KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







A link-sharing feature in mobile versions of the Apple Safari browser makes it possible for users of iPhone, iPad, and iPod Touch to alter headlines when sharing excerpts from webpages.
A researcher has raised concerns this feature can be abused not only for pulling harmless pranks but for sharing “fake news” having a wider impact.
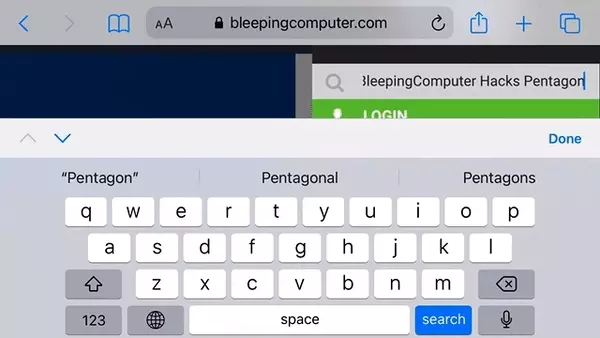
When browsing webpages, such as news articles in the Safari web browser on an iPhone or iPad, users can choose to select and share a partial text excerpt from the page, rather than the entire page itself.
However, the text excerpt can also come from a text input field that the user can control and edit.
When sharing an excerpt from a page with other iPhone users via iMessage, the link preview generated contains the value of this shared text itself, rather than the webpage’s original headline.
In other words, users can type an arbitrary text value in the search bar field of news websites, and then “share” this text value via iMessage.
The link preview generated by iMessage, as shown below, will falsely give off the impression as if that user-generated text is the actual headline of the page.
Also Read: Going Beyond DPO Meaning: Ever Heard of Outsourced DPO?
The behavior can be reproduced specifically when the Apple device is held in landscape orientation and when sharing links via iMessage between iPhone users.
So, sharing content in this manner from iPhone to Android would not result in this behavior.
This “prank” was previously reported by MacRumours in 2019 who had also pointed out there were some legitimate use-cases of this feature.
“It’s actually a useful feature that’s great for pointing out specific passages in blogs, news articles, and more,” Juli Clover, the website’s editor had said earlier.
But Josh Long who is the Chief Security Analyst at Intego believes beyond harmless pranks, this feature can have a wider impact if abused to spread false information.
“Currently there is nothing to prevent a user from typing a misleading headline or other deceptive text into a field and making it part of the page preview,” explained Long in Intego’s blog post from 2019.
“While MacRumors calls the flaw ‘fun’ and notes that it can easily be exploited as a prank, we feel that all iMessage users should take caution, as the flaw could also potentially be used in more sinister attacks, for example as a means to try to get financial investors to buy or sell stocks in a panic based on false headlines.”
Intego’s follow-up report to the 2019 one had been released end of October 2020, just in time for U.S. Presidential Election when much scrutiny surrounded “fake news” and the negative impact it can have on the democratic process.
Although findings related to this issue were made public as early as 2019, the latest Apple iOS devices continue to ship with this feature enabled.
Long tells BleepingComputer he has tested the latest versions of iOS released this month but the feature, or rather the problem continues to persist.
“I am still able to reproduce this in the final (public) release of iOS 14.2, which was released nearly a week after I reminded Apple’s security team about the problem.”
“I also confirmed that iOS 12.4.9, released the same day, is also still affected,” Long told BleepingComputer.
In a timeline shared by Long with us, since Intego’s 2019 blog post (linked above) had warned how this feature could be abused for stock manipulation scams, more than a year went by.
Last month, Intego contacted Apple to inquire if the issue would be fixed but did not hear back.
Also Read: Limiting Location Data Exposure: 8 Best Practices
Consequently, Intego released a follow-up blog post warning everyone the feature could be abused for election interference by spreading “fake news” headlines.
On November 5th, Apple released iOS 14.2, iPadOS 14.2, and iOS 12.4.9, none of which resolved the bug.
We are not aware if this feature has indeed been exploited on a large scale to conduct activities such as stock manipulation or election interference, but that is not to say concerns raised by Intego should be overlooked.
BleepingComputer reached out to Apple for comment on this issue but we have not heard back yet.
For those interested in testing this feature out themselves, a detailed PoC video is available on YouTube.