KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







A publicly exposed cloud storage bucket was found to contain images of hundreds of passports and identity documents belonging to journalists and volleyball players from around the world.
These sensitive documents were hosted on a Microsoft Azure blob storage share that was publicly accessible to anyone.
Further investigation by BleepingComputer revealed that the source of the leak was Confédération Européenne de Volleyball (CEV), or European Volleyball Confederation.
In November 2020, cyber threat intelligence researcher Bob Diachenko came across a publicly exposed online Azure storage blob that contained hundreds of image scans showing passports and identity documents.
On researching the names present on these ID documents, Diachenko could identify prominent journalists and media representatives who had likely submitted these scans as a part of some “accreditation” process.
Also Read: 5 Common Sections in an Agreement Form Example
BleepingComputer reached out to Diachenko and learned that the location of the exposed storage share was: accreditationstorage.blob.core.windows.net/backup/.
This URL contained thousands of headshot images of volleyball players from Europe, Russia, and other countries in both the ‘backup‘ directory and an ‘AccreditationPhotos‘ subfolder.
Also present in the backup directory was a documents folder that contained scans of passports, driver licenses, and identity documents belonging to sports journalists and volleyball players.
Links to these images were soon indexed by GrayhatWarfare, a search engine that captures publicly visible buckets.
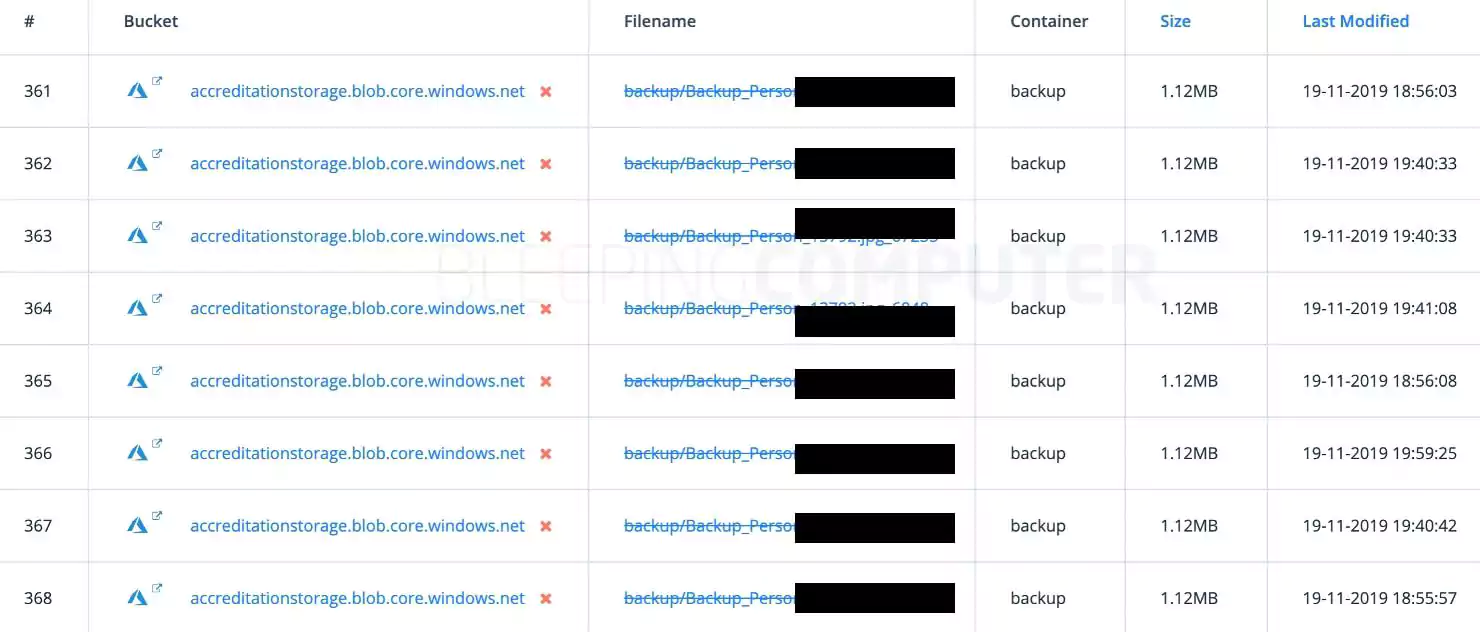
BleepingComputer analyzed hundreds of files present within these directories, including the exposed player headshots and identity documents.
Reverse-image searches for headshots revealed that these well-known European volleyball players were either directly associated with CEV or were part of a volleyball team or federation affiliated with the CEV.
BleepingComputer also found some of CEV’s assets in the bucket, such as branding images with CEV logos on them.
Further, to confirm our findings, we contacted multiple journalists and sportspeople whose identity documents were being exposed online on this Azure blob.
In all cases, BleepingComputer received a positive affirmation from the media representatives and sportspeople that they had indeed submitted their documents to CEV.
“I get my credentials for covering Volley Ball Olympic game qualifications with CEV,” Ludovic Piedtenu, a correspondent of Radio France in Germany, told BleepingComputer.
On seeing the image of the scan, Piedtenu confirmed that it was indeed a copy of his passport that he had submitted to CEV to get his press credentials so he could cover games in Berlin between January 5th and January 10th, 2020.
Also Read: Limiting Location Data Exposure: 8 Best Practices
“Indeed I was accredited in some CEV events, most recently in January in Berlin for Olympic volleyball qualification and as far as I remember I had to provide details of my ID in order to get the accreditation card,” Tomas Kohlmann, a Czech Republic-based sports reporter told BleepingComputer.
“I didn’t give my passport to anyone. Only the CEV and the embassies of [Schengen countries],” a third source told BleepingComputer.
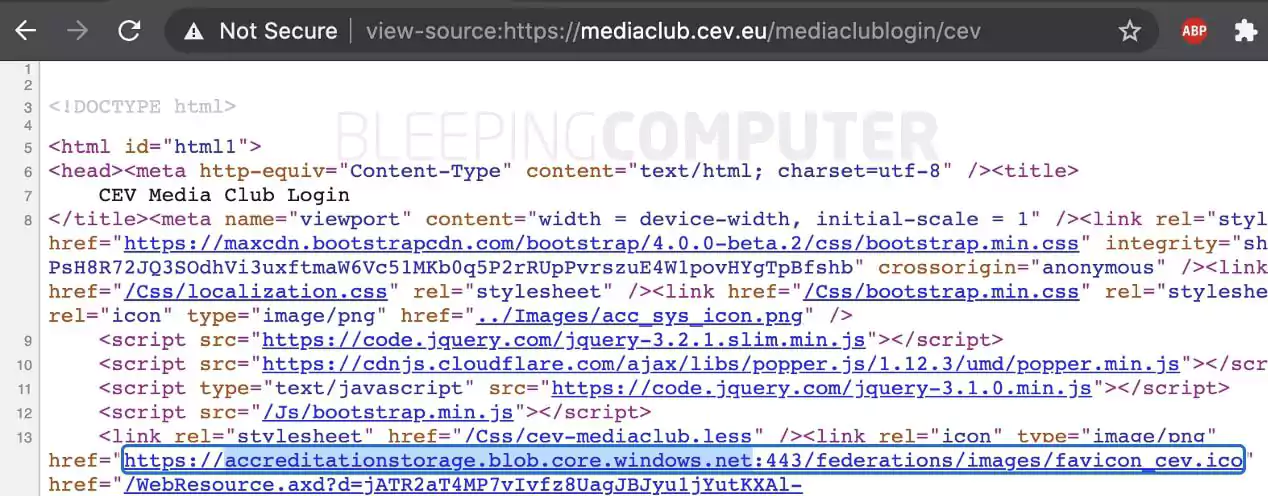
CEV does have an online Media Club accreditation system, which enables media representatives and journalists to register and upload their identity documents for verification.
On reviewing the HTML source code of CEV’s Media Club Accreditation System webpages, BleepingComputer noticed links to the exposed accreditationstorage blob were present on these pages, further confirming the bucket was indeed linked to CEV [1, 2].
After having sufficient confirmation that the publicly exposed “backup” storage bucket was linked to CEV, BleepingComputer reached out to CEV multiple times to report the leak.
BleepingComputer firstreached out to CEV on November 24th, 2020 (the same day of Diachenko’s tweet) via email and on their “out of hours” press helpline, but we did not hear back.
We tried contacting CEV the following day but still did not hear back.
Through December, we continued to reach out to different CEV departments, key personnel via email and LinkedIn, and former employees to inform the organization about the leak without any success.
Finally, on December 11th, we received an acknowledgment from CEV’s legal department that they were investigating the issue, but within five minutes, the sender had recalled their message.
It remains unclear when and how the publicly exposed bucket closed, but as of January 29th, 2021, the links within the backup folder are no longer accessible, as observed by BleepingComputer.
Further, attempting to navigate to accreditationstorage.blob.core.windows.net via the Microsoft Azure Storage Explorer application now throws an authentication error, “Server failed to authenticate the request. Please refer to the information in the www-authenticate header.”
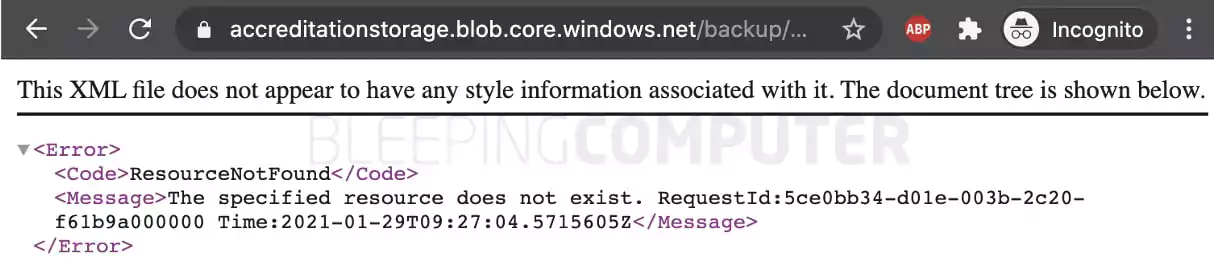
All of this indicates the bucket and the sensitive files contained were secured and are no longer publicly accessible.
However, cases of exposed cloud storage buckets leaking sensitive data have occurred time and time again.
Last year, another unsecured Azure blob belonging to a Cayman Islands investment firm exposed identity and financial documents.
In late 2019, BleepingComputer reported millions of Lion Air passenger records being exposed through buckets were exchanged on forums.
When storing sensitive data and backups in cloud storage buckets and blobs, it is mandatory that proper permissions be configured and to cross-check if these assets could be accessed publicly.