KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Asteelflash, a leading French electronics manufacturing services company, has suffered a cyberattack by the REvil ransomware gang who is demanding a $24 million ransom.
Asteelflash is a world-leading French electronics manufacturing services (EMS) company that specializes in the design, engineering, and printing of printed circuit boards.
While Asteelflash has not publicly disclosed an attack, BleepingComputer found this week a sample of the REvil ransomware that allowed access to the Tor negotiation page for their cyberattack.
This page shows that the REvil ransomware group, also known as Sodin and Sodinokibi, was initially demanding a $12 million ransom, but as the time limit expired, the ransom doubled to $24 million.
Also Read: The Difference Between GDPR And PDPA Under 10 Key Issues
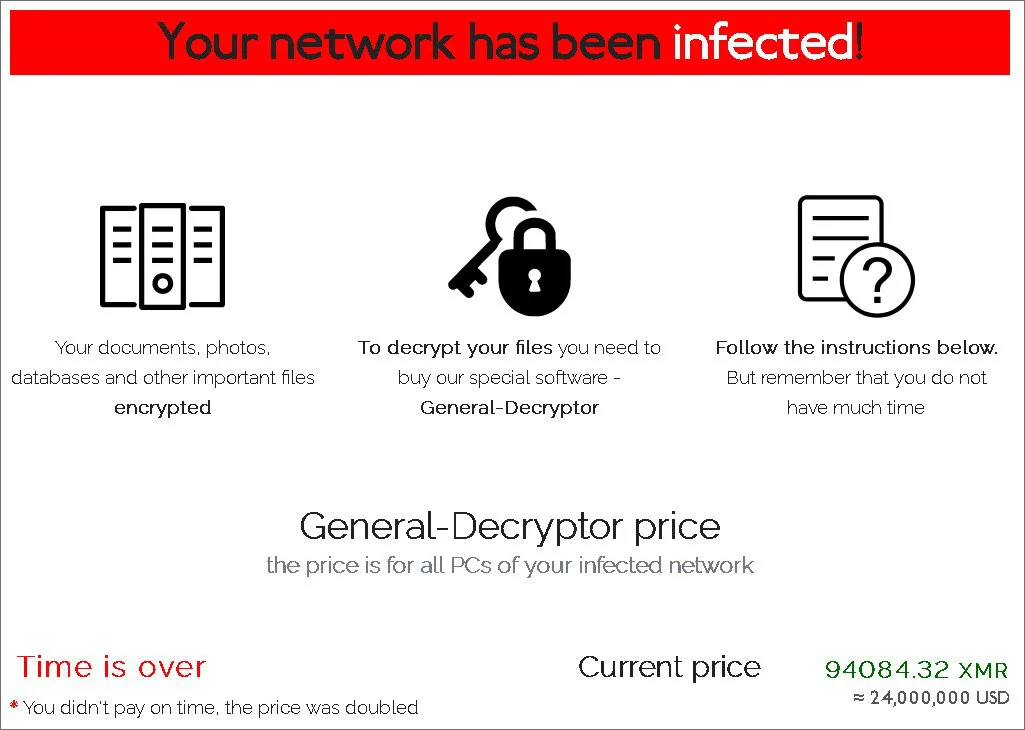
The Tor payment site showed a brief conversation between the REvil threat actors and Asteelflash. As part of this conversation, the threat actors shared a file named ‘asteelflash_data_part1.7z’ that was shared to prove that files were stolen during the attack. Metadata of some of the shared files show that Asteelflash employees authored them.
At this point, the conversation between the two parties has stalled and there are no details about the company’s intentions regarding the ransom.
BleepingComputer has contacted Asteelflash multiple times but has not received a response to our inquiries. LeMagIT had more success, an Asteelflash representative stating for them that the “the incident is being evaluated.”
Neither BleepingComputer nor LeMagIT could confirm whether the attack was successful in encrypting files on affected systems.
Also Read: PDPA Compliance Singapore: 10 Areas To Work On
For more than a year, ransomware gangs started to steal data from their victims before locking the computers. This allows them to extort victims by promising not to publish or sell the information.