KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!





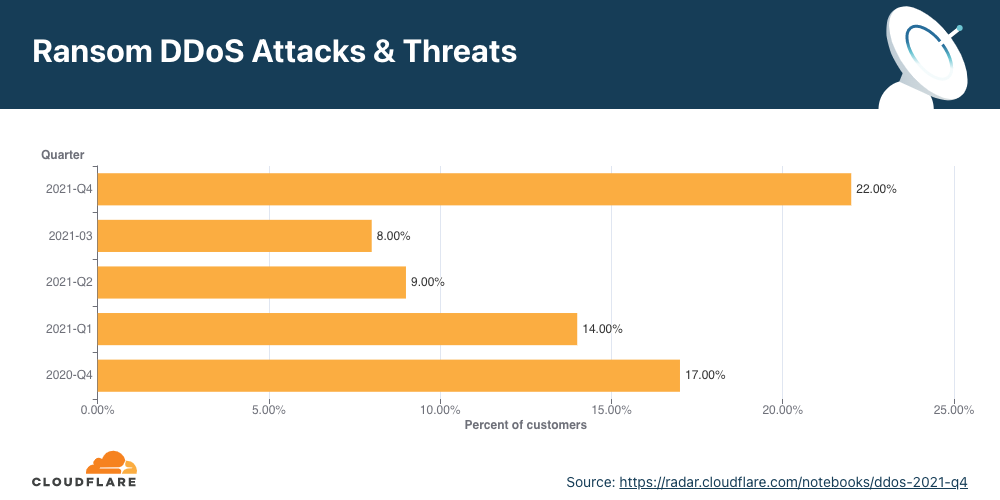
The end of 2021 saw a rise in the number of distributed denial-of-service incidents that came with a ransom demand from the attackers to stop the assault.
In the fourth quarter of last year, about a quarter of Cloudflare’s customers that were the target of a DDoS attack said that they received a ransom note from the perpetrator.
A large portion of these attacks occurred in December 2021, when almost a third of Cloudflare customers reported receiving a ransom letter.
By comparison with the previous month, the number of reported DDoS ransom attacks was double, Cloudflare says in a blog post today.
Also Read: The Competency Framework: A Guide for Managers and Staff
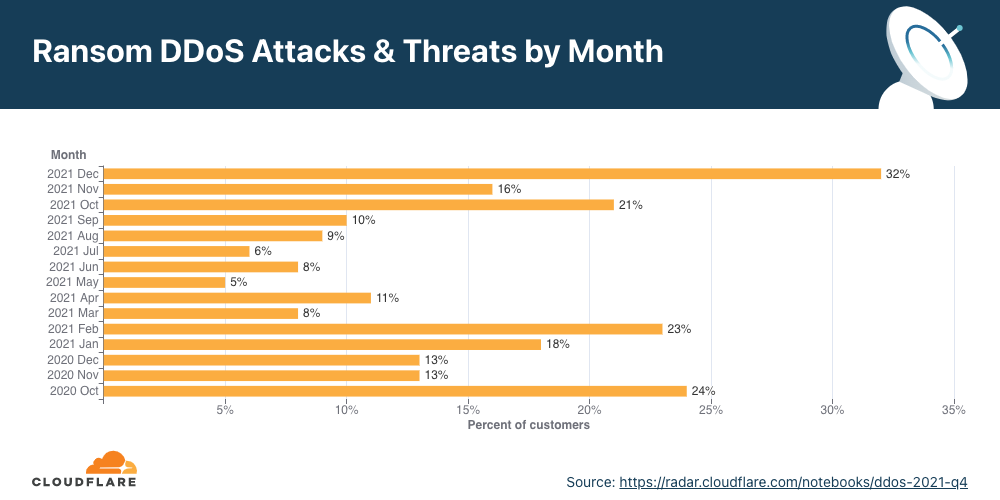
According to the company, 2021 is when most of these attacks happened, with a 29% recorded year-over-year increase and a 175% quarter-over-quarter jump.
Extortion or ransom DDoS (RDDoS) attacks started to become a new threat in August 2020 and grew bigger and more complex since then.
They started around 200Gbps and then flexed to more than 500Gbps in mid-September. In February 2021, internet security services company Akamai saw its share of a challenge dealing with an 800Gbps RDDoS that targeted a gambling company in Europe.
Last September, a threat actor deployed an RDDoS against VoIP.ms voice-over-Internet provider, disrupting phone services as the company’s DNS servers became unreachable.
Cloudflare says that application-layer DDoS attacks, HTTP DDoS ones in particular, targeted manufacturing companies and saw a spike of 641% compared to the third quarter of 2021.
Looking at the IP addresses, most of these DDoS incidents originate from China, the U.S., Brazil, and India, deployed by botnets such as Meris, which emerged this year with a record-breaking assault of 21.8 million requests against Russian internet giant Yandex.
Unlike an application-layer DDoS, which denies users access to a service, a network-layer DDoS attack targets the entire network infrastructure of a company trying to take down routers and servers.
One of the largest DDoS attacks that Cloudflare mitigated lasted for 60 seconds and came from a botnet with 15,000 systems that hurled close to 2Tbps of junk packets at a customer.
Also Read: Personal Data Protection Act Australia
While this is not the largest DDoS attack recorded to date, “terabit-strong attacks are becoming the norm,” Cloudflare says. This one was deployed from a network of IoT devices running compromised by a variant of the Mirai botnet.
Cloudflare notes that SYN floods remain a popular attack method. The SNMP protocol has seen a dramatic spike of almost 6,000% from one quarter to another, although UDP-based DDoS attacks were the second most used vector.
“When we look at emerging attack vectors — which helps us understand what new vectors attackers are deploying to launch attacks — we observe a massive spike in SNMP, MSSQL, and generic UDP-based DDoS attacks” – Cloudflare
Companies dealing with short-lived DDoS attacks, which are more frequent, should turn to an automated mitigation solution because it acts on the spot and stops the assault on the spot.