KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Hackers are luring unsuspecting users with a fake Windows 11 upgrade that comes with malware that steals browser data and cryptocurrency wallets.
The campaign is currently active and relies on poisoning search results to push a website mimicking Microsoft’s promotional page for Windows 11, to offer the information stealer.
Microsoft offers an upgrade tool for users to check if their machine supports the latest operating system (OS) from the company. One requirement is support for Trusted Platform Module (TPM) version 2.0, which is present on machines that not older than four years.
The hackers are preying on users that jump at installing Windows 11 without spending the time to learn that the OS needs to meet certain specifications.
The malicious website offering the fake Windows 11 is still up at the time of writing. It features the official Microsoft logos, favicons, and an inviting “Download Now” button.
.png)
If the visitor loads the malicious website via direct connection – download is unavailable over TOR or VPN, they will get an ISO file that shelters the executable for a novel info-stealing malware.
Also Read: PDPA Singapore Guidelines: 16 Key Concepts For Your Business
Threat researchers at CloudSEK have analyzed the malware and shared a technical report exclusively with BleepingComputer.
According to CloudSEK, the threat actors behind this campaign are using a new malware that researchers named “Inno Stealer” due to its use of the Inno Setup Windows installer.
The researchers say that Inno Stealer doesn’t have any code similarities to commodity other info-stealers currently in circulation and they have not found evidence of the malware being uploaded to the Virus Total scanning platform.
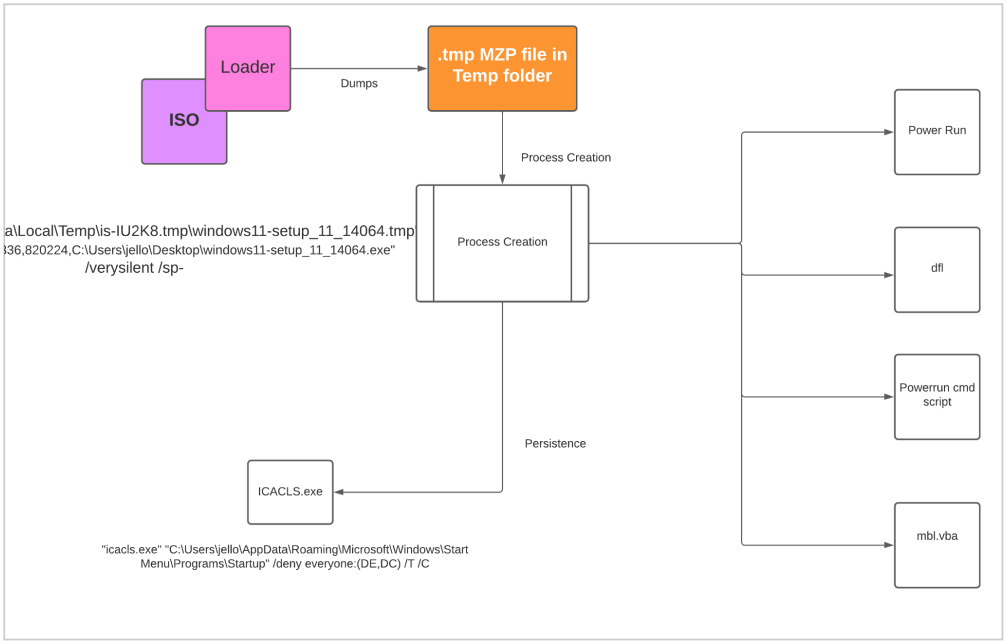
The loader file (Delphi-based) is the “Windows 11 setup” executable contained in the ISO, which, when launched, dumps a temporary file named is-PN131.tmp and creates another .TMP file where the loader writes 3,078KB of data.
CloudSEK explains that the loader spawns a new process using the CreateProcess Windows API the helps spawn new processes, establish persistence, and plant four files.
Persistence is achieved by adding an .LNK (shortcut) file in the Startup directory and using icacls.exe to set its access permissions for stealthiness.
Two of the four dropped files are Windows Command Scripts to disable Registry security, add Defender exceptions, uninstall security products, and delete the shadow volume.
According to the researchers, the malware also removes security solutions from Emsisoft and ESET, likely because these products detect it as malicious.
The third file is a command execution utility that runs with the highest system privileges; and the fourth is a VBA script required to run dfl.cmd.
At the second stage of the infection, a file with the .SCR extension is dropped into the C:\Users\\AppData\Roaming\Windows11InstallationAssistant directory of the compromised system.
Also Read: Data Protection Officer Singapore | 10 FAQs
That file is the agent that unpacks the info-stealer payload and executes it by spawning a new process called “Windows11InstallationAssistant.scr”, the same as itself.
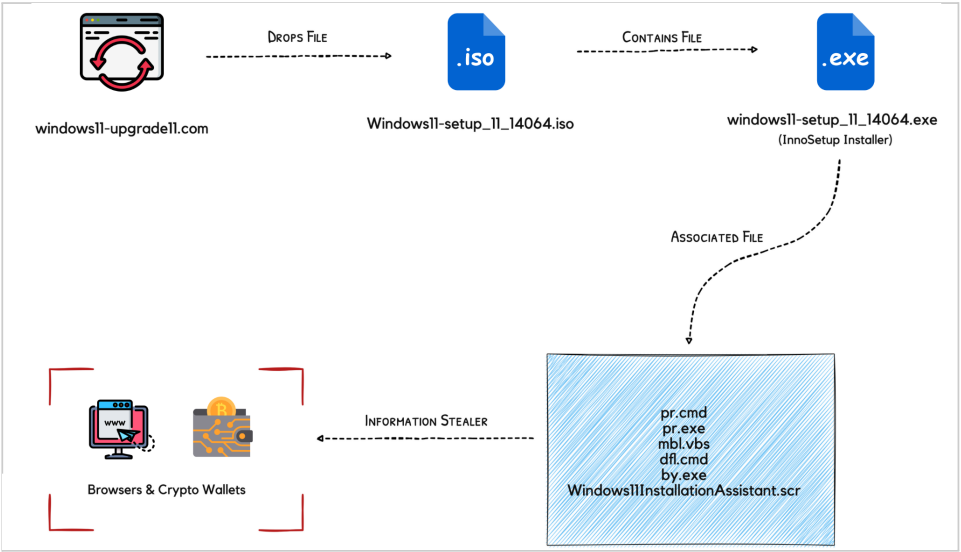
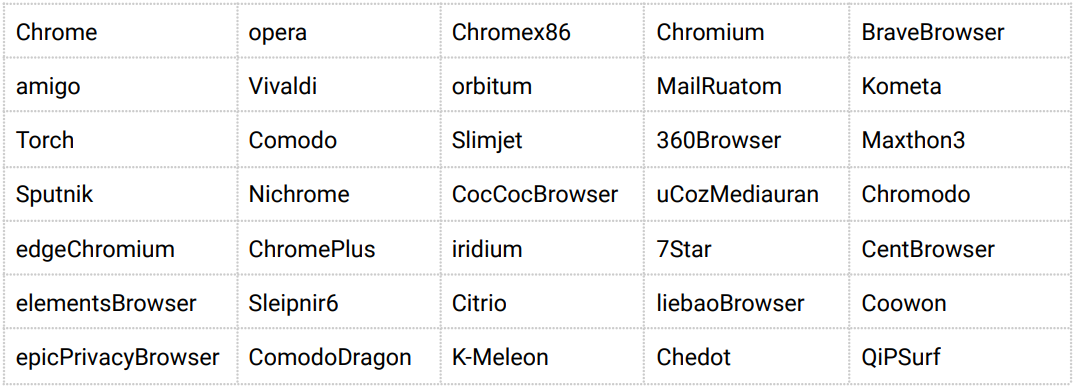
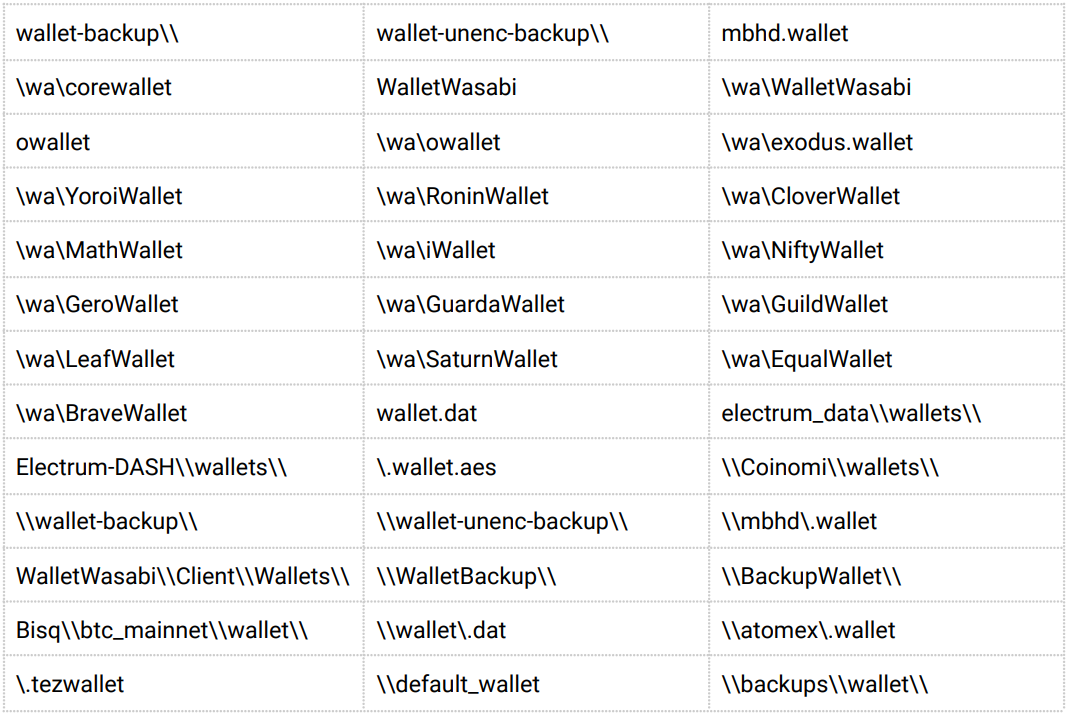
The capabilities of Inno Stealer are typical for this kind of malware, including collecting web browser cookies and stored credentials, data in cryptocurrency wallets, and data from the filesystem.
The set of targeted browsers and crypto wallets is extensive, including Chrome, Edge, Brave, Opera, Vivaldi, 360 Browser, and Comodo.
An interesting characteristic of Inno Stealer is that the network management and the data-stealing functions are multi-threaded.
All stolen data is copied via a PowerShell command to the user’s temporay directory, encrypted, and later sent to the operator’s command and control server (“windows-server031.com”)
The stealer can also fetch additional payloads, an action only performed at night time, possibly to take advantage of a period when the victim is not at the computer.
These additional Delphi payloads, which take the form of TXT files, employ the same Inno-based loader that fiddles with the host’s security tools and use the same persistence-establishment mechanism.
Their extra capabilities include stealing clipboard information and exfiltrating directory enumeration data.
The whole Windows 11 upgrade situation has created a fertile ground for the proliferation of these campaigns, and this is not the first time that something like that has been reported.
It is recommended to avoid downloading ISO files from obscure sources and only perform major OS upgrades from within your Windows 10 control panel or get the installation files straight from the source.
If an upgrade to Windows 11 is unavailable to you, there’s no point attempting to bypass the restrictions manually, as this will come with a set of downsides and severe security risks.