command:
.\Test-ProxyLogon.ps1The US Cybersecurity and Infrastructure Security Agency (CISA) strongly recommends that all organizations utilize this script to check if their servers have been compromised.
“CISA is aware of widespread domestic and international exploitation of these vulnerabilities and strongly recommends organizations run the Test-ProxyLogon.ps1 script—as soon as possible—to help determine whether their systems are compromised,” CISA advises in a new advisory.
Also Read: Computer Misuses Act Singapore: The Truth And Its Offenses
Furthermore, as it has been reported that over 30,000 Exchange Servers have been compromised in this attack, all organizations must prioritize installing the new Exchange security updates and ensuring they have not been targeted in these attacks.