KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







More than 500,000 Huawei users have downloaded from the company’s official Android store applications infected with Joker malware that subscribes to premium mobile services.
Researchers found ten seemingly harmless apps in AppGallery that contained code for connecting to malicious command and control server to receive configurations and additional components.
A report from antivirus maker Doctor Web notes that the malicious apps retained their advertised functionality but downloaded components that subscribed users to premium mobile services.
To keep users in the dark the infected apps requested access to notifications, which allowed them to intercept confirmation codes delivered over SMS by the subscription service.
According to the researchers, the malware could subscribe a user to a maximum of five services, although the threat actor could modify this limitation at any time.
The list of malicious applications included virtual keyboards, a camera app, a launcher, an online messenger, a sticker collection, coloring programs, and a game.
Also Read: 3 Reasons Why You Must Take A PDPA Singapore Course
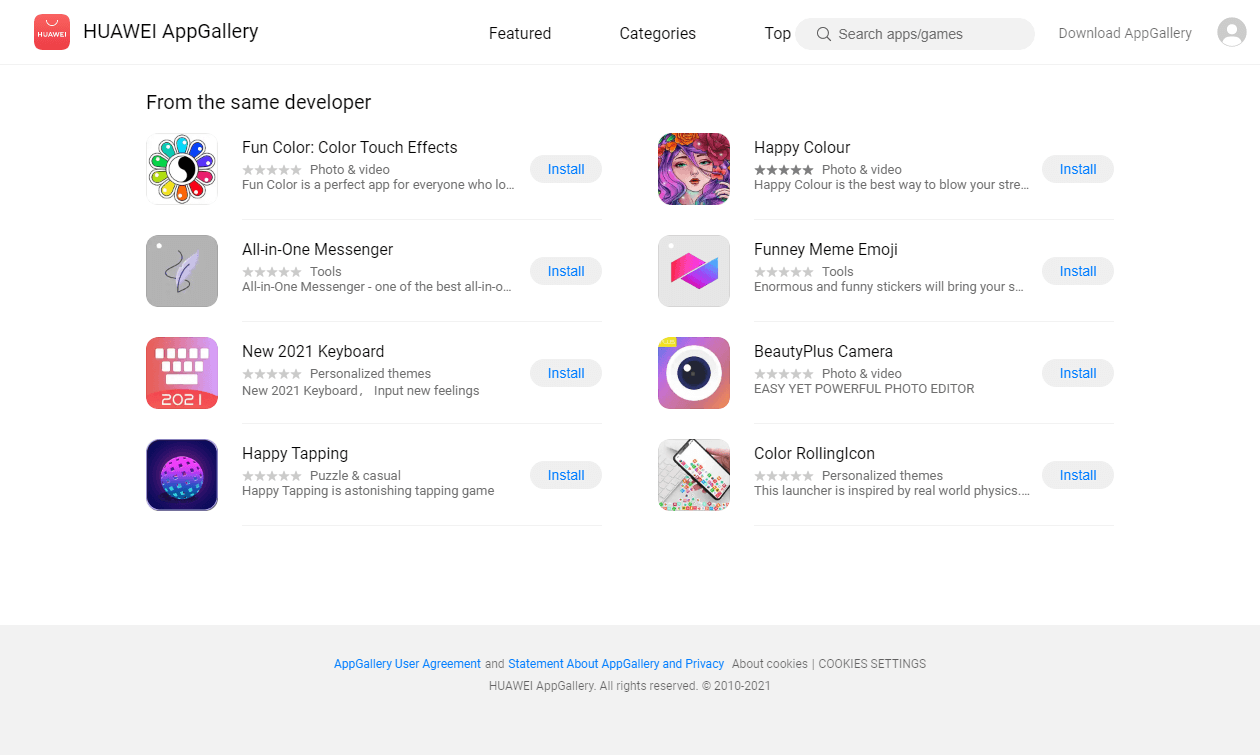
Most of them came from one developer (Shanxi Kuailaipai Network Technology Co., Ltd.) and two from a different one. These ten apps were downloaded by more than 538,000 Huawei users, Doctor Web says.
Doctor Web informed Huawei of these apps and the company removed them from AppGallery. While new users can no longer download them, those that already have the apps running on their devices need to run a manual cleanup. The table below lists the name name of the application and its package:
| Application name | Package name |
| Super Keyboard | com.nova.superkeyboard |
| Happy Colour | com.colour.syuhgbvcff |
| Fun Color | com.funcolor.toucheffects |
| New 2021 Keyboard | com.newyear.onekeyboard |
| Camera MX – Photo Video Camera | com.sdkfj.uhbnji.dsfeff |
| BeautyPlus Camera | com.beautyplus.excetwa.camera |
| Color RollingIcon | com.hwcolor.jinbao.rollingicon |
| Funney Meme Emoji | com.meme.rouijhhkl |
| Happy Tapping | com.tap.tap.duedd |
| All-in-One Messenger | com.messenger.sjdoifo |
The researchers say that the same modules downloaded by the infected apps in AppGallery were also present in other apps on Google Play, used by other versions of Joker malware. The full list of indicators of compromise is available here.
Once active, the malware communicates to its remote server to get the configuration file, which contains a list of tasks, websites for premium services, JavaScript that mimics user interaction.
Joker malware’s history goes as far back as 2017 and constantly found its way in apps distributed through Google Play store. In October 2019, Tatyana Shishkova, Android malware analyst at Kaspersky, tweeted about more than 70 compromised apps that had made it into the official store.
And the reports about the malware in Google Play kept coming. In early 2020, Google announced that since 2017, it had removed about 1,700 apps infected with Joker.
Also Read: What You Should Know About The Data Protection Obligation Singapore
Last February, Joker was still present in the store and it continued to slip past Google’s defenses even in July last year.