KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







A new malware campaign on Discord uses the Babadeda crypter to hide malware that targets the crypto, NFT, and DeFi communities.
Babadeda is a crypter used to encrypt and obfuscate malicious payloads in what appear to be harmless application installers or programs.
Starting in May 2021, threat actors have been distributing remote access trojans obfuscated by Babadeda as a legitimate app on crypto-themed Discord channels.
Due to its complex obfuscation, it has a very low AV detection rate, and according to researchers at Morphisec, its infection rates are picking up speed.
The delivery chain begins on public Discord channels enjoying large viewership from a crypto-focused audience, such as new NFT drops or cryptocurrency discussions.
The threat actors post on these channels or send private messages to prospective victims, inviting them to download a game or an app.
In some cases, the actors impersonate existing blockchain software projects like the “Mines of Dalarna” game.
Also Read: The 3 Main Benefits Of PDPA For Your Business
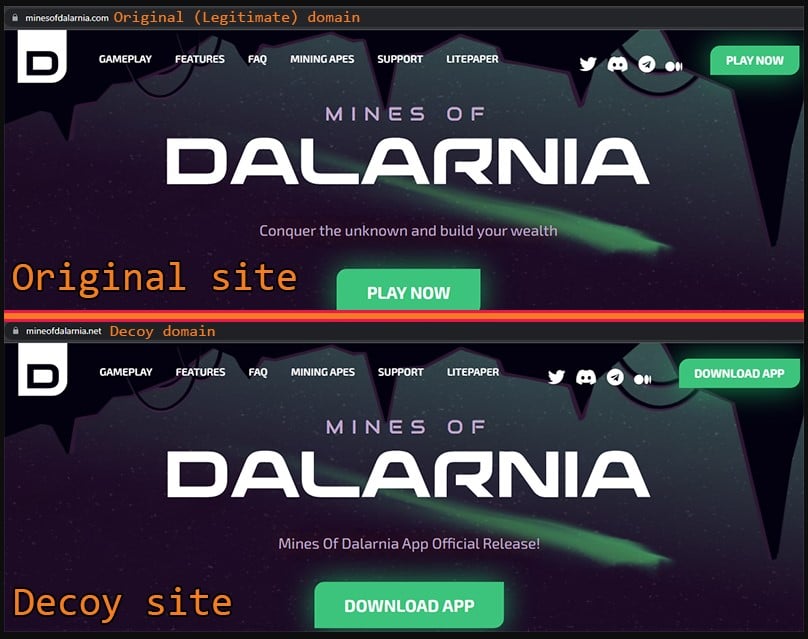
If the user is tricked and clicks on the provided URL, they will end up on a decoy site that uses a cybersquatted domain that is easy to pass as the real one.
These domains use a valid LetsEncrypt certificate and support an HTTPS connection, making it even harder for careless users to spot the fraud.
Other decoy sites used in this campaign are listed below:
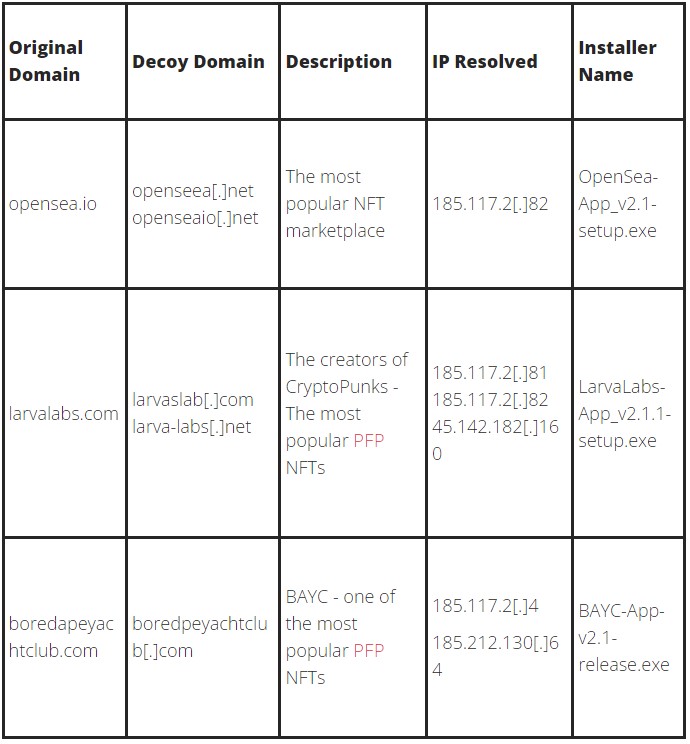
The malware is downloaded upon clicking the “Play Now” or “Download app” buttons on the above sites, hiding in the form of DLLs and EXE files inside an archive that appears like any ordinary app folder at first glance.
If the user attempts to execute the installer, they will receive a fake error message to deceive the victim into thinking that nothing happened.
Also Read: What Do 4 Messaging Apps Get From You? Read The iOS Privacy App Labels
In the background, though, the execution of the malware continues, reading the steps from an XML file to execute new threads and load the DLL that will implement persistence.
This persistence is done through a new startup folder item and the writing of a new registry Run key, both starting crypter’s primary executable.
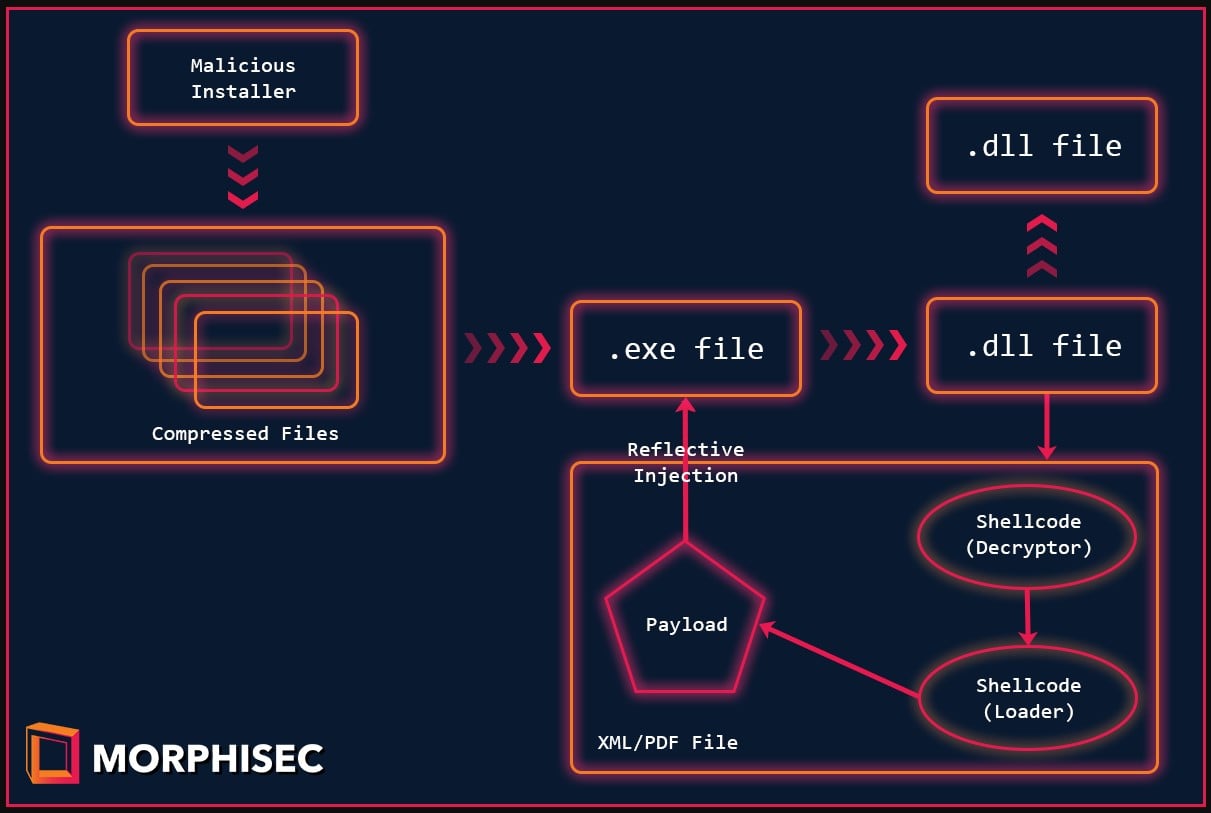
“The executable .text section’s characteristics are configured to RWE (Read-Write-Execute) — that way the actor doesn’t need to use VirtualAlloc or VirtualProtect in order to copy the shellcode and transfer the execution.” – Morphisec
“This helps with evasion since those functions are highly monitored by security solutions. Once the shellcode is copied to the executable, the DLL calls to the shellcode’s entry point (shellcode_address).”
Babadeda has been used in past malware campaigns distributing info-stealers, RATs, and even the LockBit ransomware, but in this specific campaign, Morphisec observed the dropping of Remcos and BitRAT.
Remcos is a widely-abused remote surveillance software that enables attackers to take control of the infected machine and steal account credentials, browser cookies, drop more payloads, etc.
In this case, because the campaign targets members of the crypto community, it is assumed that they are after their wallets, cryptocurrency funds, and NFT assets.