KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Security researchers analyzing multiple sets of malicious emails believe they uncovered activity belonging to a previously unidentified actor that fits the description of an advanced persistent threat (APT).
The actor received the name LazyScripter and has been active since 2018, using phishing to target individuals seeking immigration to Canada for a job, airlines, and the International Air Transport Association (IATA).
The infrastructure supporting this long-term campaign is still active and the actor continues to evolve by updating its toolsets.
LazyScripter’s latest activity involves the use of the freely available Octopus and Koadic malware. Both were delivered through malicious documents and ZIP archives that contained embedded objects (VBScript or batch files) and not macro code commonly seen in phishing attacks.
Also Read: The 3 Main Benefits Of PDPA For Your Business
The researchers from Malwarebytes also found other examples where the attacker dropped other remote access trojans (RATs) that are common to multiple hacking groups: LuminosityLink, RMS, Quasar, njRat, and Remcos.
According to the researchers, LazyScripter switched to the double-RAT tactic after initially using the PowerShell Empire post-exploitation framework. The researchers named the loaders for these payloads KOCTOPUS and Empoder, respectively.
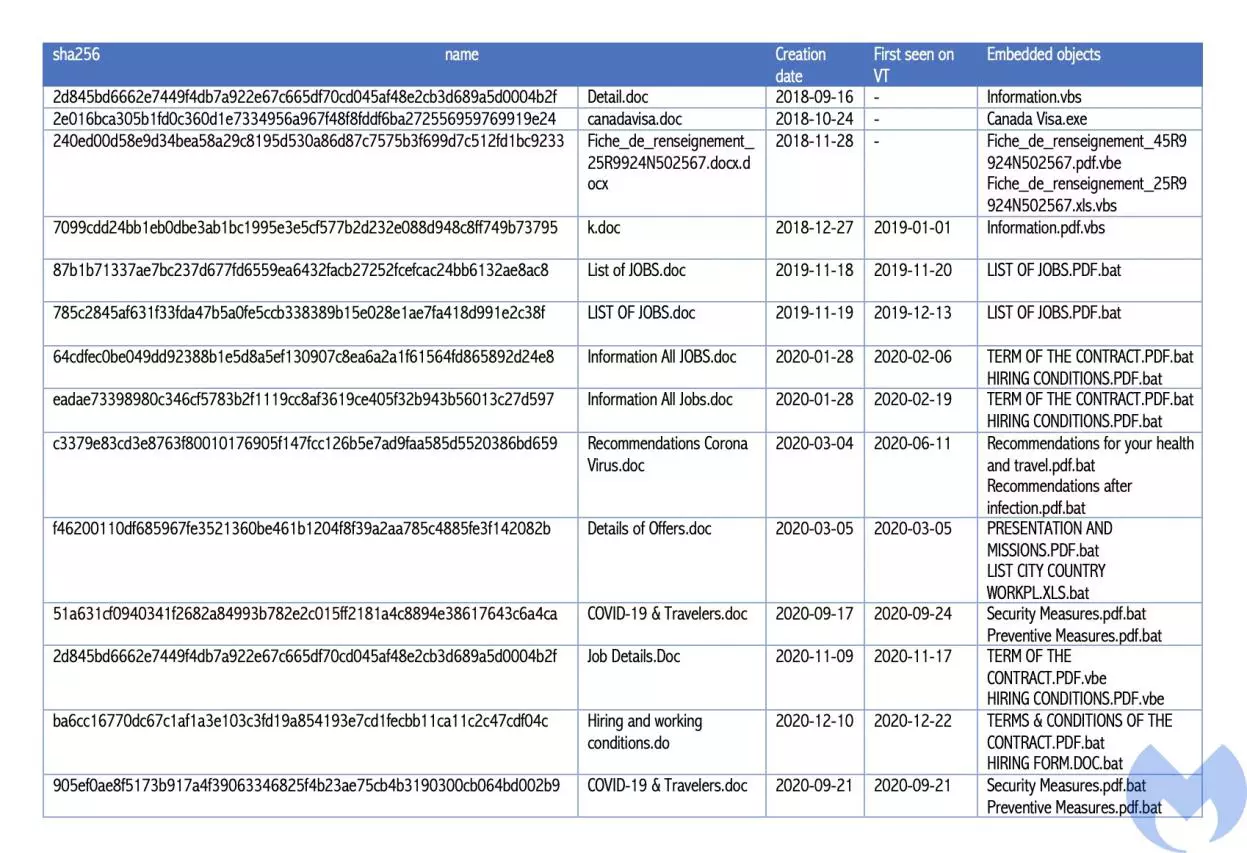
Typically, the malicious documents come with one or two embedded objects with icons pretending to be PDF, Microsoft Word/Excel files; they are, in fact, batch, executable, or VBScript variants of the KOCTOPUS and Empoder loaders.
Used to deploy Octopus and Koadic and ensure their persistence on the system, KOCTOPUS is highly obfuscated using the BatchEncryption tool.
The overall compromise process via KOCTOPUS involves bypassing the User Account Control (UAC) security feature in Windows, disabling Microsoft security products, and downloading RMS or LuminosityLink RAT.
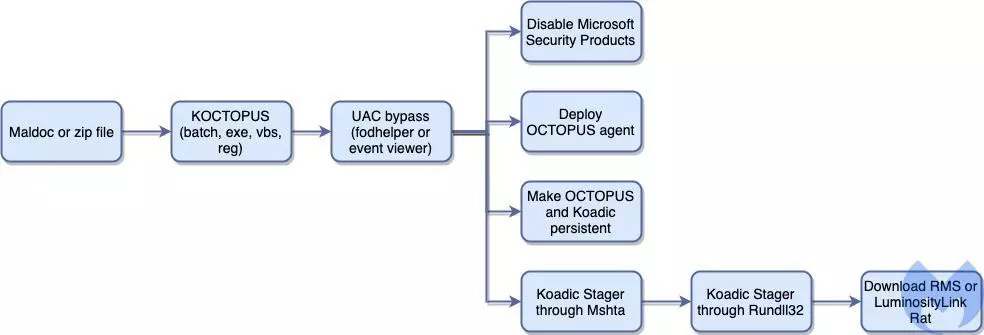
Interestingly, LazyScripter hosted their toolsets on GitHub, a tactic used in the past by an APT group associated with Iran.
Malwarebytes found three accounts linked to LazyScripter. Two of them – LIZySARA and Axella49 – have been deleted in January but a third one (OB2021) emerged at the beginning of the month, on February 2, and is still active.
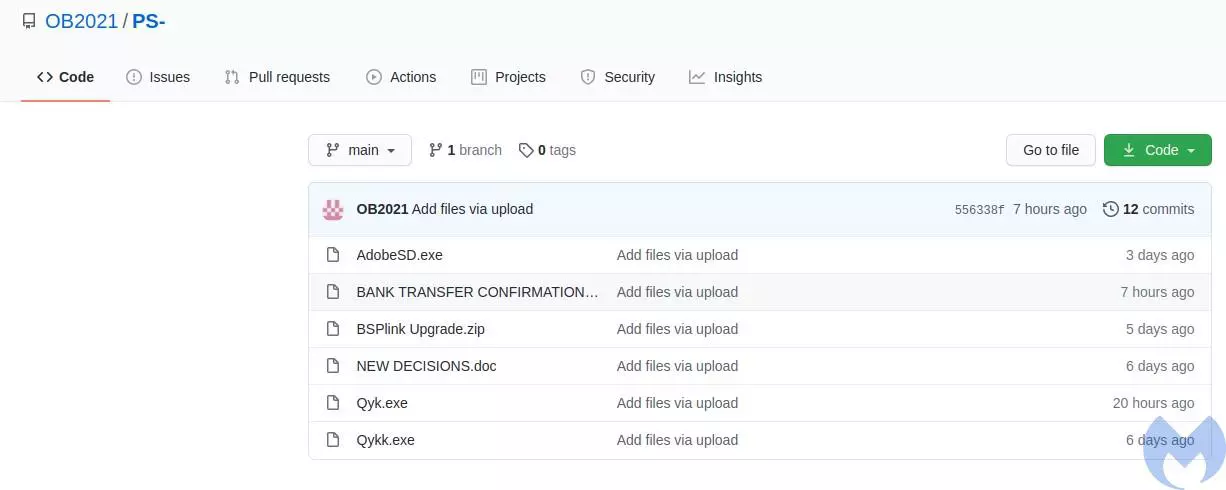
Some of the email lures appear to be specifically designed for airlines that use the BSPLink software, IATA’s solution for its Billing and Settlement Plan (BSP), which allows companies to:
The lure changed recently, “to mimic a new feature recently introduced by IATA called IATA ONE ID (Contactless Passenger Processing tool),” Malwarebytes says in a detailed technical report today.
The company adds that this is an indication that the threat actor is adapting its toolset to target new systems developed by IATA. LazyScripter’s wider collection of lures includes the following:
IATA security (International Air Transport Association security)
• BSPlink Updater or Upgrade (BSPlink is the global interface for travel agents and airlines to access the IATA BSP)
• IATA ONE ID
• User support kits for IATA users
• Tourism (UNWTO)
• COVID-19
• Microsoft Updates
• Job information
• Canada skill worker program
• Canada Visa (CanadaVisa.com is the online presence of the Campbell Cohen Immigration Law Firm)
Also Read: What Do 4 Messaging Apps Get From You? Read The iOS Privacy App Labels
A timeline of LazyScripter’s phishing activity based on the various lures they used is available below:
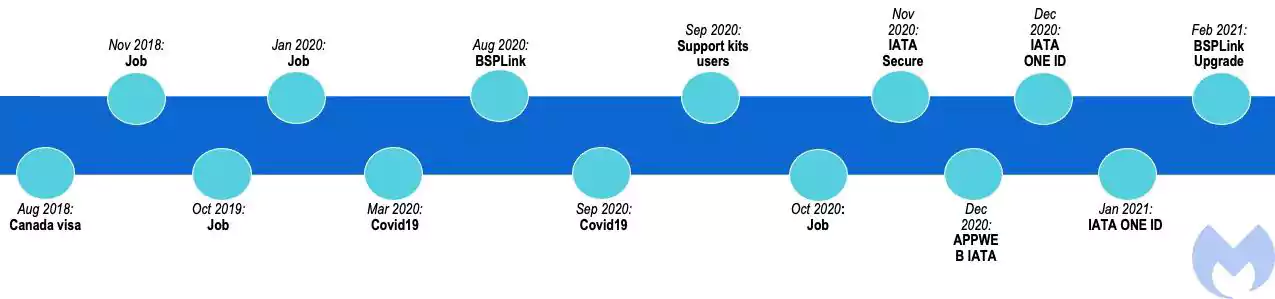
For command and control (C2) communications, LazyScripter leverages five subdomains on four different shared domains hosted by free dynamic DNS providers Duck DNS and FreeDNS:
By using open-source post-exploitation tools and malware that is widely used in hacking activities by multiple actors, LazyScripter leaves few clues regarding attribution.
However, Malwarebytes notes that public research shows only two threat actors that have used the Koadic penetration testing tool in their campaigns: the Iranian-linked MuddyWater and the Russian APT28 (Fancy Bear/Sofacy/Strontium/Sednit).
The company says that they did not find a connection with APT28 but noticed similarities with MuddyWater in that their past campaigns used both Koadic and PowerShell Empire, and relied on GitHub to host their malicious toolset.
There are some aspects, though, that do not permit high-confidence attribution and prompted Malwarebytes to label LazyScripter as a new APT group: