KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







FIN11, a financially-motivated hacker group with a history starting since at least 2016, has adapted malicious email campaigns to transition to ransomware as the main monetization method.
The group runs high-volume operations, lately targeting companies primarily in North America and Europe from almost every industry sector to steal data and to deploy Clop ransomware.
Malicious campaigns in the early history of the gang focused on organizations in the financial, retail, and restaurant sector. Over the past couple of years, FIN11’s attacks are more indiscriminate both in terms of the victim type and geography.
Starting August, the cybercriminals attacked organizations in the defense, energy, finance, healthcare/pharmaceutical, legal, telecommunications, technology, and transportation sectors.
Security researchers at FireEye’s Mandiant told BleepingComputer that FIN11 targeted its victims with malicious emails distributing a malware downloader they track as FRIENDSPEAK.
Also Read: Limiting Location Data Exposure: 8 Best Practices
They used a variety of lures like remittance documents, invoice delivery, or confidential information about company bonuses with malicious HTML attachments to load content (iframe or embed tags) from a likely a compromised website, often with dated content, indicating abandonment.
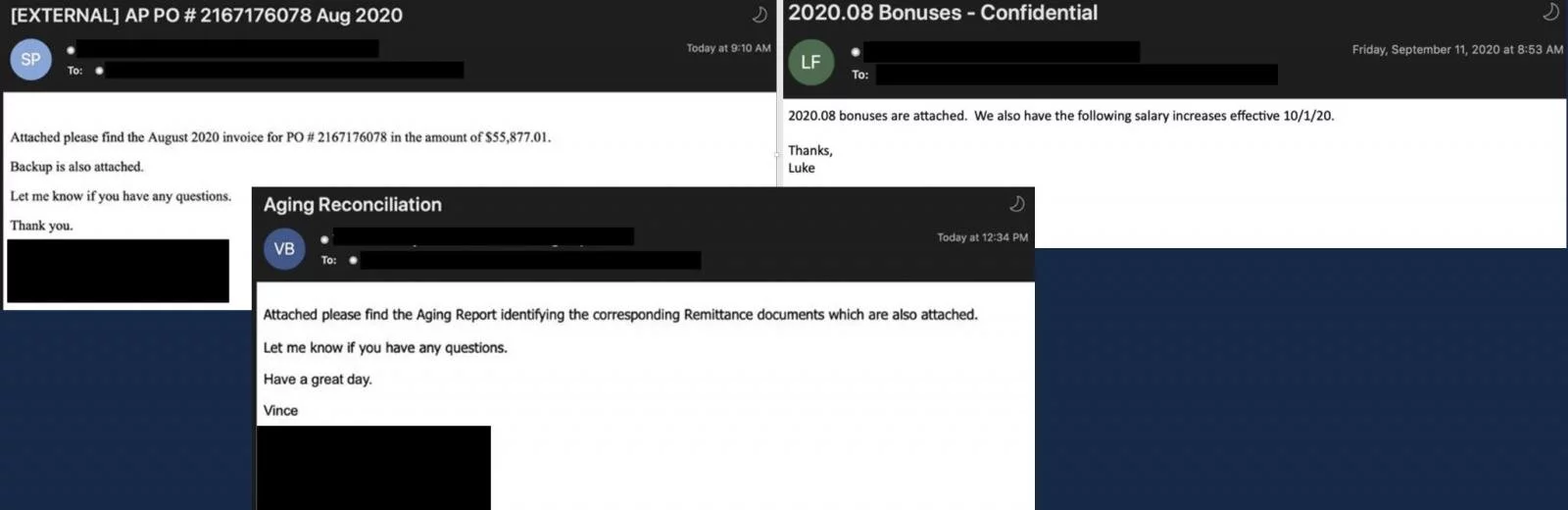
Kimberly Goody, Senior Manager of Analysis at Mandiant Threat Intelligence, told us that victims had to complete a CAPTCHA challenge before being served an Excel spreadsheet with malicious macro code.
Once executed, the code delivered FRIENDSPEAK, which downloaded MIXLABEL, another malware believed to be specific to FIN11. The latter was in many cases configured to contact a command and control domain that impersonated the Microsoft Store (us-microsoft-store[.[com).
These tactics were active in campaigns from September, although the actor modified the macros in Office documents and also added geofencing techniques, Goody said over email.
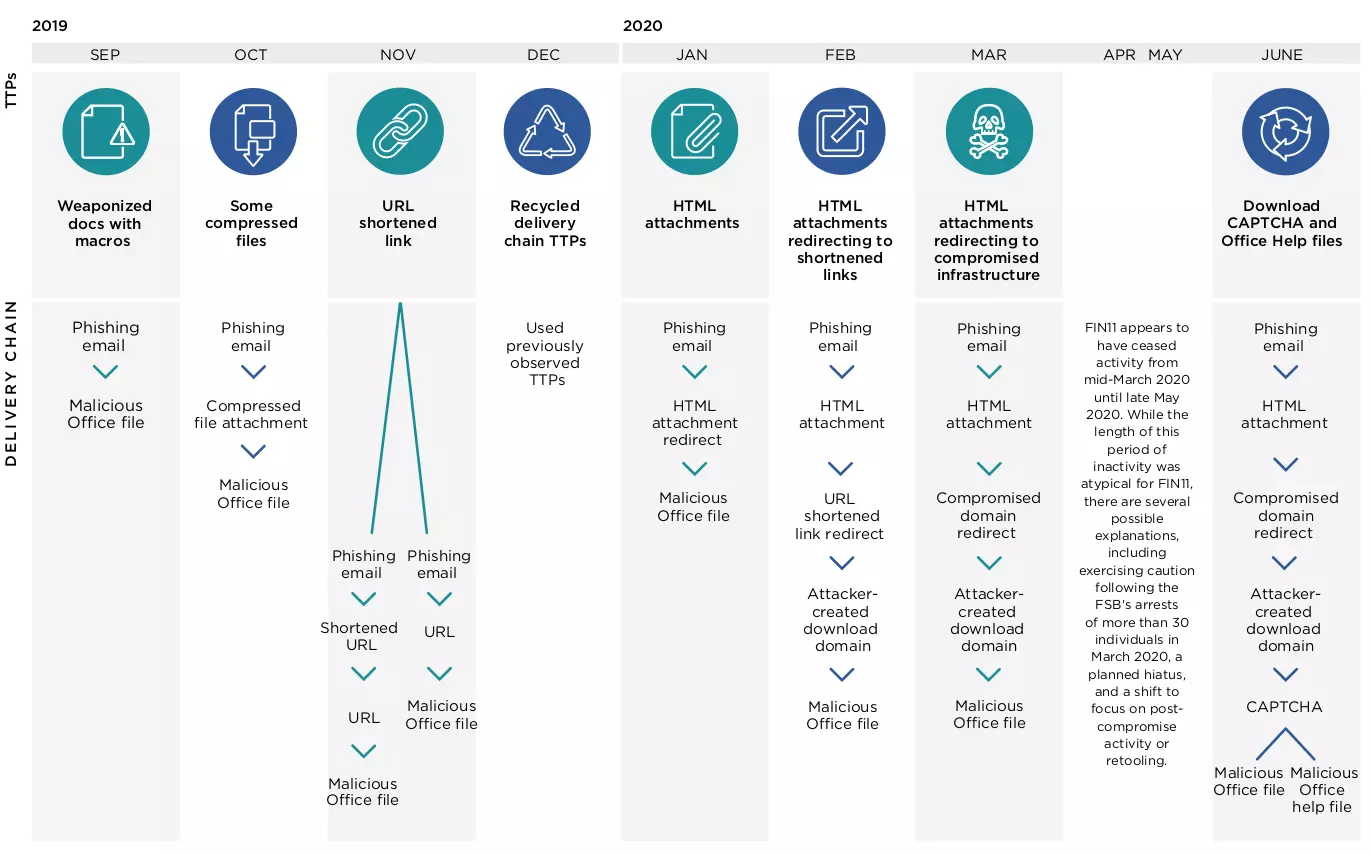
Mandiant today published an overview of the FIN11 activity and its transition to the ransomware scene. The researchers treat the group as a separate threat actor, noting its significant overlap in tactics, techniques, and malware used by TA505.
TA505 is another high-profile cybercriminal gang that deploys Clop ransomware. Recently, it started to exploit the ZeroLogon critical flaw in Windows to get admin-level privileges for a domain controller of an organization.
Distinguishing between the two actors is based on observed activity, and the “evolving arsenal of post-compromise tactics, techniques and procedures (TTPs) that have not been publicly reported on TA505.”
FIN11 also uses FlawedAmmyy, a malware downloader seen in attacks from TA505 and Silence, a group of hackers targeting banks across the world. This indicates that all three groups have a common malware developer.
Despite the strong similarities to TA505, attributing certain campaigns to FIN11 is difficult because both groups use malware and criminal service providers, something that could have led to misattribution in some cases.
Mandiant hass been tracking FIN11 since 2016 and defines it by the observed activity that they can verify independently. TA505 has been around since at least 2014 and the researchers have not attributed its early operations to FIN11.
Also Read: 10 Practical Benefits of Managed IT Services
Responding to incidents where FIN11 dropped Clop ransomware, Mandiant found that the actor did not abandon the target after losing access.
In one case, they re-compromised the organization via multiple email campaigns a few months later. In another, FIN11 regained access after the company restored infected servers from backups.
The researchers do not specify the FIN11 ransom demands from the incidents they investigated but note that ransomware remediation firm Coveware indicates amounts between a few hundred thousand to $10 million.
On one occasion where they did not deploy Clop ransomware, the actor tried to extort the victim threatening with releasing or selling stolen data, Mandiant says.
Based on their analysis, the researchers have moderate confidence that FIN11 operates from the Commonwealth of Independent States (CIS – former Soviet Union countries).
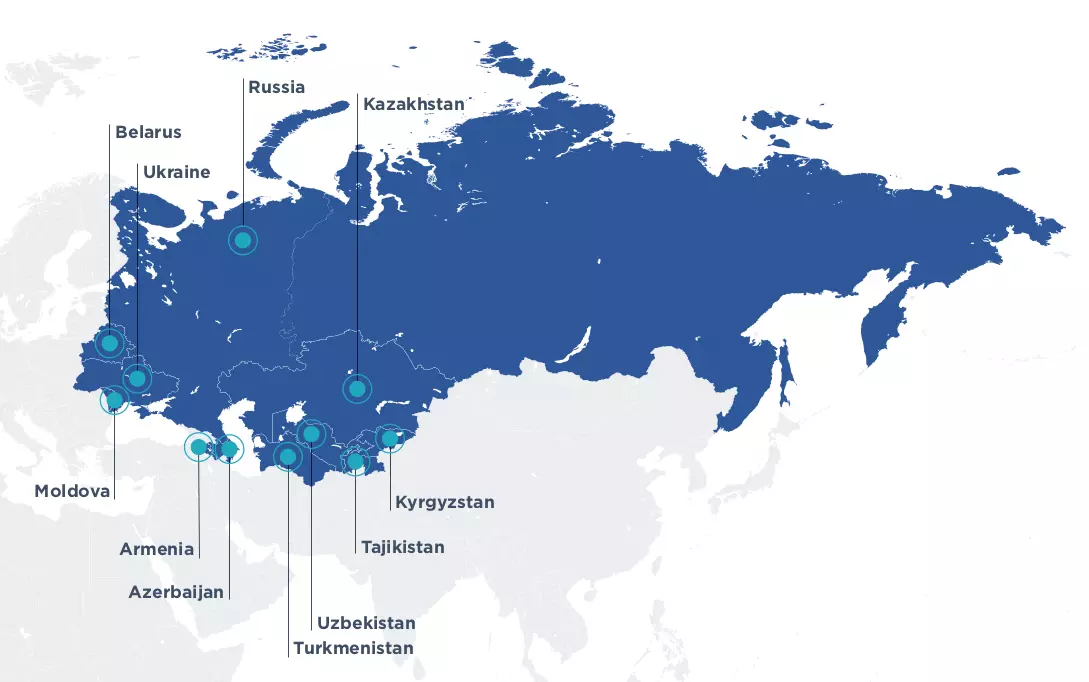
In support of this assessment is Russian-language file metadata, deploying Clop ransomware only on machines with a keyboard layout used outside CIS countries, and a drop in activity during the Russian New Year and Orthodox Christmas holidays.
Mandiant believes that FIN11 has “access to the networks of far more organizations than they are able to successfully monetize” and choose if exploitation is worth the effort based on the location of the victim, their geographical location, and security posture.
Since data theft and extortion are now part of their monetization methods, FIN11 is likely to show more interest in victims that have sensitive proprietary data that have higher odds of paying a ransom either to recover their files.