KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!



Whether you are crunching office works or doing personal stuff, cyberthreats lurk in your computer, waiting for the perfect opportunity to attack. Several malwares may be straightforward in infiltrating your system but other scams are often hidden in deceitful innocent forms. To help you protect your private data and sensitive correspondence, here are the five signs of phishing in email to watch out for.
Last July 10, a new phishing scam surfaced in Singapore which contributed to 374 reported cases involving losses that totaled to about $1.07 million. In fact, records from police authorities has revealed that more than S$201 million worth of amount was cheated through top 10 scam types in 2020. This shows that phishing has become extremely rampant as ever.
Phishing is a method used by criminals to fraudulently obtain your private personal data and/or banking information. This may include a wide variety of ways depending on the scheme launched by the perpetrators. In essence, they disguise themselves as a legitimate individual who offers you a promo, product, or service through email, instant messaging, and other online correspondence. Once they obtain your private information, the cybercriminals will use it to access your online profiles to perpetuate further fraudulent acts, or worse, drain your financial channels.
As these criminals become more and more creative on formulating their scam, it is important that you stay vigilant, especially on every business organization’s primary mode of correspondence- your email.
Read More: Personal Data Protection Act Singapore: Is Your Business Compliant?
1. Unexpected emails
These cybercriminals usually send broadcast emails to a large populace to increase their batting average. It makes sense as the more person you send a random message thereto, the more chance of having some people respond. If you receive an unanticipated email, always check the time it was sent to you. Unexpected emails usually come on wee hours, especially those sent by criminals who send broadcast phishing message internationally.
It is also a good practice to check if the message is from one of your contacts. If not, exercise caution as you open the email.
2. Public email domain
Emails that contain business opportunities or transactions are legitimately sent by representatives through official company emails. If you receive dubious emails that ends with public domain, e.g., @gmail.com, this may be a phishing scam. Take a look at this example:
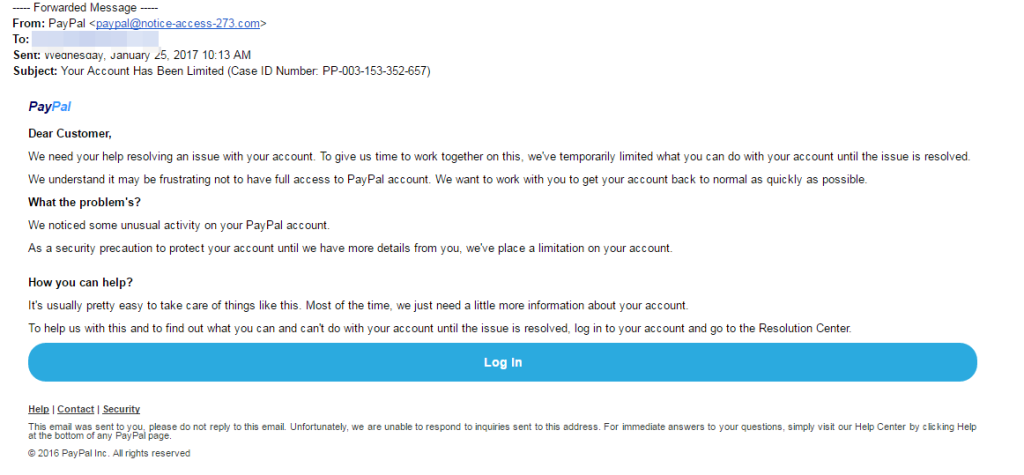
Most duly registered business organizations, except for some small startups, will have their own company email domain and accounts. Example of which is how Google’s official correspondence ends with @google.com.
The most effective way to verify the email’s legitimacy is to visit the company website and check if their “Contact Us” or “About Us” section contains an official company domain that matches the sender’s.
3. Suspicious Attachments
If you receive an email that commands you to download a certain file attached, this is one of the most common signs of phishing. The file attachment serves as the “payload”, which once downloaded, unleashes malware to your computer system and leach off your private information. See example below:
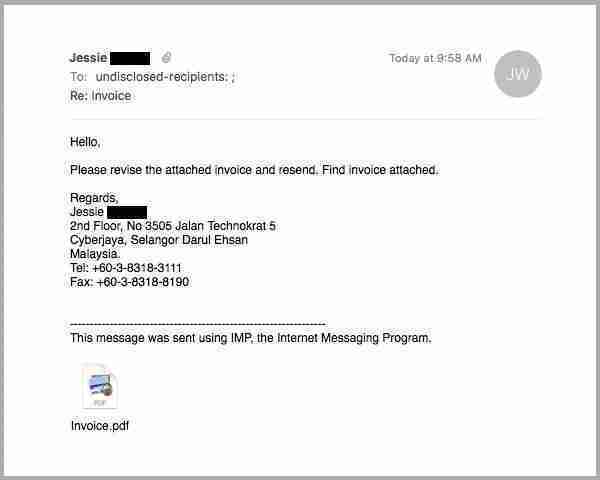
If you receive some sort of pop-up warning from your browser, or if your application prompts you to adjust your security settings, it may be best to not proceed on downloading the attachment. You should contact the sender’s company through other methods and verify if the email (and file attached) is legitimate.
4. Promise of Reward
Misleading offers of too-good to be true deals and prizes are one of the most common signs of phishing sent to private individuals. Usually, these messages creates a sense of urgency and commands you to act immediately; whether to click a certain button or complete a survey.
If an email tells you that by simply following a link can you get you a free cruise-trip around Europe, it is safe to assume that it is a phishing scam.

5. Asking for your private information
Lastly, one of the signs of phishing scams is an email that asks you to provide your login credentials for a certain account. All duly registered business organizations are fully aware that these type of confidential information should not be sent over the internet.
If the email sender claims to be from your bank and requests for your banking details, you should be cautious. Never release any confidential info without first clarifying with the bank through a quick phone call. Should they confirm that they have indeed intended to contact you, inform them that you are not comfortable in releasing your information via email and would prefer to transact on the phone or through personal appearance.
Nowadays, cybercriminals are coming up with more sophisticated schemes on how to steal your private information. Although phishing has been a constant threat to cybersecurity, it is one of the most easiest ploy to crack. All you need to do is to watch out for signs of phishing and exercise your best judgment on whether an email is legitimate or not. An extensive research works best, but in most situations, your common sense would suffice.
Also Read: How Does Ransomware Work? Examples and Defense Tips
Protecting personal data that the organisation manages is the primary duty that must be upheld, or else risk the financial penalty imposed by the PDPC in case of a breach. To help organisations with their data protection compliance, they can outsource a DPO, which is an officer responsible for ensuring that all data protection provisions are complied with at all times.
A DPO is responsible for ensuring that there are policies set up in place when it comes to clicking unexpected emails which may contain malicious links. Since employees are the target of bad actors, a DPO can ensure that they are well aware of the risks of clicking attachments in the email that could infiltrate the organisation’s system.