KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Malware distributors have turned to an older trick known as Squiblydoo to spread Qbot and Lokibot via Microsoft Office document using regsvr32.exe.
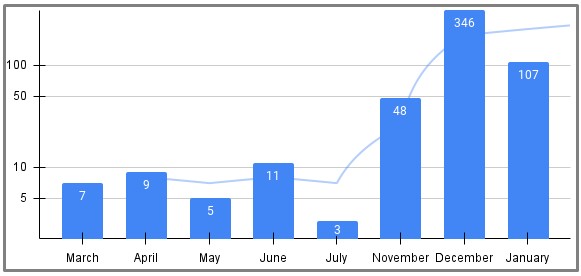
A report from the threat research team at security analytics platform Uptycs shows that the use of regsvr32.exe has been spiking for the past couple of months, occurring via various document formats but mainly Excel files.
The sudden focus this particular command-line utility is explained by the fact that it allows threat actors to bypass application blocklisting that could put an end to the infection chain.
Telemetry data collected from Uptyck’s clients shows that December 2021 was when most incidents of the Windows resident tool abuse were recorded, but the high rates continued in 2022.
Also Read: What a Vulnerability Assessment Shows and How It Can Save You Money
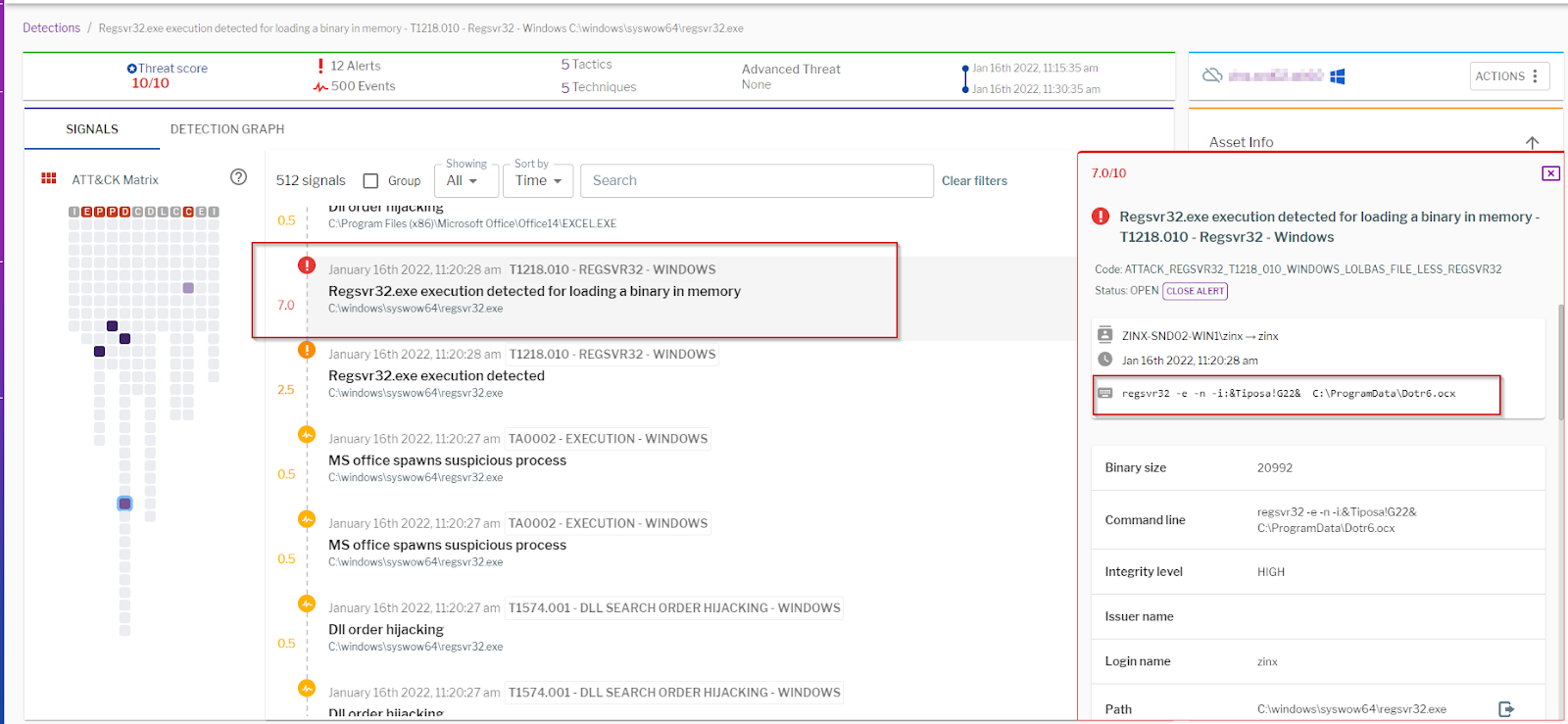
The regsvr32 is a Windows command-line utility used for registering and unregistering OLEs (DLLs and ActiveX controls) in the registry.
The threat actors abuse the utility not for making registry modifications but for loading COM scriptlets from a remote source using DLLs (scrobj.dll).
For this purpose, they use regsvr32 to register OCX files, which are special-purpose software modules that can call ready-made components, such as DLLs.
Also Read: What You Need to Know About Singapore’s Data Sharing Arrangements
This technique is called “Squiblydoo”, and it has been employed in malware-dropping operations since 2017. Back then, ESET researchers first noticed it in a campaign focused on targets in Brazil.
In the currently ongoing campaign, threat actors use Excel, Word, RTF, and composite document files with malicious macros that start the regsvr32 as a child process.
These documents are typically distributed via phishing campaigns, although they can also be dropped through “blind” SEO poisoning attacks.
The above method provides good evasion for the malware payload, because regsvr32 is a Windows tool used for multiple routine operations.
As such, security solutions are less likely to catch the threat and step in to end the infection chain.
Also, using remote COM scriptlets enables the attackers to load fileless malware; and because these payloads run from within the document, the chances to detect them are lower.
To help defenders, Uptyck has shared a list with indicators of compromise that can be used for targeted threat hunting on this GitHub repository.