KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







A newly discovered cyberespionage group has been targeting hotels worldwide around the world since at least 2019, as well as higher-profile targets such as governments, international organizations, law firms, and engineering companies.
Slovakian internet security firm ESET spotted the hacking group (dubbed FamousSparrow) and described it as an “advanced persistent threat.”
The cyberspies have targeted victims from all over Europe (France, Lithuania, the UK), the Middle East (Israel, Saudi Arabia), the Americas (Brazil, Canada, Guatemala), Asia (Taiwan), and Africa (Burkina Faso) in attacks spanning the last two years.
Also Read: 10 Principles On How To Build A Good Governance Model
“The targeting, which includes governments worldwide, suggests that FamousSparrow’s intent is espionage,” ESET researchers Matthieu Faou and Tahseen Bin Taj said.
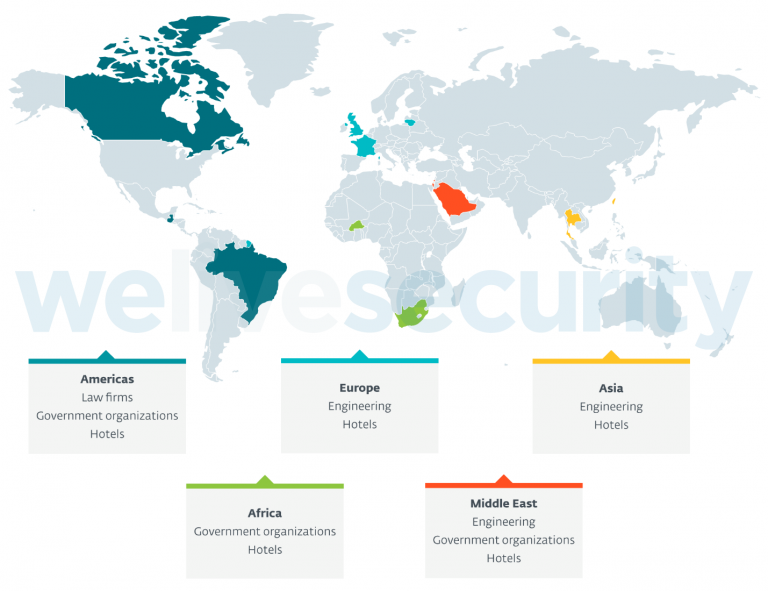
The group has used multiple attack vectors in Internet-exposed web applications to breach its targets’ networks, including remote code execution vulnerabilities in Microsoft SharePoint, the Oracle Opera hotel management software, and the Microsoft Exchange security flaws known as ProxyLogon.
After breaching their victims’ networks, the group deployed custom tools such as a Mimikatz variant, a small tool designed to harvest memory contents (such as credentials) by dumping the Windows LSASS process, and a backdoor known as SparrowDoor only used by FamousSparrow.
“FamousSparrow is currently the only user of a custom backdoor that we discovered in the investigation and called SparrowDoor. The group also uses two custom versions of Mimikatz,” Bin Taj explained.
Also Read: The Importance Of DPIA And Its 3 Types Of Processing
“The presence of any of these custom malicious tools could be used to connect incidents to FamousSparrow.”
The espionage group also started targeting Microsoft Exchange servers not patched against the ProxyLogon vulnerabilities in March 2021, one day after Microsoft fixed the bugs.
ESET also shared info on at least ten hacking groups actively abusing these bugs after joining the March Microsoft Exchange attack frenzy.
According to reports from other security firms, in-the-wild exploitation began on January 3rd, way before the bugs were even reported to Microsoft, who released patches on March 2nd.
After scanning roughly 250,000 Internet-exposed Exchange servers worldwide in March, the Dutch Institute for Vulnerability Disclosure (DIVD) found 46,000 servers unpatched against the ProxyLogon vulnerabilities.
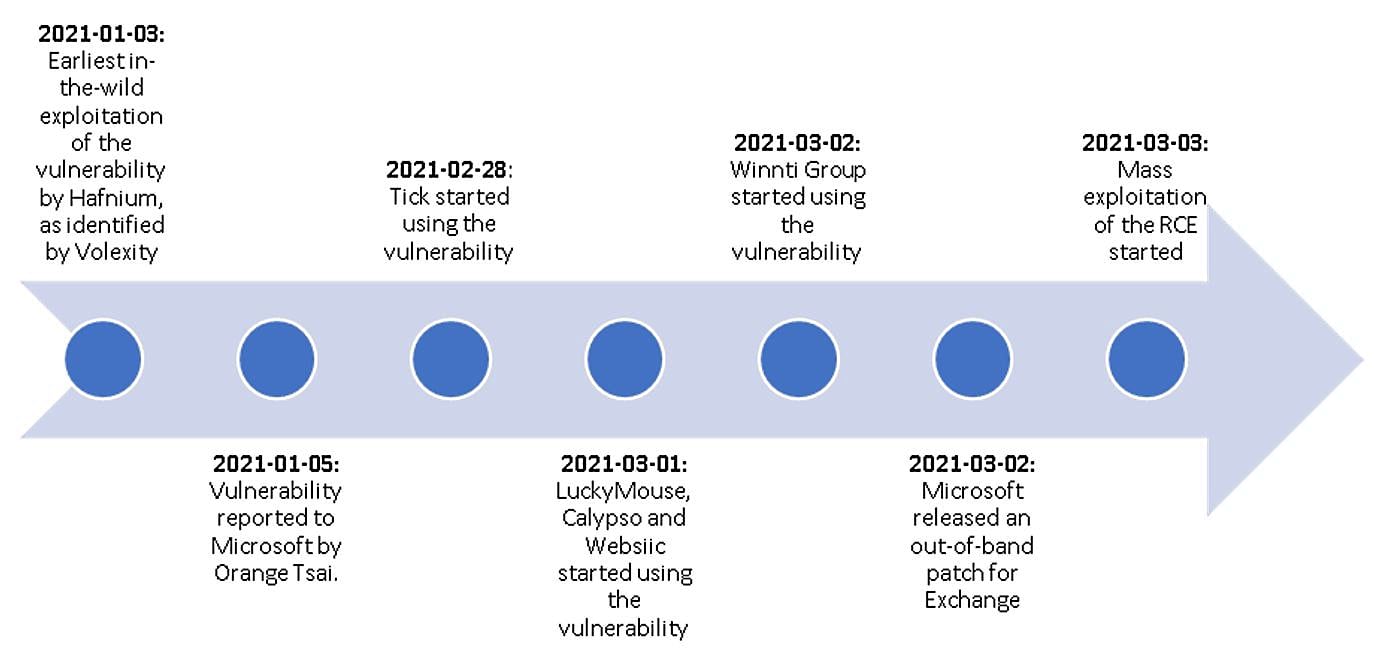
ESET also found some links to other known APT groups, including malware variants and configurations connected. SparklingGoblin and DRBControl.
However, as the researchers said, FamousSparrow is considered a separate entity that likely leveraged its access into compromised hotels’ systems for espionage purposes, including keeping track of specific high-profile targets.
“FamousSparrow is yet another APT group that had access to the ProxyLogon remote code execution vulnerability early in March 2021. It has a history of leveraging known vulnerabilities in server applications such as SharePoint and Oracle Opera,” the ESET researchers concluded.
“This is another reminder that it is critical to patch internet-facing applications quickly, or, if quick patching is not possible, to not expose them to the internet at all.”