KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







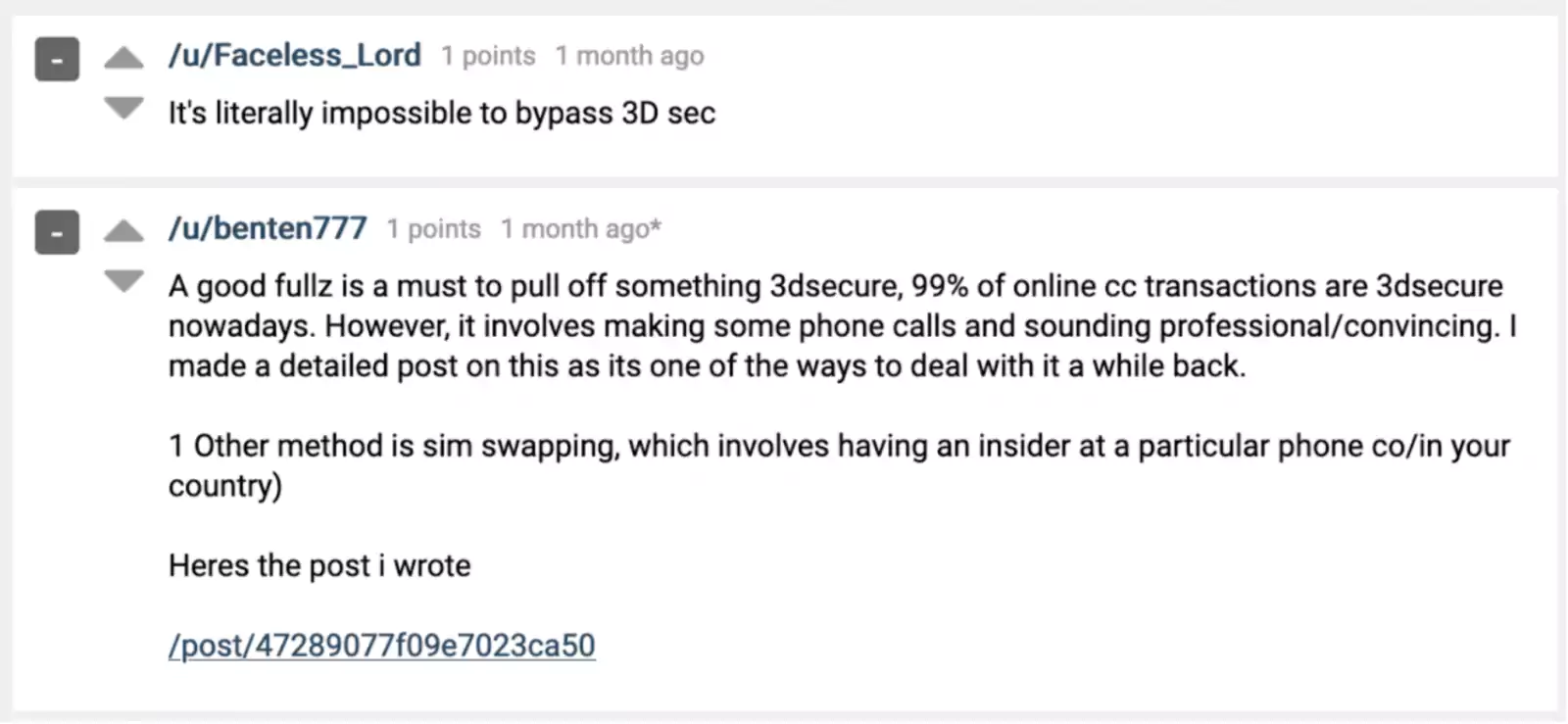
Cybercriminals are constantly exploring and documenting new ways to go around the 3D Secure (3DS) protocol used for authorizing online card transactions.
Discussions on underground forums offer advice on how to bypass the latest variant of the security feature by combining social engineering with phishing attacks.
Individuals on multiple dark-web forums are sharing their knowledge on making fraudulent purchases on shops that implemented 3DS to protect customer transactions.
3DS adds a layer of security for online purchases using credit or debit cards. It requires direct confirmation from the card owner to authorize a payment.
The feature evolved from the first version where the bank asked the user for a code or a static password to approve the transaction. In the second version (3DS 2), designed for smartphones, users can confirm their purchase by authenticating in their banking app using their biometric data (fingerprint, face recognition).
Also Read: How Formidable is Singapore Cybersecurity Masterplan 2020?
Despite the advanced security features that 3DS 2 provides, the first version is still widely deployed, giving cybercriminals a chance to use their social engineering skills and trick users into giving the code or password to approve the transaction.
In a blog post today, analysts at threat intelligence company Gemini Advisory share some of the methods cybercriminals discuss on dark-web forums to make fraudulent purchases at online stores that implemented 3DS.
It all starts with full cardholder information, which includes at least the name, phone number, email address, physical address, mother’s maiden name, ID number, and driver’s license number.
Cybercriminals use these details to impersonate a bank employee calling the customer to confirm their identity. By offering some personally identifiable information, they gain the victim’s trust and request their password or code to complete the process.
The same tactic could work on later 3DS variants and make purchases in real-time. A hacker described the method in a post on a top-tier underground forum.
Using full cardholder details, a voice changer, and a phone number spoofing app, the fraudster can initiate a purchase at a site and then call the victim to elicit the needed information.
“In the final step, the hacker advises the victim that they will receive a confirmation code for final identity verification, at which point the cybercriminal should place the order at the shop; when prompted to enter verification code that was sent to the victim’s phone, the fraudster should retrieve that code from the victim” Gemini Advisory
Getting the 3DS code is possible through other means, like phishing and injects. When the victim makes a purchase on the phishing site, the criminals pass all the details to the legitimate store to get their product.
According to Gemini Advisory’s findings, some cybercriminals also add stolen credit card data to a PayPal account and use it as a payment method.
Another method is classic and involves compromising a victim’s phone with malware that can intercept the security code and pass it to the fraudster.
Alternatively, many stores do not ask for the 3DS code when transactions are below a certain limit, allowing fraudsters to get away with making multiple smaller purchases.
Also Read: Going Beyond DPO Meaning: Ever Heard of Outsourced DPO?
Most of these techniques work where earlier versions of 3DS are present. With 3DS 2 still a long way from being widely adopted. Europe is leading the transition to the more secure standard (PSD2 regulation – strong customer authentication fulfilled with 3DS 2), while in the U.S. the fraud liability protection for merchants using 3DS 1 expires on October 17, 2021.
However, Gemini Advisory believes that cybercriminals will also take a stab at the more secure 3DS 2 through social engineering.